Seeking a reliable security testing tool can be overwhelming, given how large the opsec environment has grown over these last few years. Given how large things have grown, it’s become common to overcharge people in the industry for security services provided.
Due to this factor, it’s very beneficial for any small business or organization to consider their options in terms of free and open-source software available out there if on a budget. There are many free & open source security testing tools available out there, but the best places to look are with Github, reliable search engines, and within the infosec/opsec sphere of blogs and forums.
In this article, we’ll be discussing the most common ones used in an organization’s security arsenal and why they’re helpful.
It’s critical to consider hiring an expert or company that understands what they’re doing with these tools, however, acting impulsively based on information gathered with them can potentially be riskier than not utilizing one.
Why Security Testing Matters
In today’s online environment, testing for vulnerabilities as an organization remains critical in the face of threats and attacks. This means security testing tools play a crucial role in ensuring your organization is protected against any risks of compromises as much as possible.
As we cross over into the digital world, it’s become increasingly apparent how vulnerable our cyberinfrastructure can be. Some of the biggest ransomware attacks to occur last year were directly targeting oil pipelines, healthcare, food industries, and even water supplies.
With this in mind, we need to accelerate our progress in terms of educating and protecting our institutions and public ways of living across the world.
Not only is ransomware a major global concern, but targeted attacks against users in terms of scrapping and manipulating their data have become just as effective in taking down organizations and global infrastructure.
Social engineering and malvertising threats have become increasingly popular over these past few years, and there doesn’t seem to be much sign of it going away unless we take better care of our data, our organization’s data, as well as improve our abilities to properly analyzing said data.
We always need to keep in mind that usually, the most vulnerable point in any system is the people and steps need to be taken to ensure that that risk is minimized.
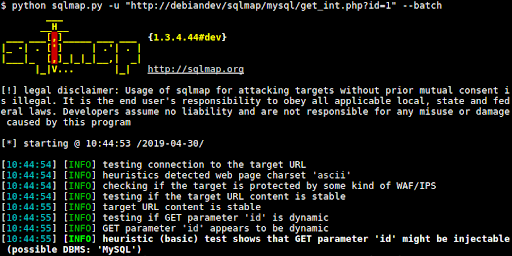
SQLmap
Finding vulnerable code within your organization and catching it before it’s exploited will always be a critical role in remaining secure online. SQLmap is specifically catered to being a dynamic detection engine that provides a variety of features for penetration testers.
They include a vast amount of support for database management systems and the 6 kinds of injection techniques. Since this tool has a wide array of features listed, including this within your security arsenal will certainly be beneficial in lowering the risks of SQL injections (SQLi).
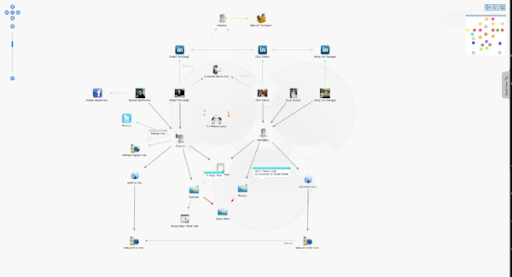
Maltego
Protecting you and your organization from cyber security threats in today’s climate has become a lot more complex. In regards to data collection, this open-source security tool allows you to access and integrate all of your data into one place. With this tool, you’re able to map, merge, and mine data.
Collaborating with your team or company regarding investigation reports and threat analysis will help develop an insightful understanding of what needs to be adjusted.
In addition to mapping and analyzing data, this software can provide you with a more detailed look into any false positive alerts associated with other security services that are being used. In terms of forensics reporting and penetration testing, this tool can provide a bunch of digestible information regarding any compromised system.
Overall, due to its vast amount of integrations amongst some of the most noteworthy data partners, Maltego should be considered in terms of these services an average scanner or firewall service is unable to offer.
WPScan
For websites using WordPress as their CMS, we’ve previously covered this security tool already, but it’s still a worthy mention. This tool will allow the average site owner or developer to scan for any specific vulnerabilities found within their WordPress website. We’ve also provided a helpful guide on how to install this tool for you here.
Wireshark
Having a Network Protocol Analyzer is intrinsically valuable to any organization existing online. Wireshark allows you to read/write in different capture formats, decompress with gzip, decrypt various protocols, and export this information.
Not only does Wireshark provide a wide range of useful security features at your disposal, but they also regularly provide education conferences and training regarding their program too.
Burp Suite Community Edition
The community edition of Burp Suite provides the average user with the necessary tools to scan their web applications for any vulnerabilities with automated scanning.
This tool helps you stay in check with compliance requirements (GDPR, HIPAA, PCI DSS, etc.) and provides a substantial workflow in terms of testing, reporting, and remediating vulnerabilities a lot more adequately.
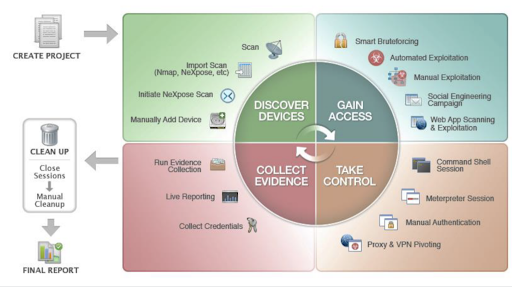
Metasploit
When it comes to finding, exploiting, and validating vulnerabilities Metasploit is no stranger. Allowing users to infiltrate, collect data, and remediate security concerns means your organization or business can be ahead of things and decrease potential risks of being attacked online.
By creating projects within your organization you’re then able to retrieve target data, run vulnerability scans, configure listeners, and generate reports.
In conclusion
The security tools mentioned in this post should be surely effective for your organization or small business, but there are still many free open source security testing tools that exist that we’ve not yet uncovered that foundations such as OWASP discuss as well.
Of course with all of this being said, users utilizing these tools will still need to understand what to do with the information given, or how to remediate anything they’ve discovered.
As previously stated at the beginning of this article, please consider seeking an expert or company that handles these tools if you’re unfamiliar or comfortable using them. These tools may require some triaging since sometimes not all of the information is set.
You can also spend a decent amount of time researching these in a collaborative setting, reading blogs, webinars, podcasts, etc.m and then coming up with a conclusion together.








