Our security operations team investigate and mitigate multiple denial-of-service (DDoS) attacks every single day. One recent case caught our attention because of the intensity and duration of the attack and – as we discovered through some research – how it was being done. In this article, we’ll share the specifics in an effort to track down the vulnerable devices and to help get them patched.
DDoS Against a Small Business
It all started with a small brick and mortar jewelry shop that signed up with us to help protect their site from a DDoS that had taken them down for days. By switching their DNS to the Sucuri Network, we were able to quickly mitigate the attack for them. It was a layer 7 attack (HTTP Flood) generating close to 35,000 HTTP requests per second (RPS) which was more than their web servers could handle.
Normally, this would be the end of the story. The attack would be mitigated, the attackers would move on after a few hours, and the website owner would be happy. In this case, however, after the site came back up, the attacks increased their intensity, peaking to almost 50,000 HTTP requests per second. It continued for hours, which turned into days.
Since this type of long duration DDoS is not so common, we decided to dive into what the attackers were doing. To our surprise, they were leveraging only IoT (Internet of Things) CCTV devices as the source of their attack botnet.
CCTV-Based DDoS
It is not new that attackers have been using IoT devices to start their DDoS campaigns, however, we have not analyzed one that leveraged only CCTV devices and was still able to generate this quantity of requests for so long.
As we extracted the geolocation from the IP addresses generating the DDoS, we noticed that they were coming from all over the world in different countries and networks. A total of 25,513 unique IP addresses came within a couple of hours.
The source of the attack concentrated in Taiwan, with 24% of the IP addresses, followed by the USA with 12%, Indonesia with 9%, Mexico with 8%, and Malaysia with 6%. The top 10 countries with the most compromised CCTV devices used in this attack were:
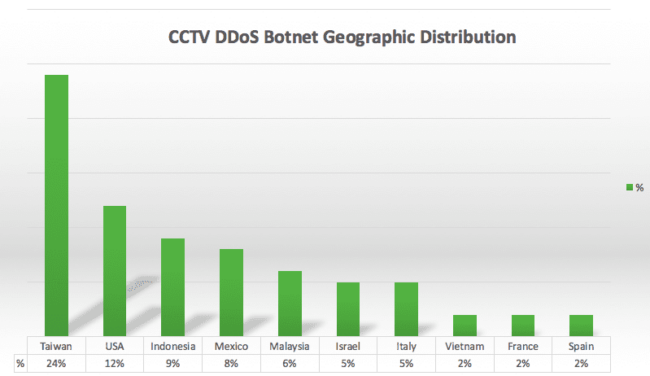
These top 10 countries only accounted for 75% of the locations, and the other 25% were spread to another 95 countries (105 in total).
When we look at the networks, the top ASNs matched the countries pretty closely:
HINET Data Communication Business Group Uninet S.A. de C.V. TMNET-AS-AP TM Net BSNL-NIB National Internet Backbone AIRTELBROADBAND-AS-AP Bharti Airtel Ltd. ATT-INTERNET4 - AT&T Services COMCAST-7922 - Comcast Cable Communications ASN-IBSNAZ TE-AS TE-AS TELEFONICA_DE_ESPANA
We already started to reach out to some ASNs and provide the IP addresses affected. If you manage an ASN, please contact us and we will provide a list of IP addresses compromised within your network.
As far as country visualization, this is the plot of the IP addresses across the world:
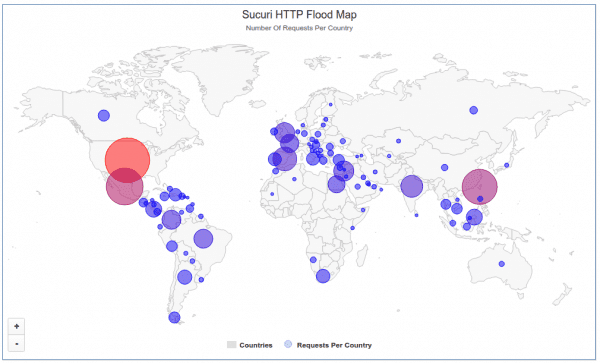
Compromised CCTV Devices – 25,000 of them
As we dug deeper into each of these IP addresses, we learned that all of them were running the “Cross Web Server” and had a similar default HTTP page with the “DVR Components” title.
$ curl -sD - 122.116.xx.xx | head -n 10 HTTP/1.1 200 OK Server:Cross Web Server Content-length: 3233 Content-type: text/html <title>DVR Components Download</title>
This is what raised our suspicions of an IoT botnet that was leveraging some CCTVs as part of the attack. As we kept looking, we found the company logos from the resellers and manufactures on all IP addresses.
