New release!
On 11/03/2017 everything you need to know on how to secure your WP site came out and it includes best practices and a list of vulnerabilities. Read it now!
Updated: 9/14/2016
Pharma hacks continue to evolve, our latest articles shares the latest tactics being employed. Additionally, we’ve released a detailed guide on how to identify and remove hacks from WordPress.
We get to deal with infected websites on a daily basis and the most common question we get is how do we clean websites. What steps do we take? What should you do if you want to clean up your site if it gets infected?
This is part one of a small series of posts showing how to clean up sites. We will start with how to clean up “Pharma Hack” on a WordPress driven site due to the popularity.
We also released a guide on how to clean a hacked WordPress site with our plugin.
*Note that this post covers website clean up only (Mostly applicable to shared servers). If you have a dedicated server (or VPS), there are additional steps to secure it, not covered here.
**If the items contained in this post are more than you want to take on, we are here to help. Visit Sucuri or email us at support@sucuri.net
1- Detecting (discovering) that you are hacked
This is the most important step. Most people don’t realize they’ve been exploited, here are a couple things you can do to check your site:
Fire up Google and do a search for “site:yoursite.com”. Check to see if there are any strange titles or spammy results returned on your search. If you see Viagra, Cialis or any other flavor of medicine returned by Google on your search, you’re probably dealing with the Pharma Hack.
If you’re not sure after checking Google, use http://sitecheck.sucuri.net to run a scan. Type your domain name, and if it returns the Pharma Hack (or any other malware) you will see an alert:
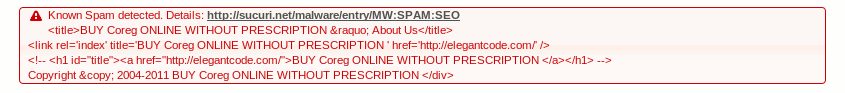
2- Fixing Vulnerabilities
If you’re WordPress site is infected with the Pharma Hack, here are a few things you can do to fix some of the vulnerabilities:
1-Make sure your WordPress install is upgraded up to date. If not, update it ASAP. Even before you start cleaning up the malware.
2-Change your WordPress password (for all admin / editor accounts) and your FTP (or SSH) password.
3-Update all your plugins.
Check out our post on WordPress Security – Yet Another WordPress Security Post – Part One
3- Removing backdoors
This is the first step in the clean up process. These types of attacks often times include loading backdoor files on your server to allow access to attackers in the future. If you don’t remove the backdoors, the attackers will be able to reinfect your site pretty easily. These are the files to look for AND REMOVE:
wp-content/uploads/.*php (random PHP name file) – Any PHP file inside your uploads directory
wp-includes/images/smilies/icon_smile_old.php.xl
wp-includes/wp-db-class.php
wp-includes/images/wp-img.php
Also, search for the following characters in all your PHP files:
ZXZhbChiYXNlNjRfZGVjb2RlKCJhV1lvYVhOelpY
eval(base64_decode
$a = ‘m’.’d5′
$y = ‘base’.’6′
If any of these characters are found in one of your files, remove it.
4-Cleaning up the file system
After successfully creating a backdoor into your system, the attackers usually add a new plugin file that is called everytime WordPress is loaded. Here are some examples of the file names we see regularly:
akismet/wp-akismet.php
akismet/db-akismet.php
wp-pagenavi/db-pagenavi.php
wp-pagenavi/class-pagenavi.php
podpress/ext-podpress.php
tweetmeme/ext-tweetmeme.php
excerpt-editor/db-editor.php
akismet/.akismet.cache.php
akismet/.akismet.bak.php
tweetmeme/.tweetmem.old.php
The file names typically follow the above naming convention, but the plugin names used are random. We do not recommend you rely only on these samples for your search, and also try looking for any plugin file with the “wp_class_support” string on it.
$ grep -r “wp_class_support” ./wp-content/plugins
./wp-content/plugins/akismet/db-akismet.php:if(!defined(‘wp_class_support’)) {
./wp-content/plugins/akismet/db-akismet.php: define(‘wp_class_support’,true);
If you are infected, you will see things like the above output and you can safely delete them (full content of the file here):
5- Cleaning up the database
This is where the Pharma Hack actually loads the spam from. It uses a few entries inside the wp-options table, so connect to your database and run the following queries:
delete from wp_options where option_name = ‘class_generic_support’;
delete from wp_options where option_name = ‘widget_generic_support’;
delete from wp_options where option_name = ‘fwp’;
delete from wp_options where option_name = ‘wp_check_hash’;
delete from wp_options where option_name = ‘rss_7988287cd8f4f531c6b94fbdbc4e1caf’;
delete from wp_options where option_name = ‘rss_d77ee8bfba87fa91cd91469a5ba5abea’;
delete from wp_options where option_name = ‘rss_552afe0001e673901a9f2caebdd3141d’;
That should do it for database cleanup.
6- Verifying it all
After you are done with clean up, we suggest the following:
- Re-run the WordPress update tool (to overwrite all the files with a clean copy)
- Remove your cache files (if you’re caching your site)
- Go to your WordPress admin panel and remove any admin/editor users that aren’t supposed to be there, or that are no longer in use.
- Re-scan your site for malware. http://sitecheck.sucuri.net
You should be good to go at this point. If you have any question, let us know.
Check out our new plugin: http://sucuri.net/wordpress-security-monitoring










28 comments
I think I’d just delete and reinstall WP and restore posts. Minimally, I’d do a forensic analysis each time and not count on them making the same changes every time.
In a previous post about the Pharma hack you mention doing a string search on the files looking for “php $[a-zA-Z]*=’as’;” and also about the search noted under number 3 – how do you do a string search on the php files on my install?
I checked the above website and it says mine comes back clean, yet it redirects to Feedburner in addition my email address jason@jasonestevens.com is not working either. Any idea of this type of attack or is something else going on? Thanks for the help.
My site is infected with a version of the Pharmahack that your tool is not detecting. If I run it through Webmaster tools as Googlebot the Pharma crap appears, but your tool does not pick it up.
can sucuri pick up hack that effected your database?
Recently a Pharma Hack was executed on my WordPress website. The hack was activated by running the following plugin file: /wp-content/plugins/db.php. As this file has not been mentioned in your article I think it’s important to share it with you.
Who is your web host provider? I would like to track back links on a site hosted on a different provider than mine. You don’t have to give me your URL but I would like you to give me the URL of one incoming link with a drug name in it. I’m doing research if you are wondering.
I have a question: What would happen if the sites that Pharma Hack is redirecting to or putting frames had to shut down and reopen with a new URL. Would this kill the hack and force the crackers to have to go back and patch in a new URL?
In all my WordPress sites, the code added like below:
Can anybody help me, how to remove this code from all the files at a time.
Thanks.
Showing like: <?php /*versio:3.02*/ $GLOBALS["ktrmpz"] this.
Do you need a university degree, Do you want to hack a college degree of any university,
do you intend to upgrade your score, do you need that
information concerning any database, do you need bank
details, credit card details, SSN, hack into your
cheating spouse’s phone to get any info you want? add me
on Y! messenger @ wisegeek2001
Thanks for sharing a useful informatio.
thank you for this
Comments are closed.