When creating phishing lures, attackers may cite recent major regulatory changes within the context of their social engineering scheme to confuse or further entice victims into clicking a link or performing some action.
For example, in September 2019 the EU directive PSD2 went into effect (with some parts delayed until the end of 2020). This new directive requires an increase in security controls used by EU financial institutions.
From a client’s perspective, one of the biggest changes from PSD2 is the use of additional authentication measures like SMS OTPs (one time passwords) for accessing online banking and electronic payments. These changes require the client to have an up-to-date mobile phone number on their bank account or they will eventually have problems authenticating payments or logging into their banking accounts.
These new authentication measures are being exploited by attackers: victims are now much more likely to click on verification links in phishing emails with the intention of updating their account information to avoid service disruptions.
Phishing for Italian Postal Services
One recent example of attackers leveraging new security controls is seen in a phishing page found targeting client financial account data from the Italian postal service provider, Poste Italiane.
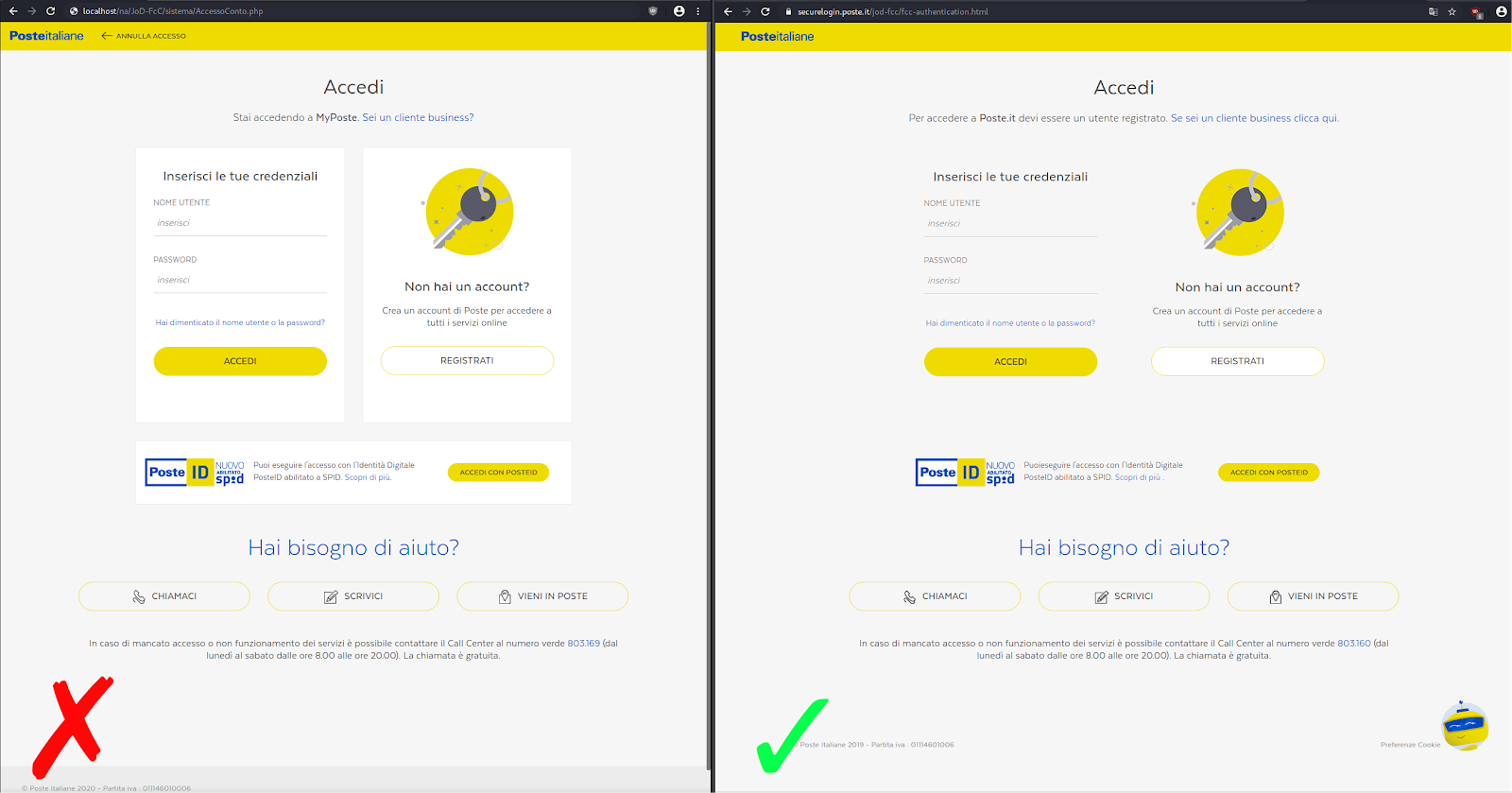
As you can see below, it is difficult to distinguish the phishing page from the real Poste Italiane login page. Interestingly enough, the phishing page has the current year (2020) for the copyright text in the footer, whereas the real Poste Italiane login page is still showing 2019.
