Our Remediation group is comprised of two distinct teams, the Incident Response Team (IRT) and Malware Research Team (MRT). These teams work closely with our customers in an effort to identify and remove website infections to include malware, SEO spam and a number of other malicious actions attackers take once successfully penetrating a websites defenses. It’s through these teams that we stay in tune with the emerging website threats, while offering our customers the most efficient remediation services.
This group currently remediates a little over 500 infected websites a day, 7 days a week. With this kind of volume we thought it was time we analyze the data. So we did! Focusing on January through march, Quarter 1 of 2016, we were able to profile the types of open-source CMS applications in our network, how many were out-of-date at the time of infection and place special emphasis on the types of infection payloads the attackers are using. With this information, we’ve prepared our first Website Hacked Report 2016 (Quarter 1).
CMS Analysis
Our analysis consisted of over 11,000 infected websites that we had enough data for. We feel this is a representative sample, and over time will prove more impactful when we look at the year as a whole.
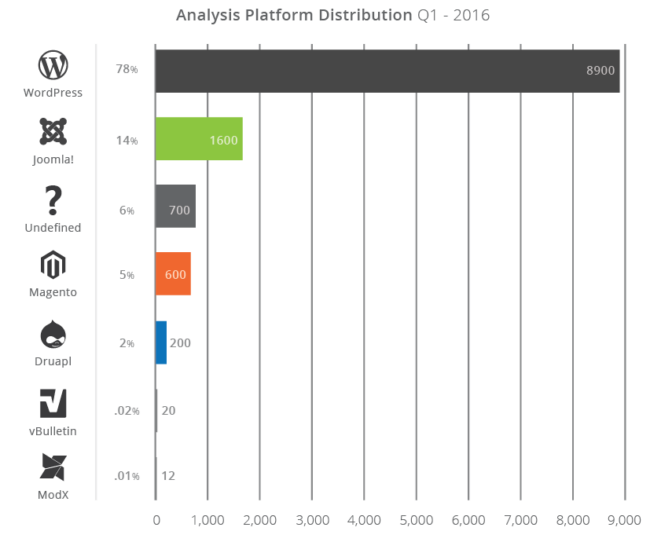
The four open-source Content Management Systems (CMS) we focus on in our report include: WordPress (78%), Joomla! (14%, Magento (5%), and Drupal (2%). The report shows some historical trends, such as a 196% growth in infections in Magento between 2015 and 2016 Q1.
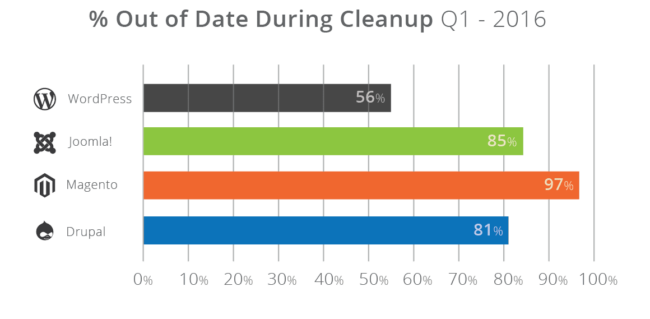
We dive into specific information around the out-of-date software, specifically how it pertains to the state of a website when going through our cleanup process. Some interesting datasets include that WordPress installations are out-of-date 56% of the time, but that is nothing compared to Joomla! (85%), Magento (97%) and Drupal (81%).
We briefly dive into specific extensible components within the WordPress platform as it makes up the largest sampling in our environment (75%) and place special emphasis on the top three plugins contributing to the most issues and that make up 25% of the contributing vectors we are currently seeing.
Malware Analysis
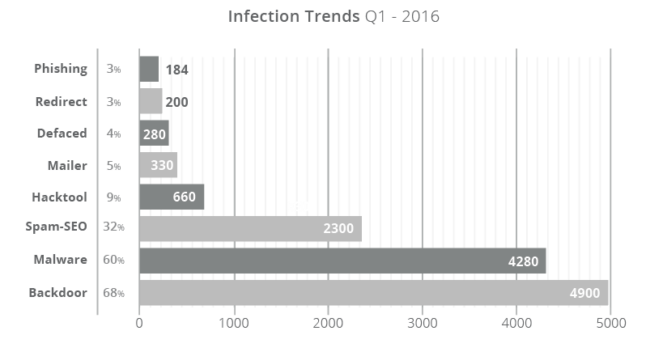
We also focused on understanding specifically what attackers were doing once they successfully compromised a website. Specifically the types of malware and nefarious actions they were performing once they successfully penetrate a websites defenses.
We divide it into the specific malware families we identify with. It’s been interesting to see the rise of Search Engine Poisoning (SEP) attacks in which the attackers inject SEO spam into a website targeting it’s Search Engine Result Pages (SERP). SEO poisoning of a website came in at 32%, while 68% of the time we found backdoors on each of the sites.
New Website Security Report
I’m especially proud of our ability to share this information with the greater website security industry, and hope you find it insightful. I already have thoughts on way to improve it i the future, but look forward to your thoughts as well. I would really appreciate it if you took some time to read it and share it if you find it valuable.
In our next report, we have already updated our system to start tracking more pertinent data that we feel could be more actionable for all website owners. My hope is that we can double, if not triple our sample base with more consistent and relatable datasets.
The report is available both on our site, and in PDF format. Have no fear, it’s not gated!!!












15 comments
Great work, thank you for sharing. Its a good insight into whats going on. The PDF was worth looking at for more details 🙂
Awesome stats!!!
Wait for the next one 🙂 We are adding a lot more insights and data.
Great share!
Would be interesting to see how these stats compare to the market share of each cms … or maybe I missed that?
Yeah, that is a big point to leave out. This data needs to be normalized against market share.
I agree could we get that statistic?
As Tony mentioned on another comment, this data is based is compromised sites that our team worked on. So it is always going to be biased to match the behaviour of sites that got hacked (for whatever reason) and found/used our company to get it resolved.
For that reason, measuring that against our own market share would not make much sense. Same as if we tried to compare our numbers against the overall CMS market share:
http://w3techs.com/technologies/history_overview/content_management
It would not be a 1/1 match. That’s why we left out it.
Hi @bartnelis:disqus
In the report we talk to the fact that market shares are different, and the fact is not lost on us. This report however is specific to the data we’ve collected from our network and has little to do with market share. You can definitely speculate however that some of these numbers are to be expected for a number of reasons, including market share.
Thanks
Yup, was wondering the same thing. Glad the mod already answered 🙂
But… nice article providing some useful insights..
Thanks for starting to publish these reports. You guys are currently manually reviewing my site via Rainmaker. Might just register my other site with you guys directly, for security protection. Been dealing with hacker-related problems on our site since last year (hence the switch to Rainmaker) so it’s nice to finally see trends via reports like these. Thank you.
That’s a great one. Thanks for the great contribution.
good analysis. does your Report define the terms under Malware Analysis, such as Backdoor and Hack Tool? I need to read up on these to understand better exactly what each type is. thx
Hello guys, I know some professional hackers who has worked for me twice in the past one month. They are very good at hacking anything concerning database, emails & social media and credit score . They offers legit services excellently. Contact them if you need such service Alphafasttunnel247@cyberservices.com. You will be grateful
Comments are closed.