This article was written by Christopher Vera, CISSP, HISP, GCFA, GLEG for Sucuri.

Of all the elements of a successful cyber security program, security awareness is probably one of the least understood. Some cyber security professionals have even gone as far as to claim that security awareness doesn’t work. Their observations are not entirely unfounded. The key is that successful awareness programs must provide value to their audiences. When they don’t provide value they are ignored, and thus ineffective, plain and simple. Further, a security awareness program cannot protect a user from everything. With new platform-agnostic attacks bypassing even fully patched systems with host-based firewalls and the most recent anti-virus signatures, it’s easy to throw one’s arms up in frustration. But defense in depth is one of our most trusted principles. We understand that no one security control can protect us from every threat. Otherwise, we’d have tossed out our network firewalls years ago. The advantage of a successful security awareness program is that it’s much less expensive to implement and maintain.
When most people think of security awareness, they generally think of clever websites, e-mails, and posters reminding us to adhere to the organization’s acceptable use policy or to stop clicking dangerous links. But a successful awareness program is more than the sum of its topics or its delivery mechanisms. It’s about changing the culture of our organizations. The agenda of all awareness programs is to change behavior; to replace security apathy with reasonable concern and consideration of security risks. It’s not fast. Success sometimes requires months or years. It’s difficult to measure effectiveness well. It’s as much a marketing campaign as a security control. In short, security awareness is a strategic element to a cyber security program, not a tactical one. This means our security awareness programs must have strong strategies (a topic for another time), and therefore, clear missions.
Let’s be clear about mission statements. They are short statements of purpose that an organization can use to drive strategy and decision making. The mission statement that I created for my own organization has worked so well it has been adopted by my company’s communications department and even external awareness initiatives like “Securing Our eCity” in San Diego, California.
The mission is so simple you may roll your eyes. I propose that the mission of a successful awareness program must be to “deliver the right message to the right people at the right time”.
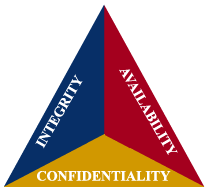
Experienced cyber security professionals may recognize those words as a succinct description of the CIA Triad (Confidentiality, Integrity, and Availability) and that principle is precisely from where I adopted this strategy.
This mission helps those of us responsible for managing an awareness program focus on the three critical success factors: our audiences, our delivery mechanisms and our messages. These factors are based on criteria unique to our organizations’ needs. But what does it mean? How can we put this into action?
The right people
When it comes to communications, nothing frustrates our audiences more than being distracted by messages that don’t apply to them. If 90% of our audiences already regularly do the right thing, say, don’t connect their personal mobile devices to the network, then why, for goodness’ sake, would we make them sit through one hour web based presentations on about the dangers of connecting personal devices to the network? If an audience isn’t responsible for patching Microsoft Windows systems, why e-mail them monthly reminders about the latest Microsoft vulnerability? Eventually, the message (and our branding) becomes diluted and future messages will be ignored. We have failed to provide value because the target audience rightly feels we are wasting their time. We didn’t care enough to send a relevant message, so why should they care about absorbing it?
Therefore, target audiences must be as granular as we can make them and still manage them successfully. Who should we deliver “don’t connect personal devices” messages to? Only those with a high risk of attempting to connect personal devices! Contractors and vendors come to mind. Who should receive messages about Windows vulnerabilities? Only audiences responsible for patching Windows systems.
The value of our awareness program increases as we tune our messaging for specific audiences that directly benefit (or avoid severe discomfort) from the content being delivered.
The right message
As awareness program managers, we must continually adapt our messaging. Think in terms of timely talking points. Evolving elevator speeches. Our awareness programs must constantly say old things in new ways in order to keep the content relevant to our audience and so provide value. The topics are often the same: passwords, e-mail, web browsing, information management, phishing. But sometimes it’s not what we have to say; it’s how we say it that makes the difference.
Take passwords. Passwords can be an incredibly boring topic because everyone has been told over and over about their obligations to create and manage their passwords.
Does your password messaging look anything like this?
Passwords should be at least 6 characters long and contain at least three of these four: upper case characters, lower case characters, numbers, special characters. It should not be anything found in the dictionary. Oh, and don’t write it down.
Ouch! It’s all well and good, but is as dry as toast and will be forgotten immediately after it is read because its value is limited. Compare that with this set of talking points about the benefits of passphrases.