Conditional Behavior & Redirects
After clicking the URL from the phishing email, victims are taken to the phishing kit’s redirector (/JoD-FcC/index.php), which is used to direct traffic based on certain requirements.
require_once('geoplugin.class.php'); $geoplugin = new geoPlugin(); $geoplugin->locate(); $country_code = $geoplugin->countryCode; switch($country_code) { …
In this case, the requirement is that the victim’s IP address must geolocate to the geographical area of Italy (country code – “IT”). If this condition isn’t met, the victim simply gets redirected to google.com instead of the phishing page (defined in /JoD-FcC/sistema/AccessoConto.php).
case 'IT': header('Location: sistema'); exit; default: // exceptions header('Location: https://www.google.com/'); Exit;}
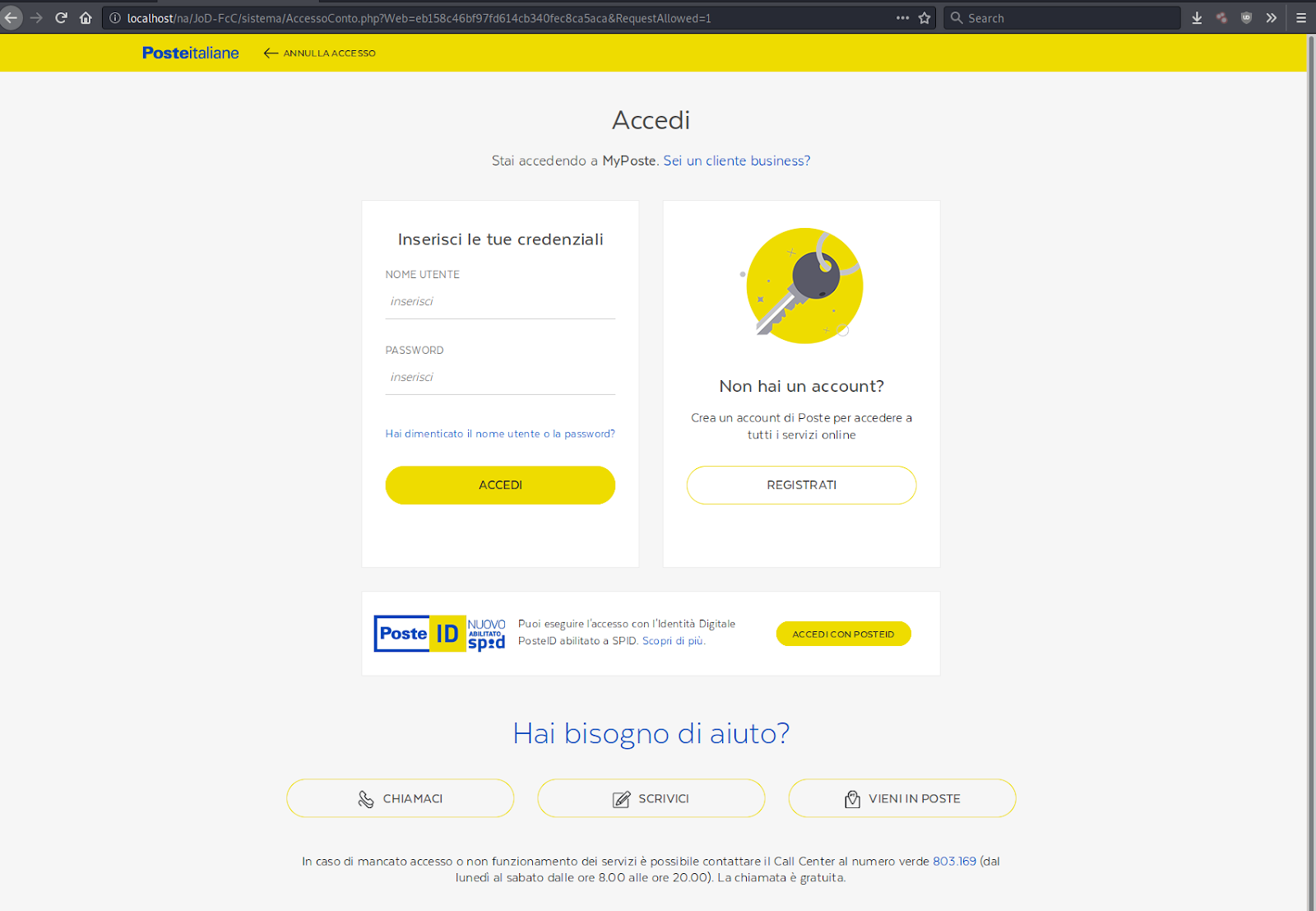
The first page in the campaign begins the phishing process by requesting the victim’s username and password for their Poste Italiane account.
