Since the beginning of November we’ve been cleaning many sites infected with the same SEO spam malware.
The malware creates doorways for hundreds of random trending keywords – from news to porn. For its templates, it uses mobile pages of some legitimate sites (probably taking into account the latest Google’s “mobile first” approach).
Infection Details
The attackers scan sites for known vulnerabilities and then upload a file with a random looking name that consists of 10 hex digits, e.g. 4ae0e06003.php, 4d9d041ee8.php, f18072c6bc.php, etc.
This zip file contains full source code of an open-source PclZip library. However, at the top of the file there are a couple of lines that first decode a long base64-encoded string and then write the resulting output into a .zip file. This file always has a random three-letter word for the filename – vlw.zip in the below example.
$data = base64_decode("UEsDBAoAAAAAAPigZ0kAAAAAAAAAAAAAAAAEAAAAdmx3L1B…
file_put_contents("vlw.zip",$data);At the bottom of the file there is a piece of code that extracts this newly created zip file within current directory (which is typically the site root directory):
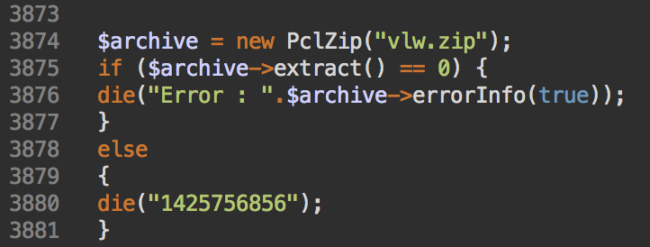
As a result, the following file structure is created:
- a directory with the same name as the .zip file
- two .php files hoop1.php and rohel.php
- .htaccess
- two subdirectories gknol and templates
Rewrite Requests and Cached Spam
This is what the structure looks like:
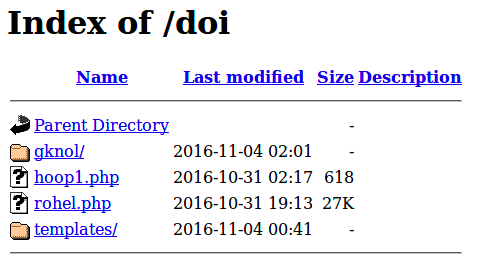
The files perform the following functions:
hoop1.php – makes the doorways ready for the SEO spam campaign by creating an .htaccess file with a rewrite rule to make the URLs look as if they were .html pages.
rohel.php – the doorway generator script. It creates content for search engine bots, mixing keywords found on search result pages of Ask.com, Yahoo! and Google for targeted keywords. It caches them in the gknol subdirectory. Real visitors get redirected to a link such as: hxxp://coolin[.]in/for/77?d=….
gknol – the subdirectory where the script saves cached doorway pages.
templates – the subdirectory with 10-20 page templates for spammy pages.
There are some other variations of the same infection. For example, it can be a master.php file (the doorway generator) and two subdirectories: save (cache) and shabs (templates).
The following redirect chain normally lands on porn pages:
hxxp://82.146.37[.]48/mobi?sub_id_1... -> hstraffa[.]com/l?link= … -> zvip[.]biz/aff_c?offer_id=20008&aff_id=6716& …
The actual chain may vary, depending the visitor’s location and browser.
Reinfection and Cross-Contamination
It is worth mentioning that the attackers try to infect all sites that share the same server account. This malware doesn’t depend on any CMS, so we find it on all sorts of websites from WordPress to pure HTML sites.
One site can be infected multiple times by this malware (several spammy directories) and quite often it can be infected with other types of malware and spammy doorways, like Japanese replica spam doorways.
This happens because webmasters usually neglect security issues for quite a long time. Even when they notice the problem and try to clean their sites, they either fail to remove backdoors from all of their sites or harden only their most important sites while leaving less important ones with unpatched security holes. In doing so, all of their accounts remain unprotected against reinfection.
This shows that every aspect of website security is important and should be done properly – cleaning, hardening (including configuration and proper isolation), monitoring, etc.









1 comment
Thanks for this Denis! Besides the proper methods of site security/hardening, anything specifics we can do to avoid this?
Comments are closed.