Instead of a password consider a passphrase instead, which is easier for you to remember and harder for bad guys to guess. Use a mnemonic to make it easier to remember without writing it down. This works for your own personal passwords as well as organization ones. Which is easier to remember and harder to guess using the mnemonic of “fast food”?
Ch33zBrg3r$
or
Cheeseburgers@my.house
In this messaging example, we provide value by giving the audience a fresh way at looking at an old problem, and we make it personally relevant (it works at home too). When we need to share password complexity requirements, say for compliance reasons, we can link to the specific document in policy, standards and guidelines. Audiences that know the password standard can freely ignore the link. Others, like new hires, can click it for more information. This saves everyone time. Now that’s the right message!
The right time
Pop quiz. Many people in our organizations will probably get a virus or other malware this year. When is the best time to warn them not to click on potentially malicious links?
- A month before they click,
- A day after they click, or
- Right before they click.

Timing, as they say, is everything. So it is in our awareness programs. Every time a celebrity dies, or a major disaster strikes somewhere in the world, we quickly deploy prepared messaging (based on templates that can be easily modified to suit the message) using several different delivery mechanisms to warn our high risk e-mail and web browsing audiences to expect scammers to begin sending them malicious e-mails or links to malicious websites. Warning audiences about malicious links after your IT department has responded to 2500 users with malware on their systems is too little, too late. Our goal is to be able to provide inline context-based organizationally branded awareness to our audiences while they are using e-mail or web browsing. Newer versions of Microsoft Office and various browsers try to do this with pop-ups (“are you sure you want to open this?”), but use generic messaging that users tend to click through without a thought.
Often times, well-meaning awareness programs will deliver cookie cutter messaging on a monthly or quarterly basis, hoping audiences will remember that the message they read in January applies to the malicious link they receive in September. No wonder our messaging doesn’t perform to our expectations.
Provide value
Our audiences have their own jobs to do. They will never understand (or even want to understand) everything we know about cyber security. Provide them value by giving them the information they need to make their life easier. They don’t want computer viruses, or to be held accountable for a newspaper headline because they failed to shred confidential documents. Effective awareness is a critical element of a robust cyber security program that helps our organizations solve problems. This in turn positively influences behavior. Which in turn, positively influences the culture of your organization from one of security apathy into one of security awareness.
The right people, the right message, the right time. I look forward to hearing your own thoughts on the mission of security awareness.
Christopher Vera, HISP, CISSP, GCFA, GLEG is an information security practitioner with over 11 years experience in drafting and publishing security policy, creating and managing multiple computer incident response and forensics teams, as well as vulnerability management, security engineering and security awareness programs. With a degree in Geological Sciences from San Diego State University, he is trained to examine the positive and negative synergies between large collections of systems. He works in the energy industry and is an active member of Infragard. He also writes science fiction and poetry. christophervera.com










7 comments
I fully agree with you and even i have noticed that while i conduct session , I never pay this attention that target audiences is not ready to accept all the information that i have related to cyber security. I should cut off the geeky part and should only deliver the part that is suitable for target audience … I think this will solve the issue right ?
My recent post PFConfig (Update your router automatically | No need to do port forwarding manually).
Rockey, thanks for reading the article. Every communication we deliver–whether in person or electronically–must be targeted for the audience it is intended to reach. There's nothing wrong with including the "geeky part" if you have an audience that you know will appreciate the more technical aspects of your presentation. I find in my own organization, that the average employee does not really care for the details. This is okay! They want just the info they need to reduce the risk to themselves and to the organization. Interestingly, this forces us to be more creative about how we deliver the content (war stories work GREAT here!). Which makes it more interesting and entertaining. Which means you will be invited back to speak more often to deliver more awareness content. Win-win!
Great post, Chris! This is a very pragmatic and effective approach to awareness. My comment pertains to the “right people” section. I think that help desk and support entities are a necessary audience for awareness communications. These groups are at the front line. They make up the “human IDS” which is key in spotting abnormalities, patterns and other things that just seem out of place. How many times have security incidents been identified by a number of callers reporting some vague but unusual system behavior? Effective security awareness and point communications keep them alert, aware and ready to respond.
You're right Prince! In fact, let me add that *every* person in an organization becomes part of the "human IPS". Not only can they help detect events, but in the right circumstances, they can prevent them from happening. The best measurement of this comes from communications we get from our employees: "I saw this strange thing (usually an e-mail) and I just deleted it."
I really like this 🙂
Comments are closed.