After submitting the username and password, the victim is directed to the second page which requests personal data on the victim. From here, a request is made for the victim’s first and last name, along with the balance of their Post Italiane account.
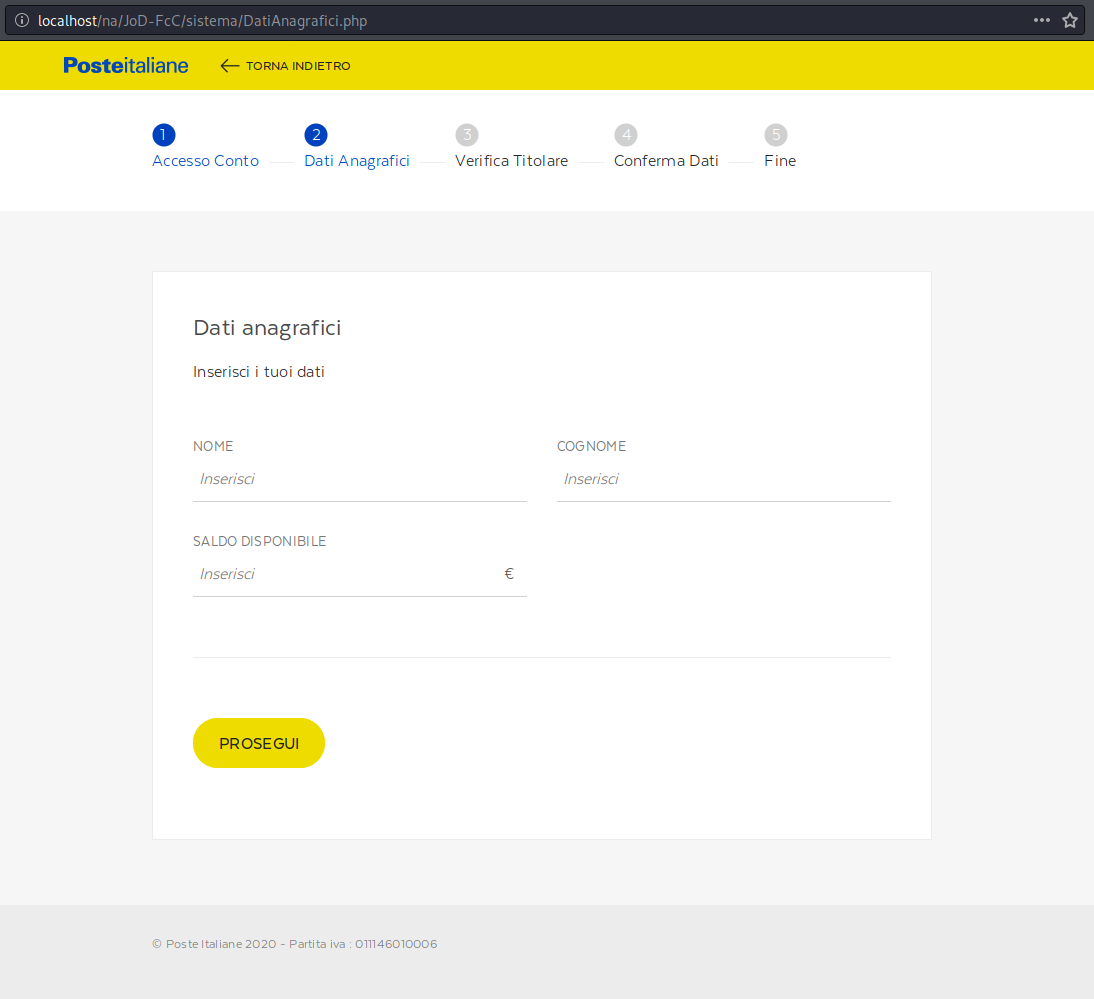
After submitting their name and available balance, the victim is asked for their payment card details.
