Email will continue to be the dominant mode of digital communication for the foreseeable future. However, the email framework was not designed with security in mind. There still are security flaws that bad actors regularly exploit to their advantage.
Recently, researchers have discovered a business-email compromise scam in Russia. Known as Cosmic Lync, the cybercriminal group running this scam has been associated with more than 200 security incidents targeting senior-level executives globally since July 2019.
This group can send phishing emails that look authentic, right from the content of the message to the sender’s address. Even an experienced user would find it difficult to identify a fake email without taking a deep -dive.
How it works
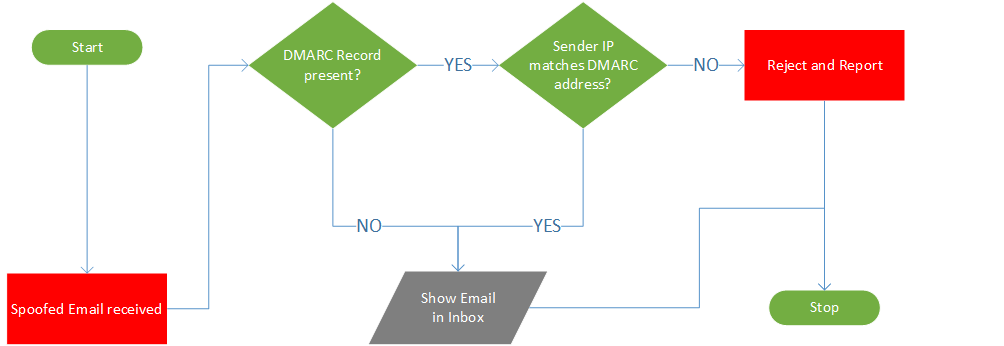
First, the attacker needs to find a vulnerable website by identifying if the website has a DMARC record, which is a TXT record visible in the DNS settings.
nslookup -type=txt example.com
If the website has no DMARC record, it means the attacker can spoof any email address with the website domain name. For example, the attacker can choose to send an email with the address ceo@example.com without any authentication.
Next, the attacker needs to set up an SMTP Open Relay Server, which is a regular mail server with the Relay option enabled. Sometimes, server administrators forget to turn off the Relay option. These types of servers are ideal for sending phishing emails, as they allow the attacker to send from a targeted phishing email address using the victim’s domain without having to authenticate.
The attacker can identify if the server is an Open Relay Server by running the following telnet command which checks for a connection to the default SMTP port (25):
telnet mail.examplemailserver.com 25
If the connection is established, it means the server is accepting SMTP connections:
Trying 192.168.1.2... Connected to mail.examplemailserver.com Escape character is '^]'. 220 mailserver.examplemailserver.com
The attacker can then check if Open Relay is enabled:
MAIL FROM: <ceo@example.com> 250 OK <ceo@example.com > Sender ok
If an OK is received, the server is accepting messages from email accounts that are not hosted on this server.
Running the following commands will then send the email to the target:
RCPT TO: <recepient@example.com> 250 OK <recipient@example.com> Recipient ok
Finally, the contents of the message can be sent with the following command:
DATA 354 Start mail input; end with <CRLF>.<CRLF> test email .
Pressing “.” sends the email.
The email might land into the inbox or the spam folder. But from the first look, it seems genuine.
