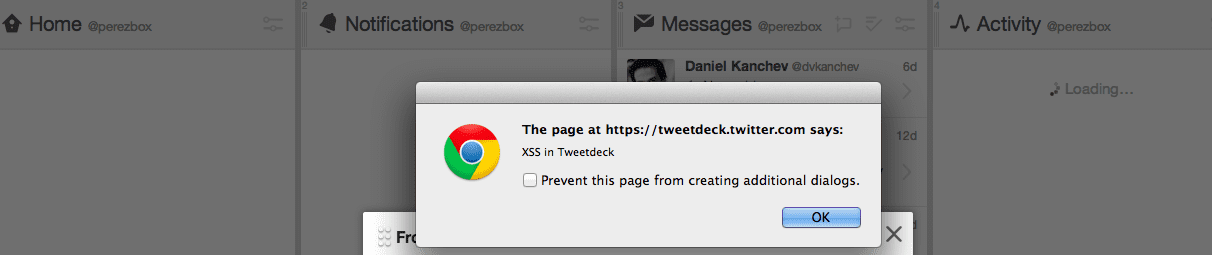
This morning as I was logging into various social networks I was presented with a popup from an XSS on Tweet Deck. This obviously set every hair on my neck on fire because it’s obviously not the normal welcome screen.
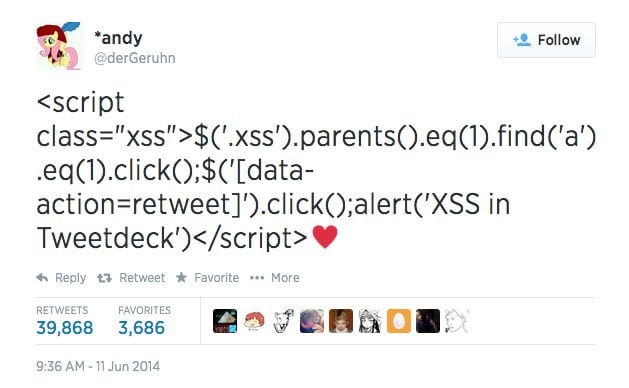
After some investigation, I found a tweet from one account that I follow which had the following JavaScript code as an example – it should be all good, but TweetDeck wasn’t sanitizing the input which caused the code to execute in the browser.
This is why, someone injected this into their tweet. When you logged into TweetDeck it triggered the vulnerability:
As you can see, the XSS attack was set to automatically retweet via this: data-action:retweet causing a chain event for anyone that logs into TweetDeck.
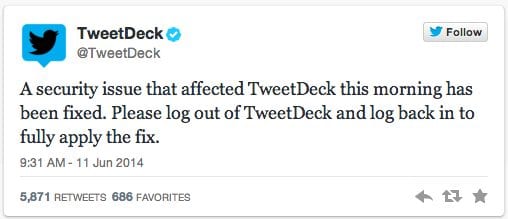
This is a very serious security flaw. TweetDeck says they have already addressed the issue:
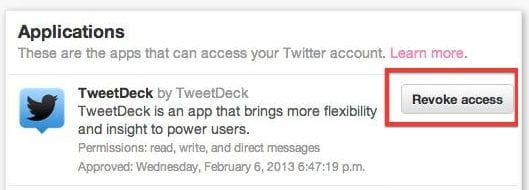
To be safe though, we recommend logging out of Tweetdeck, revoking access in your Twitter profile and resetting all connections if you want to continue to use the application.
What is very annoying about this is that you can’t undo the automatic retweet, making it very difficult to remove from people’s timeliness. Thankfully, the attack is mostly benign and appears to be intended to making a statement than causing harm, but it’s clear example of how the largest of applications can be exploited.






4 comments
You can easily just log into twitter and click “unretweet” and it removes it from your timeline.
Twitter client worm, woo! That was *really* fun to watch this morning.
good work
I noticed that yesterday, the original tweet from @derGeruhn had ~81K retweets. Today it was down to 79K, so I’m suspecting that some people are removing their retweet.
Also, I broke down the code and examined how it worked. Turns out you don’t even need that much code to have forced users to retweet you. See http://g-liu.com/blog/2014/06/how-tweetdeck-got-hacked-the-non-technical-answer/ my blog post for an overview of what that tweet does and how it forced you to retweet it.
Comments are closed.