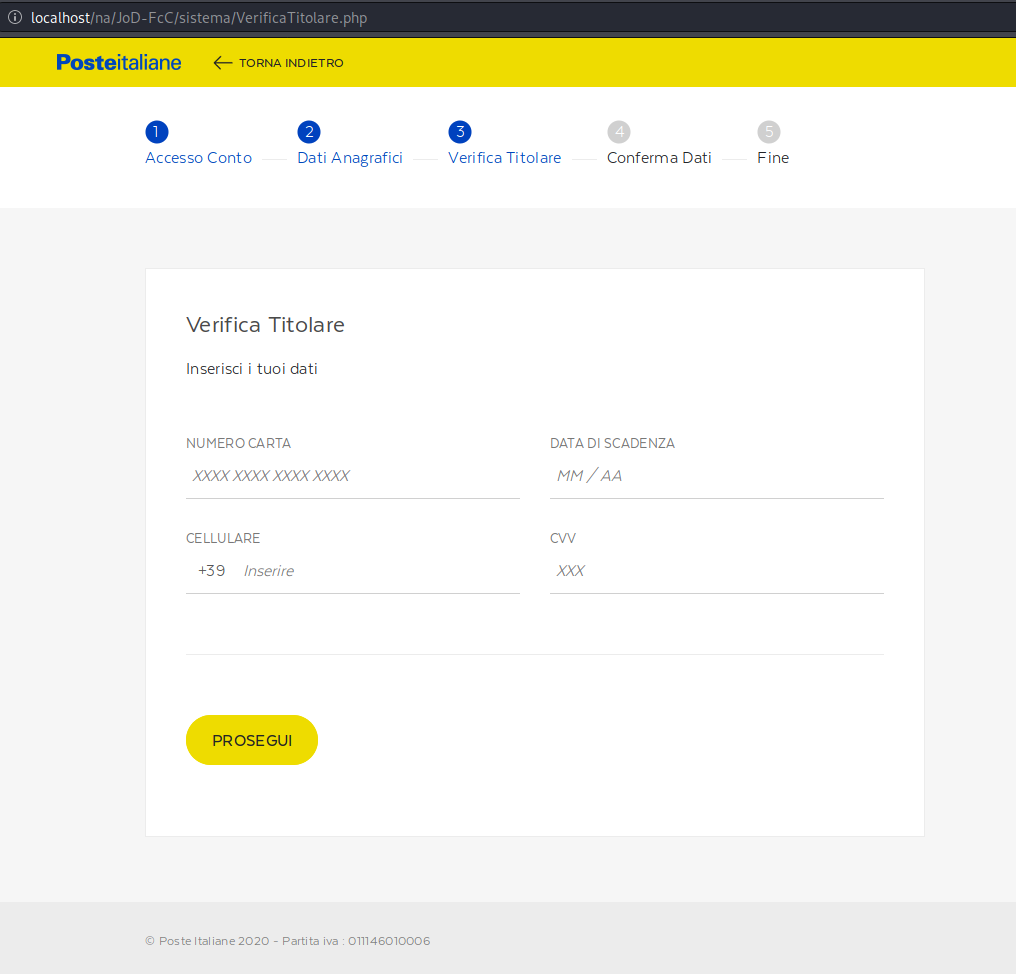
The first field requests the payment card number, however it is very selective in the numbers that it will accept in this field.
