Last week, we described how an ongoing massive malware campaign began using Baidu search result links to redirect people to various ad and scam pages.
It didn’t last long. Soon after the publication of that article, the bad actors changed the links to use compromised third-party sites and a couple of day later they began using Google’s goo.gl URL shortening service.
This is a snippet from their decoded script:
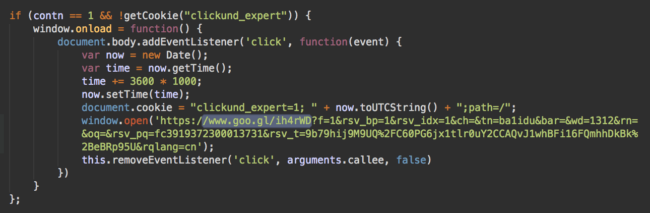
The Redirect Chain
If you check Google’s own information about that shortened URL, it shows that the URL redirects to another Google owned URL maps.app.goo.gl which looks quite benign. This domain is used for sharing user location on Google maps.
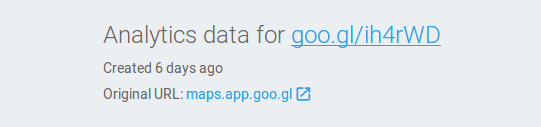
Don’t click on it though. Things are not as simple as Google makes them seem. Let’s check the same shortened URL in Unmask Parasites:
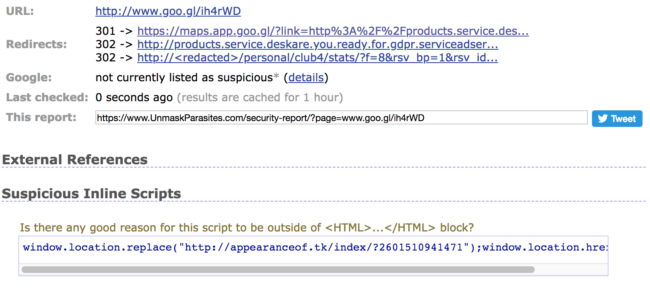
The results page shows that maps.app.goo.gl is actually just the first step in the chain of redirects. Then they go to the already familiar Cyrillic domain with many misleading subdomains (in this case xn--h1ards[.]xn--p1ai or чсти[.]рф), and after that, to a compromised third-party site containing JavaScript that redirects to random, frequently changing .tk sites.
These sort of redirects are typical to campaigns operated by roi777. They push location-dependent ads and scam pages and are specifically notorious for fake lottery and fake technical support scams. For more information about roi777 campaigns, we recommend reading this recent blog post by Kafeine.
Open Redirect Vulnerability in maps.app.goo.gl
Now let’s return to the second step of the redirect chain. How did hackers manage to have Google location sharing service maps.app.goo.gl redirect to a malicious site? It turns out that it was not difficult at all. You just need to add any URL in the ?link parameter and maps.app.goo.gl will start redirecting to the specified URL. For example, this URL https://maps.app.goo.gl/?link=https://sucuri.net currently opens Sucuri’s website. That’s called an open (unvalidated) redirect.
This security issue has been known for quite a while. For example, you can find the vulnerability report on the Open Bug Bounty site. It was originally reported by LewisBugBounty on September 10, 2017 and publicly disclosed on December 9, 2018. Apparently, Google didn’t find this issue serious enough to fix and anyone still can use their site as an open redirector.
goo.gl vs maps.app.goo.gl
It’s interesting to see that the attack uses two types of goo.gl links as the initial steps in the redirect chain. The first one is a normal shortened goo.gl link and the second is a crafted redirect via maps.app.goo.gl. So what’s the difference?
The shortened goo.gl link efficiently hides the real link destination and the domain reputation helps avoid problems with blacklisting. On the other hand, goo.gl links can be created only via Google site or their API, so the creator of the link can be potentially tracked. Even for links shortened by anonymous users, anyone can view various analytics data such as time of creation, volume of clicks, and referrers (infected sites in our case).
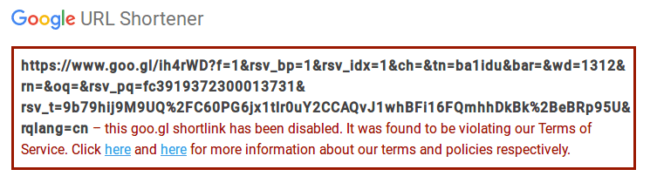
What’s more important, the URL shortening service has Terms of Service and Acceptable Usage Policy which among other things specifically prohibits “directing users to sites containing spam and malware”, and “shortening URL re-directors”. This means that any shortened goo.gl link can be disabled for violating the rules.
During the investigation, the link was reported to Google and it was disabled. All infected websites with this variation of malware now open the “disabled” notification instead of malicious ads:
While maps.app.goo.gl redirect links have a reputable domain name that can hardly be blacklisted, they are not good at hiding the final link destination, which is in plain sight right after “?link=”. This might not be a big issue for certain attacks, especially when it’s not the first step in the redirect chain as in this case. Moreover, maps.app.goo.gl has several advantages over the regular goo.gl for using in malicious activity.
- Anonymous and untrackable. One doesn’t need to use any Google services to create redirect links.
- Unblockable. Since the open redirects are just a side effect of the service, there is no easy way to report and block such links to stop malicious activity.
Too bad Google leaves this redirector open.
Attack Volume
Now, let’s take advantage of the hackers’ choice of the URL shortening service and check analytics data for this campaign (for this link only – not all infected sites have this goo.gl variation of the redirect at the moment).
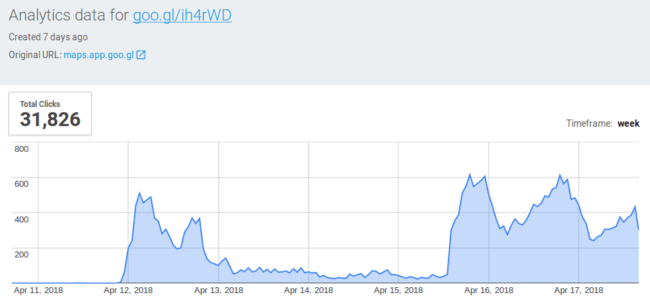
As you can see, the link had been created on April 12, 2018 and attracted over 31 thousand clicks (opened popups) in one week, with about 8 thousand clicks on an average “good” day and very few clicks during the weekend.
No more goo.gl links?
A funny fact about this link is that it was created on the last day when goo.gl allowed anonymous users to shorten links. Right now, every goo.gl page has this notification:
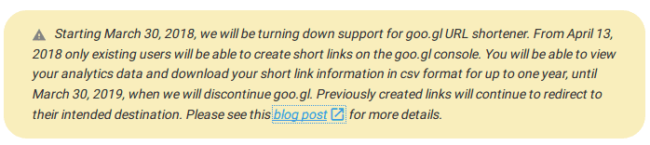
This means that the attackers will no longer be able to create new goo.gl links anonymously. Registering fake accounts will not help, as users who have never created short links before March 30, 2018 will not be able to create new goo.gl links either.
At this point, the ih4rWD goo.gl link has already been in use for a whole week and the attackers will have to replace it with something else soon. Unless they managed to shorten multiple links before April 13, we won’t see any new goo.gl links used by this malware.
While we are waiting for new creative variations of this attack, you can read our previous articles and the WordPress cleanup guide that will help you mitigate the damage if your site was one of the many hacked sites. If you believe your website has been compromised, we are happy to help you.