Security Risk: Medium
Exploitation Level: Easy/Remote
DREAD Score: 6/10
Vulnerability: Stored XSS
Patched Version: 4.0.3
During regular research audits for our Sucuri Firewall (Cloud WAF), we discovered a stored XSS vulnerability affecting the WordPress Jetpack plugin, currently installed on more than a million WordPress sites. The vulnerability can be easily exploited via wp-comments and we recommend everyone to update asap, if you have not done so yet.
Vulnerability Disclosure Timeline:
- May 12th, 2016 – Initial report to the Jetpack team
- May 26th, 2016 – Jetpack disclosure released.
- May 27th, 2016 – Sucuri disclosure released.
Are You at Risk?
The security bug is located in the Shortcode Embeds Jetpack module, so if you don’t have it activated on your site you’re not affected by this issue. An attacker can exploit this vulnerability by leaving a comment containing a carefully positioned shortcode to inject malicious Javascript code on the vulnerable website.
As it is a Cross-Site Scripting (XSS) vulnerability it could allow an attacker to hijack administrator accounts, inject SEO spam to the affected page, and redirect visitors to malicious websites.
Technical Details
This bug is very similar to the bbPress vulnerability we disclosed last week, another instance of text carelessly being replaced with some HTML tags.
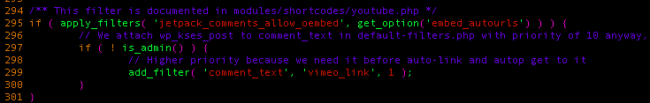
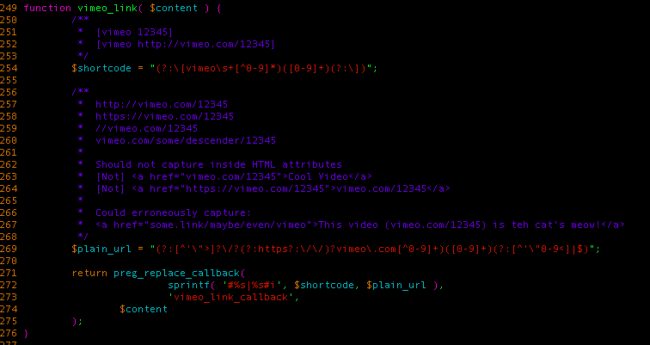
In this case, our journey begins with the comment_text hook, which is used when printing a comments content. The vimeo_link is hooked there so it can modify the comments output dynamically.
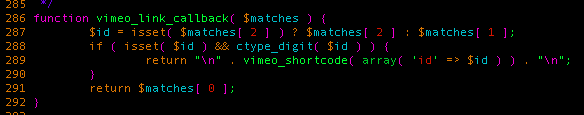
As you can see from the above regexes, it will look for a vimeo shortcode inside the comment and if it finds one, it will pass it to the vimeo_link_callback function.
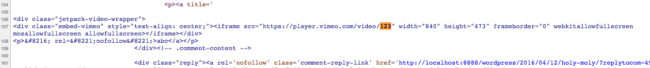
What is returned is an HTML tag containing the embedded Vimeo video. Let’s take a look at what the resulting output looks like if we send a comment containing <a title='[vimeo 123]’>abc</a>:
Woah, what happened there? It looks like our title attributes ending single quote (‘) disappeared! All we needed to make a working exploit from there was to ensure we could properly close our title attribute and insert new arbitrary event handlers to run our POC. As we said, very easy to exploit.
We worked with the JetPack team and they responded immediately and kept us on the loop the whole time.
Update as Soon as Possible
If you’re using a vulnerable version of this plugin, update as soon as possible! In the event where you cannot do this, we strongly recommend leveraging the Sucuri Firewall or equivalent technology to get it patched virtually.










3 comments
thanks, as always, for maintain us informed and secure 🙂
Good job, guys.
Thanks for the heads-up Sucuri. You guys are awesome!
Comments are closed.