Determining Payment Card Issuers
So, why did the bad actors implement this functionality? Because the attackers are only interested in targeting specific BINs which are assigned to prepaid Mastercard and Visa cards registered to Poste Italia. The BIN (bank identification number) is typically the first six digits of a payment card’s number and can be quickly looked up to determine the payment card’s issuer.
The attacker uses JavaScript to limit the available inputs used on this specific form field:
function is_ppay() { var cc = document.loginForm.power1.value.substr(0,7); var ppay = /^(4023 60|4023 61|4030 35|4176 31|5299 48|5313 46|5333 17|5364 14|5354 76)[0-9]*/; if(!cc.match(ppay)) document.loginForm.power1.value = ""; }
If the first six digits (BIN) entered in the field do not match the six digit (BIN) sets defined in the ppay variable, then the attacker’s malicious JavaScript removes any digits that were already entered in the field. This prevents the victim from being able to type the digits of a payment cart not matching the defined BINs.
We can use a BIN lookup tool to confirm that these define BINs are all assigned to prepaid/debit cards issued by Poste Italiane:
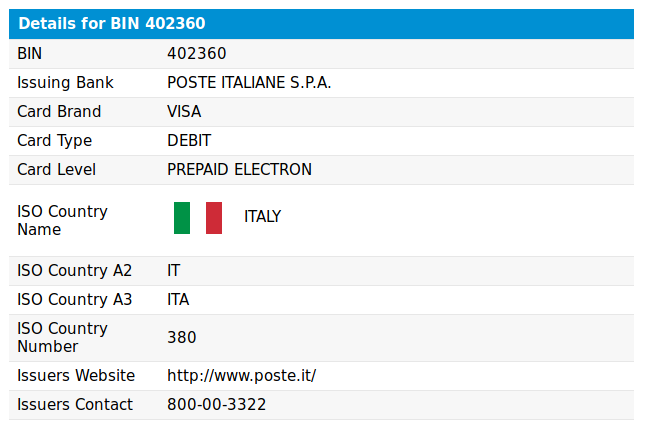
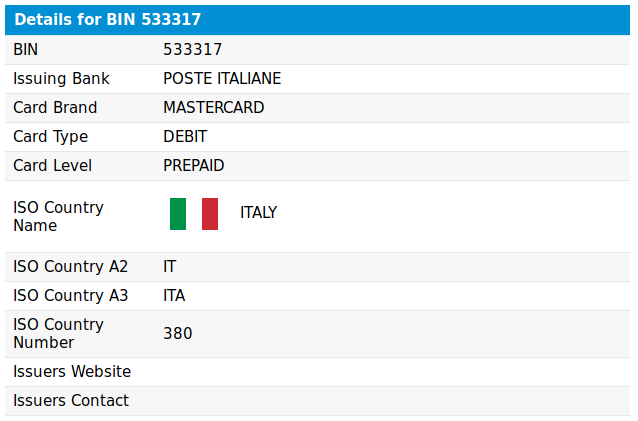
Harvesting Numbers for SMS OTP Verification
The telephone number associated with the victim’s Poste Italiane account is also requested. This information is used on the next page and involves the SMS OTP.

As previously mentioned, PSD2 regulations in the EU now require financial institutions to have strong authentication measures and this can often mean using SMS OTPs as an additional form of authentication. Only phishing the payment card data and the bank login data may not be enough to get unauthorized access and perform fraudulent charges.
