The malware attack that began as an installation of malicious Injectbody/Injectscr WordPress plugins back in February has evolved since then.
Some of the changes were documented as updates at the bottom of the original blog post, however, every week we see minor modifications in the way they obfuscate the scripts or the files they inject them into.
Encrypted WordPress JavaScript Files
At this moment, the most common injection targets are core WordPress JavaScript files:
wp-includes/js/jquery/jquery-migrate.min.js
wp-includes/js/jquery/jquery.js
wp-includes/js/wp-embed.min.js
Hackers add the malicious code and then obfuscate the entire file contents along with the original legitimate code so that the only way to clean the files without breaking the site functionality is to replace them with their original clean copies. You can locate the current core WordPress files for version 4.9.5 here.
Footer.php Injection
Another common infection target is the footer.php file of the active WordPress theme. In this case, the obfuscated malicious code is injected at the very bottom before the </body> tag.
Typical injections look like this.
<!-- my-footer-content --><script data-cfasync='false' type='text/javascript'> eval(function(p,a,c,k,e,d){e=function(... removed for brevity … .split('|'),0,{})) </script></body> </html>
Actual code changes roughly every week. Nonetheless, the functionality of the code stays the same – it creates popups containing unwanted ads. All malware modifications feature the “clickund_expert” cookie that it sets for one hour in order to avoid recurring popups during short browsing sessions.
Baidu Links in the April Modification
At the beginning of April, we noticed one interesting variation of the malware that began opening Baidu (largest Chinese search engine) links in the popups.
Here’s a piece of the deobfuscated code showing how they use them:
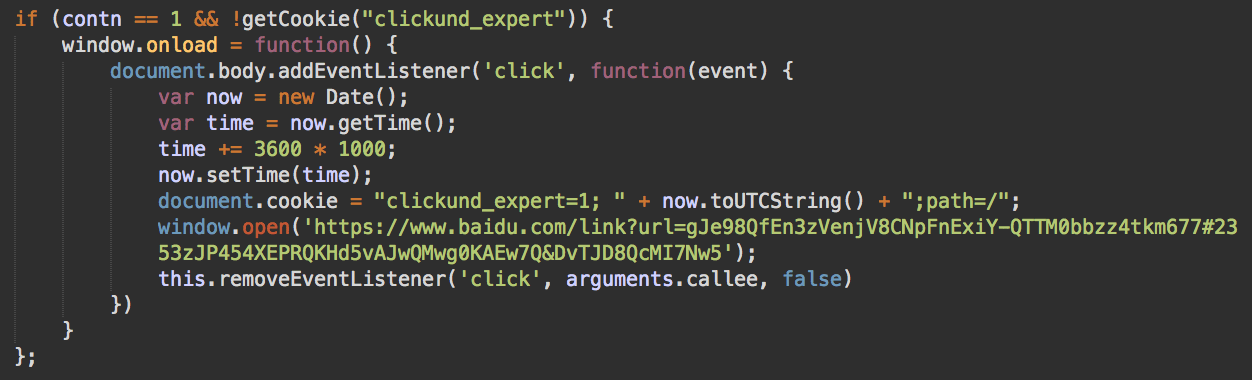
It turns out that on April 4th, 2018 they registered a new domain 7494568[.]info, made Baidu index it, and then used the Baidu search result link which you can see in above screenshot.

Redirect via Cyrillic domains
They also used a so-called “cloaking” technique to make sure that while Baidu’s crawler sees some normal content (which looks like random text found on many Chinese online stores), the rest of the visitors get redirected to the usual attack intermediary pages with long unreadable addresses whose parts look like addresses of popular legitimate services like YouTube, Google, e.g.
hxxp://www.youtube.com.channel.ucc4mcmfvjukr99e7mnr34sa.coe54eqko2zlh77v5yubra.www.google.com.imgres.imgurl.fvtjd8qcminw.maxresdefaultcoeb7eqko2zlh8cbv5yubra.youtu.be.lbl6ya7coeb8eqko2zlh8cbv5yubrar2uq.xn--80aqhr[.]xn--p1ai/1a747.xnp1ai1ai.o1aqry.xnagyp1.ds2ai.myaccount.youtu.be/imgres/imgurl/?imgres?imgurl=https://i.ytimg.com/vi/vTJD8QcMINw/maxresdefault.jpg&imgrefurl=https://www.youtube.com/watch?v=....
Note: The whole highlighted part of the above URL is the domain name, with many subdomain levels that include misleading words like: www, youtube, com, channel, google, imgres, youtu, be. The path part of the URL also has various misleading parts that resemble URLs of Google image search results and Youtube links.
The real second-level domain of that URL is “xn--80aqhr[.]xn--p1ai” (лапи[.]рф in Cyrillic ). It redirects to sites like “ganymede-or-hylas[.]tk”, “flemish-tapestry[.]tk”, “then-hepulled[.]tk”, “curtained-picture[.]tk”, “monstrous-maladies[.]tk” etc., that in turn redirect to some ad landing pages.
That 7494568[.]info site is hosted in Germany on a server with the IP 5.9.253.154. That server also hosts the xn--80aqhr[.]xn--p1ai” (лапи[.]рф) domain, as well as the following Cyrillic domains with the same malicious functionality:
- xn--h1au4a[.]xn--p1ai (ить[.]рф)
- xn--i1av6a[.]xn--p1ai (яфй[.]рф)
- xn--o1aqy[.]xn--p1ai (пчя[.]рф)
- xn--i1aa6a.xn--p1ai (йфй[.]рф)
- xn--l1adg6b[.]xn--p1ai (ыорм[.]рф)
These attackers are not going to stick to just one Baidu link for one malicious domain. For example, on April 6, 2018, they registered the patbat[.]info domain and a few days later began using a new variation of the packed JavaScript in footer.php files that opened the Baidu link (hxxps://www.baidu[.]com/link?url=r4v_ZO_dobBdAfTBWOfcBC3bMWIFNGK9joM_ya306Ai) pointing to that site.
For patbat[.]info, the redirect chain became even longer. It first redirected to a hacked third-party site, and only then to a typical attack site with many subdomains on a Cyrillic second-level domain.
Use of Baidu links in Malware
In this case, Baidu was used for the same purpose as hackers previously used URL shortening services like bit.ly, goo.gl, etc. This way, they hide the actual redirect location and make it harder to block after the script analysis – Baidu links can hardly be blacklisted.
Although we don’t see this trick quite often, it’s not the first time we have come across it. For example, some time ago Baidu links were actively used in Skype spam campaigns promoting various pills and dietary supplements.
Mitigation
Please check our previous article on the cleanup steps for this infection. In addition to checking for unknown plugins in wp-content/plugins, removing rogue WordPress admin users, and changing passwords for the rest users, we highly recommend that you verify all core WordPress files are intact and replace any changed ones with files from the official WordPress repository. We also advise you check to ensure your theme files (especially footer.php) were not modified.
For more details on how to perform such steps, please read our guides on WordPress Security.