Ransomware is one of the most insidious types of malware that one can come across. These infections will encrypt all files on the target computer as well as any hard drives connected to the machine – pictures, videos, text files – you name it. This means that all of your files are locked. The attackers will then demand an extortion fee to have them decrypted, usually in the form of untraceable Bitcoin ransom. Like any ransom, you can never be sure they’ll stay true to their word or instead continue to demand more money.
The Evolution of Ransomware
Ransomware infections started appearing in 2013 and have been steadily on the rise since then. Today it is one of the most pervasive online threats that Internet users and businesses face. Traditionally, ransomware has only affected personal computers and the malware is often distributed through hacked websites.
Over the last few months, there has been a new development with ransomware attacks. They’ve started to infect websites themselves.
Unlike the DDoS BitCoin ransom we wrote about recently, these attacks infect and encrypt the website files and then demand payment. The files on the server are inaccessible and the homepage is defaced with a warning that the website has been held hostage.
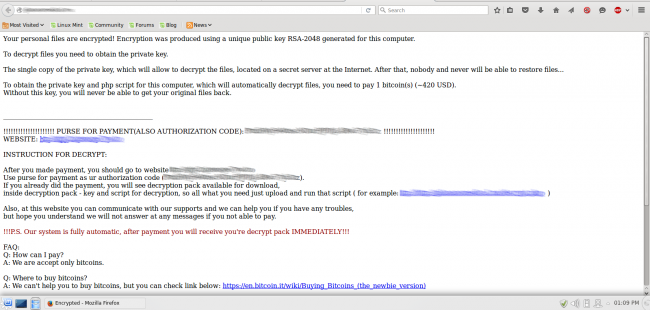
The malware was first discovered last November by Russian security company Dr.Web. Unsurprisingly, vulnerabilities in outdated software seem to be the main method of distribution. Remember web admins: Update, update, update!
Ransomware Now Targeting Websites
Usually, websites are used to spreading PC-based ransomware. Visiting the infected website will launch the payload onto the end-user machine, encrypting its contents. Earlier this year we documented a widespread campaign affecting WordPress sites that redirected visitors to exploit kits distributing ransomware. It’s also commonly distributed through tech support scams and bogus emails, but now we’ve seen website admins fall victim as well. Magento ecommerce sites seem to be a big target of this new website ransomware, but it is by no means limited to them.
AES Encryption
Once the attackers have access to your server, they encrypt all of your site files using AES and append .encrypted to the filename rendering them useless:
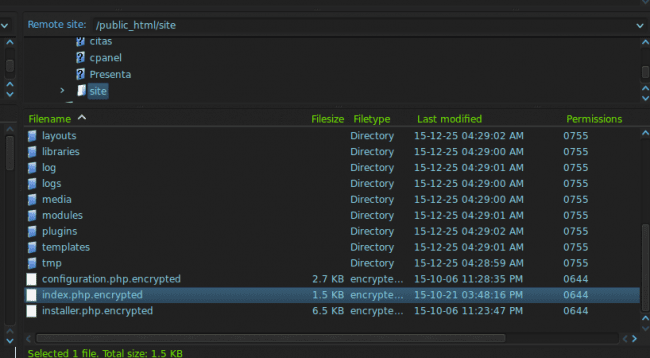
Initially, there was a flaw in the way that the files were encrypted. Using a clever method, the AES key could be guessed by the timestamp / last modified date on the files and a number of websites were able to revert the damage and save their data.
Not surprisingly, the attackers caught wind of their design flaw. Very recently, we’ve seen cases where a few of the timestamps have been intentionally scrambled by the attackers, thus rendering the entire decryption process useless. In these cases, without a usable backup, you might find yourself having to rebuild your entire website (unless you want to take the risk of paying the ransom fee, which I would not advise).
Cross-Contamination
Even worse, this malware (like any other) can spread to any websites in the same hosting environment through cross-contamination making a bad situation much worse. Remember: Compartmentalize your sites so that when disaster strikes at least the problem will be contained!
Website Backups Are Crucial
If you find your website has been infected with this malware, your best bet is to revert to a recent backup, change all administrator credentials and update all software. Cases like this are an excellent example of why having a sound backup strategy is imperative for all websites owners. If you don’t already have a backup service or a hosting provider that does that for you, then we have some straightforward steps written out here. If you are a server admin, you could also consider implementing a live shadow volume which is kind of like a RAID configuration.
Other Recommendations
Fortunately, this ransomware seems to be limited to the website files and does not appear to affect databases. If you find yourself rebuilding your site in the wake of such an attack, then you can try exporting your database and import it into a new, safe/clean hosting environment and replace all of your site files with fresh copies. That should leave your posts/content intact. Don’t forget to change your passwords when you do this!
To help avoid such infections on your website, I highly recommend putting your site behind a website firewall to prevent attacks before they even reach your server. I’d recommend this especially if you are stuck using an old, out-of-date CMS or don’t feel comfortable updating it yourself.








2 comments
Any live shadow volume would also be encrypted and thus useless, thus is not a backup strategy anyone should consider! – the only correct way to backup is to backup to a different place, server, service, off server location – however if the hack evolves, as the credentials for that off-server backup service are also stored in the database/config files the hacker could also grab those and encrypt those – I have not seen this yet, but its only a matter of time. I have seen several Joomla sites hacked this way recently – ALL were hacked over weak brute forced FTP Passwords, files downloaded, encrypted and then uploaded again and not through old Joomla versions or vulnerabilities. If you are using Akeeba backup – remember to upgrade to Akeeba Backup Professional and then use that to push your backups to a 3rd party service.
@ben wrote “If you are a server admin, you could also consider implementing a live shadow volume which is kind of like a RAID configuration.”
Mirroring in realtime does never ever protect you from hacks. Raid and raid-a-like system protect you from drive failures only. If you copy/mirror data live you copy/mirror every change in the file system. Frequent backups (as you already mentioned) protect you from disaster as long as you have an uncompromised one.
Today’s server admins should work with virtualization and do proper snaphshots of the virtual machines every day. This will allow to recover from any hack, exploit or hardware damage within minutes.
Comments are closed.