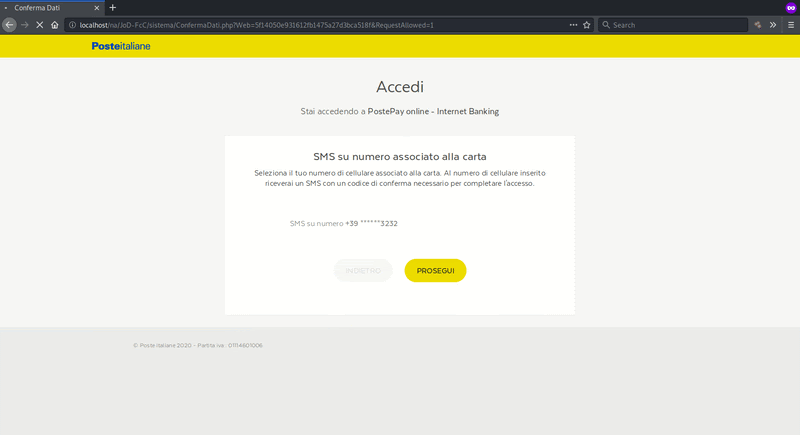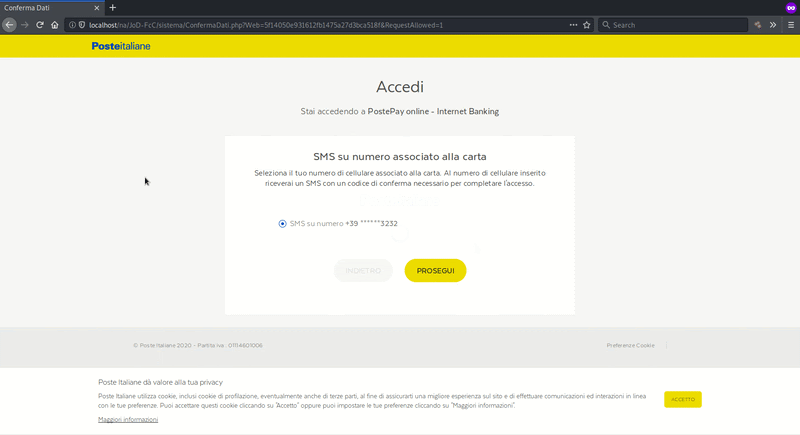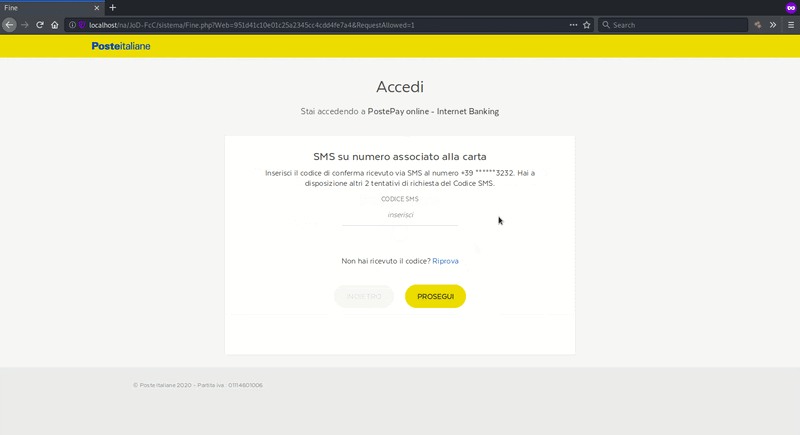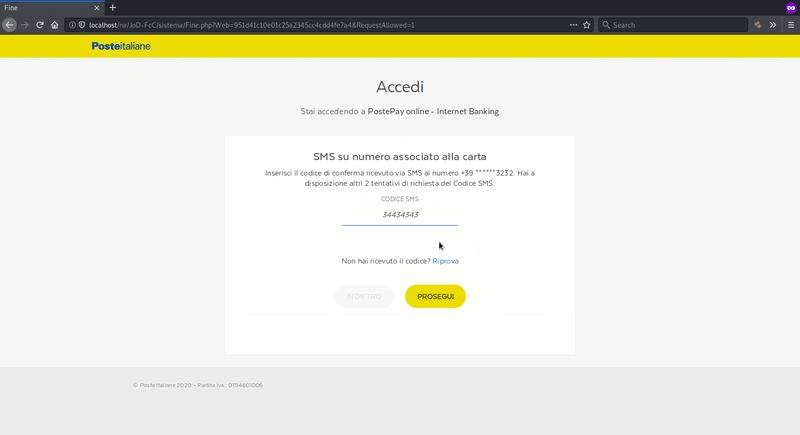
Once the victim submits their phone number from this final step, it’s game over. The attacker now has every piece of information needed to gain unauthorized access and modify account information.
Conclusion & Mitigation
Most phishing kits are usually hidden away in layers of subdirectories and don’t directly interfere with your website’s functionality. In an ideal scenario, the attacker conceals the malicious behavior and phishing pages from anyone who doesn’t meet a specific criteria.
The best bet for website owners who want to detect these types of phishing pages is to use a server-side scanner, since external scanners are usually unable to detect malicious behavior in their scans unless it meets the criteria defined in the bad actor’s code.