A Java Zero-Day vulnerability was disclosed today, and its being distributed through the use of websites.
If you visit an infected site you’ll see something like this if you have Java disabled. It will not always show though:
![]()
It is ill-advised to allow it to run. Please be sure to disable Java on your browser momentarily to give the Java developers some time to develop a patch.
Disable Java by following these steps:
- Internet Explorer readers: http://kb.iu.edu/data/ahqx.html
- Mac readers: http://www.maclife.com/article/howtos/how_disable_java_your_mac_web_browser
The signature for the payload can be found in our labs here: http://labs.sucuri.net/db/malware/mwjs-encoded-dadong1
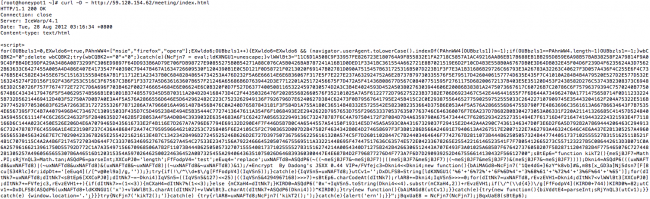
If you open a site you feel might be infected using curl you’ll be able to better see the payload.
Curl usage:
curl -D – http://[domainname]/index.html
Payload displayed:
Although Java is platform independent, the current payload appears to be targeting Java installs on Windows 7 SP 1 boxes, confirmed by a number of local desktop Anti-Virus companies.
Here are some details on the infection:
- It’s JavaScript obfuscated using jsxx 0.44 vip
- When applet.jar is loaded, it disables protection against local files file://
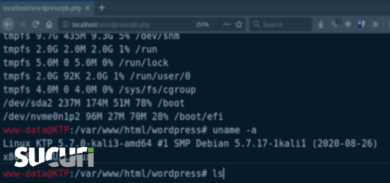
- It then targets the Windows OS here: check os.name <http://os.name/>;, if it’s not “Windows” then exit
While our focus is not desktop, web properties are being used to distribute this payload and further infect local environments. Please do your due diligence to check your website to ensure you’re not increasing the risk of distributing this to your visitors.
Our definitions have been updated, if you’re a client you’ll be notified on the next scan, if you’re not, you can always use our free scanner, SiteCheck.
If you have any questions or concerns please leave us a comment or send us a note at info@sucuri.net.










4 comments
I really like that you are providing information on core and advance java , being enrolled in http://www.wiziq.com/course/1779-core-and-advance-java-concepts, i was looking for such information online to assist me on core and advance java concepts and your post helped me a lot .thAnks
Comments are closed.