Email Headers Reveal Spoofed Email
Let’s investigate the email headers for closer inspection:
Received: from MN2PR02MB5854.namprd02.prod.outlook.com (2603:10b6:a03:1d0::37) by BY5PR02MB6802.namprd02.prod.outlook.com with HTTPS via BY5PR04CA0027.NAMPRD04.PROD.OUTLOOK.COM; Tue, 4 Aug 2020 13:36:11 +0000 Received: from MWHPR21CA0069.namprd21.prod.outlook.com (2603:10b6:300:db::31) by MN2PR02MB5854.namprd02.prod.outlook.com (2603:10b6:208:113::31) with Microsoft SMTP Server (version=TLS1_2, cipher=TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384) id 15.20.3239.16; Tue, 4 Aug 2020 13:36:10 +0000 Received: from MW2NAM10FT060.eop-nam10.prod.protection.outlook.com (2603:10b6:300:db:cafe::a) by MWHPR21CA0069.outlook.office365.com (2603:10b6:300:db::31) with Microsoft SMTP Server (version=TLS1_2, cipher=TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384) id 15.20.3283.0 via Frontend Transport; Tue, 4 Aug 2020 13:36:09 +0000 Authentication-Results: spf=none (sender IP is 192.168.1.2) smtp.mailfrom=example.com; example.com; dkim=none (message not signed) header.d=none;example.com; dmarc=none action=none header.from=example.com;compauth=fail reason=001 Received-SPF: None (protection.outlook.com: example.com does not designate permitted sender hosts) Received: from mailserver.exampleserver.com (192.168.1.2) by MW2NAM10FT060.mail.protection.outlook.com (10.0.0.1) with Microsoft SMTP Server id 15.20.3239.17 via Frontend Transport; Tue, 4 Aug 2020 13:36:09 +0000 Received: from (UnknownHost [192.168.10.1]) by mailserver.exampleserver.com with SMTP; Tue, 4 Aug 2020 09:35:52 -0400 Message-ID: <982e2392-01f5-4275-bf47-0cbc97d73b97@MW2NAM10FT060.eop-nam10.prod.protection.outlook.com> From: <ceo@example.com> To: Undisclosed recipients:; Return-Path: ceo@example.com Date: Tue, 4 Aug 2020 13:36:09 +0000 X-MS-Exchange-Organization-ExpirationStartTime: 04 Aug 2020 13:36:09.6244 (UTC) X-MS-Exchange-Organization-ExpirationStartTimeReason: OriginalSubmit X-MS-Exchange-Organization-ExpirationInterval: 1:00:00:00.0000000 X-MS-Exchange-Organization-ExpirationIntervalReason: OriginalSubmit X-MS-Exchange-Organization-Network-Message-Id: db4b44e2-faeb-4c5d-b1c1-08d8387b58e1 X-EOPAttributedMessage: 0 X-EOPTenantAttributedMessage: d5f1622b-14a3-45a6-b069-003f8dc4851f:0 X-MS-Exchange-Organization-MessageDirectionality: Incoming X-MS-Office365-Filtering-HT: Tenant X-MS-PublicTrafficType: Email MIME-Version: 1.0 X-MS-Exchange-Organization-AuthSource: MW2NAM10FT060.eop-nam10.prod.protection.outlook.com X-MS-Exchange-Organization-AuthAs: Anonymous X-MS-Office365-Filtering-Correlation-Id: db4b44e2-faeb-4c5d-b1c1-08d8387b58e1 X-MS-TrafficTypeDiagnostic: MN2PR02MB5854: X-MS-Exchange-Organization-AVStamp-Service: 1.0 X-MS-Oob-TLC-OOBClassifiers: OLM:1728; X-MS-Exchange-Organization-SCL: 5 X-Forefront-Antispam-Report:
As you can see, the email is sent from the email ceo@example.com. The only difference is that the IP address of the sender’s email server does not match the IP address in the MX records of example.com.
Hence, if we can verify the sender’s IP address and correlate that with the MX records of the sender’s domain, we would be able to detect a spoofed email successfully — that’s what DMARC is designed to do.
Conclusion
DMARC (Domain-based Message Authentication, Reporting & Conformance) works in combination with existing security mechanisms like SPF and DKIM to identify if the email message comes from a legitimate mail server or if it is spoofed.
A typical DMARC record is a TXT record with the format:
Type: TXT Host/Name: _DMARC.example.com Value: v=DMARC1; p=quarantine; ruf=mailto:dmarc@example.com
Explanation of parameters:
- v=DMARC1 means the current version of DMARC
- p=quarantine means in case of DMARC violation the mail is quarantined by receiving email address listed by the next parameter
- ruf=mailto:dmarc@example.com means that the receiver will send forensic information about the quarantined email to dmarc@example.com
The presence of a valid DMARC record ensures that the receiver’s email server will not only identify if the mail is spoofed.
Adding a DMARC record is essential to prevent spoofed email.
According to a study made by Valimail, 79% of Fortune 500 companies and 25% of U.S. federal domains are still unprotected from DMARC-based spoofing attacks. You can help improve this statistic — and your website’s security — by setting up and implementing DMARC records if you haven’t yet done so.
Does your domain have a DMARC record? Let us know by tweeting us @sucurisecurity.