These were the companies with the most market share:
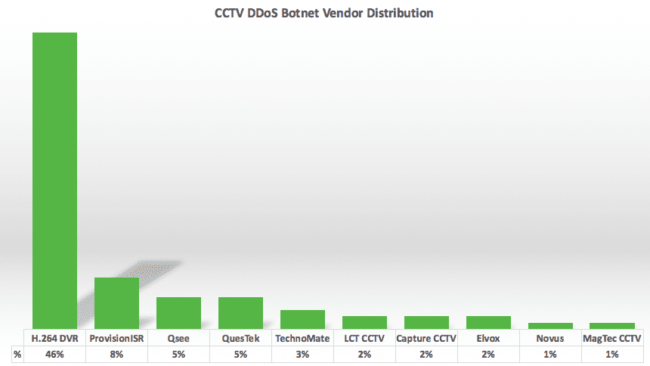
46% H.264 DVR 8% ProvisionISR 5% QSee 5% QuesTek 3% TechnoMate 2% LCT CCTV 2% Capture CCTV 2% Elvox 1% Novus 1% MagTec CCTV
As you can see, the majority had the default H.264 DVR logos, but the others had modified branding to match the company that built or sold it. All these devices are BusyBox based. It seems like they might have been hacked via a recently disclosed RCE vulnerability in CCTV-DVR (this is unconfirmed).
HTTP Flood Attack
As far as the DDoS attack, it was a variation of the HTTP flood and cache bypass attack, which is pretty standard and mitigated by the Sucuri Firewall. Very few servers can handle 50,000+ requests per second, but due to our Anycast network and stack optimization, that number is easily mitigated by us.
As for the attack indicators, they were leveraging random referrers and user-agent combinations in an effort to emulate normal browser behavior. The most popular referrers were:
- Referrer: http://engadget.search.aol.com/search?q=RANDOMKEYWORD
- Referer: http://www.google.com/?q=RANDOMKEYWORD
- Referer: http://www.usatoday.com/search/results?q=RANDOMKEYWORD
The user agents were pretty random as well and emulated the most popular browsers: Chrome, IE, Safari, etc:
- User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_7_4) AppleWebKit/534.57.5 (KHTML, like Gecko) Version/5.1.7 Safari/534.57.4
- User-Agent: Mozilla/5.0 (Windows NT 6.1) AppleWebKit/536.5 (KHTML, like Gecko) Chrome/19.0.1084.56 Safari/536.5
- User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; SV1; .NET CLR 2.0.50727)
IPv6 DDoS
We don’t see many DDoS attacks leveraging IPv6 yet, and this is another thing that surprised us as we saw quite a few of these devices coming from IPv6.
It wasn’t a big number, but almost 5% of all DDoS attack IP addresses came via IPv6.
That’s a change we expect to keep happening as IPv6 becomes more popular.
Protecting Your Sites
Unfortunately, as website owners, there is not much you can do to get those 25,000+ CCTVs fixed and protected. You also can’t do much to fix the millions of vulnerable devices on the internet that can be used as botnets and DDoS amplification methods.
However, you can do your part. If you are an online camera user or vendor, please make sure it is fully patched and isolated from the internet. Actually, not just your online camera, but any device that has internet access (from DNS resolvers to NTP servers, and so on).
We are in the process of reaching out to the networks that have these unprotected and compromised cameras, but that’s just one small piece of the problem. Once the cameras are patched, the attackers will find other easily hacked devices for their botnets.
If your website continues to go down, or you are experiencing DDoS attacks, I recommend trying the Sucuri Firewall. It is a cloud-based security solution that includes DDoS protection as part of our Intrusion Prevention and WAF stack.










16 comments
Great post and scary! Why someone would want to target a small brick and mortar jewelry shop ius beyond my uderstanding. Maybe this was done by Samaritan? 🙂
We got to know later on the reason, but I can’t share publicly.
However, most of the times it is a competitor or someone that is upset with you (former employee or customer). We are also starting to see more and more DDoS for ransom and the goal there is just money for the attackers (not personal).
Filthy Lucre. The days of inquisitive young hackers writing largely benign viruses or breaking into websites to leave scene props and boasting is long gone. Criminals are now running many of these things and are doing it to extort, blackmail, or steal.
Yes, all about money now.
General decline of society that has snowballed with the advent of mass communications and a degree of isolation between attacker and target.
The Internet was a sort of Utopia up to the mid 1990’s. Commercialization, growth, and globalization corrupted its character.
On the upside, maybe it has hastened our ultimate judgement.
Definitely Samaritan.
We had one of our clients that sells jewelry get hit the past few days also with a very large attack. I am really curious of the reason behind it since he is not a major dealer in the grand scheme of things.
Interesting. Mind emailing me the details (dcid@sucuri.net)? Would love to see if it correlates with what we saw.
I’d be very interested if this had a Samaritan aspect of exposing IoT vulns at a higher, ahem, “volume” to reach a broader audience than the infosec crowds.
Samples hashes?
Most of the countries listed here would be targets of China’s state sponsored hackers. I also understand that these hackers do offer hacking as a service to make a little extra cash. So an interesting question might be what else are they using these hacked cameras for? Taiwan might want to know.
That’s a good question. We are starting a more deep investigation to understand what is going on in addition to the DDoS. hopefully we will have something to share in the next few months.
Why in the world did they store the CVC code?
how can hacker control those CAM to flood HTTP request ?
do they build a FW and push it to CAM via HTTP ( because almost CAM doesn’t open Telnet or SSH port) ?
Offers Financial Assistance
Are you having Financial Constraints ,or you do not have Funds to settle your Bills and Debts, Bother no more for the solution is here, We provide quick Loans at a very minimum and Affordable Interest Rate of 3%.
Contact me via Email: loans.fundrexfinance@gmail.com
Best regards,
Management
This is sooo cyberpunk
Comments are closed.