WordPress 4.7.2 was released two weeks ago, including a fix for a severe vulnerability in the WordPress REST API. We have been monitoring our WAF network and honeypots closely to see how and when the attackers would try to exploit this issue the wild.
In less than 48 hours after the vulnerability was disclosed, we saw multiple public exploits being shared and posted online. With that information easily available, the internet-wide probing and exploit attempts began.
Patches Are Not Being Applied
WordPress has an auto-update feature enabled by default, along with an easy 1-click manual update process. Despite this, not everyone is aware of this issue or able to update their site. This is leading to a large number of sites being compromised and defaced.
We are currently tracking four different hacking (defacement) groups doing mass scans and exploits attempts across the internet. We see the same IP addresses and defacers hitting almost every one of our honeypots and network.
If Google is correct, these defacers seem to be succeeding.
Campaign #1
Just for one defacer, which we call Campaign #1, Google alone shows 66,000+ pages compromised:
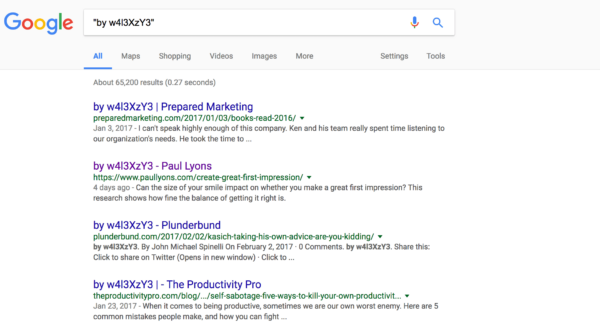
They started the exploits less than 48 hours ago. We assume Google hasn’t had time to reindex all compromised pages. We anticipate that the number on Google’s SERP will continue to increase as the re-indexing scans continue.
IP Addresses being used:
- 176.9.36.102
- 185.116.213.71
- 134.213.54.163
- 2a00:1a48:7808:104:9b57:dda6:eb3c:61e1
Defacer[s] group behind it: by w4l3XzY3.
We recommend blocking these IP addresses or investigating their activity via your logs. Specially if you didn’t update in time.
Campaign #2
The second campaign is not as successful, with Google only showing 500+ pages compromised. This campaign started just a few hours ago, so probably not enough time for Google to index the pages.
IP Address:
- 37.237.192.22
Defacer[s] group behind it: Cyb3r-Shia.
Campaign #3 and #4
This campaign is a bit unique, where two different defacers are sharing the same IP address. Each defacer has compromised over 500 pages (according to Google).
IP Address:
- 144.217.81.160
Defacer[s] group behind it: By+NeT.Defacer & By+Hawleri_hacker
We don’t like naming defacers as they do it for publicity, but we are sharing their names so we can track their growth better and compare with other security companies. If you have been hacked by any of these, or you see their names showing up on any of your blog posts, they likely used this vulnerability to compromise the site.
Spam SEO Will Be a Problem
The defacement campaigns are going strong and increasing by the day, but we believe that it will slow down in the next few days. What we expect to see is a lot more SEO spam (Search Engine Poisoning) attempts moving forward. There’s already a few exploit attempts that try to add spam images and content to a post. Due to the monetization possibilities, this will likely be the #1 route to abuse this vulnerability.
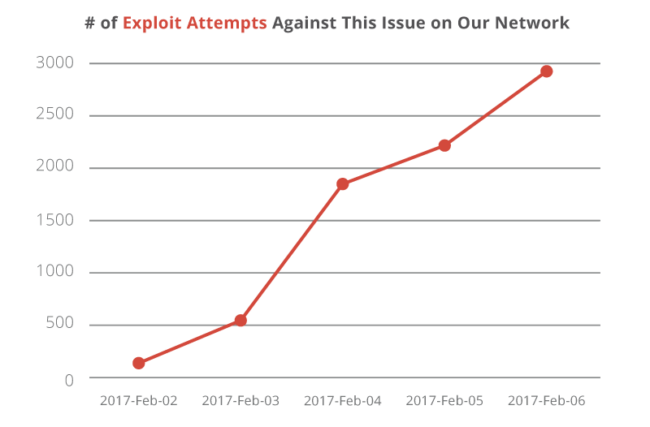
This is the currently exploitation attempts against our WAF Network for the last 5 days:
This vulnerability is very recent and lot may change in the next few days. We will keep sharing updates as this issue progresses.
Be on the know:
We have released a WordPress Security Guide that allows you to be up to date with vulnerabilities and the best practices you need to be able to effectively protect your website.






![Massive ois[.]is Black Hat Redirect Malware Campaign Targets WordPress Sites](https://blog.sucuri.net/wp-content/uploads/2022/11/BlogPost_Feature-Image_1490x700_PHP-Login-Stealer-390x183.png)