*Update 2015-04-27*: A patch has been released and made available by the WordPress Core Team in version 4.2.1 – Please update immediately.
Yes, you’ve read it right: a critical, unpatched XSS 0day in WordPress’ comment mechanisms was disclosed earlier today by Klikki Oy.
Who’s Affected?
If your WordPress site allows users to post comments via the WordPress commenting system, you’re at risk. An attacker could leverage a bug in the way comments are stored in the site’s database to insert malicious scripts on your site, thus potentially allowing them to infect your visitors with malware, inject SEO spam or even insert backdoor in the website’s code if the code runs when in a logged-in administrator browser.
You should definitely disable comments on your site until a patch is made available or leverage a WAF to protect your site and customers.
Technical Details
This vulnerability requires an attacker to send a comment long enough to force the backend MySQL database to truncate what is stored.
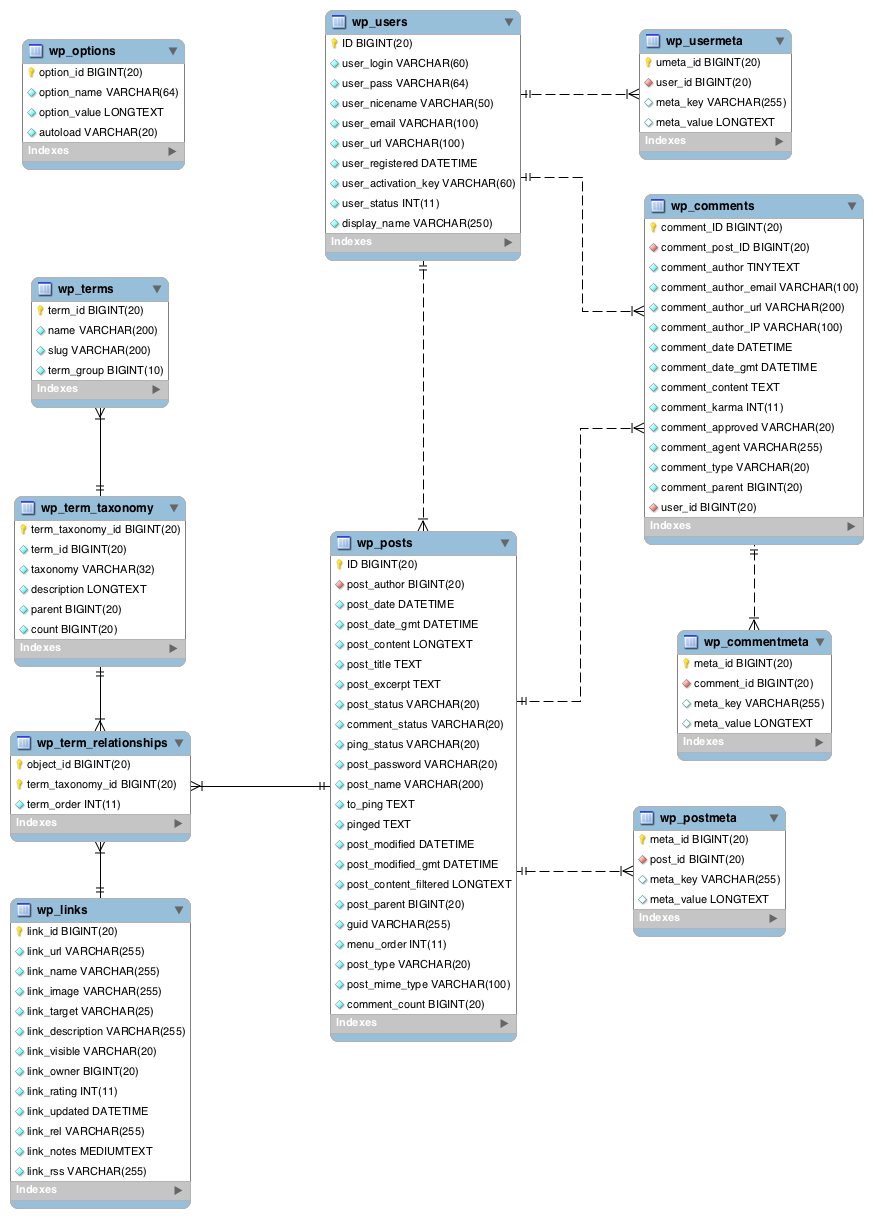
As you can see from the above schema, the comments texts are stored in the comment_content column which is a TEXT column, meaning a comment can only contain a maximum of 65535 bytes of data.
A typical exploit would look like the following:
<a href='x onclick=alert(1) AAAAAAAAAAAAAA..(multiplied so our comment contains more than 65k bytes)'>test</a>
Once taken back from the database would look like this:
<p><a href='x onclick=alert(1) AAAAAAA</p>
Some of you might have noticed that the resulting HTML tag isn’t complete, but this isn’t a problem for most modern browsers as most of them will simply patch it up automatically:
This bug then allows anyone to insert any HTML tag attributes to his hyperlink, including Javascript event handlers.
What You Can Do
There’s a few thing you can do to prevent getting hacked before there’s an official patch being released:
- You can disable comments on your site.
- Leverage a Web Application Firewall to filter good requests from exploit attempts.
Hopefully the WordPress team will release a patch soon.








36 comments
Any word or knowledge on whether using a commenting system – like Disqus here – helps here? Or, because it still allows comments to be injected, are users of that plugin just as vulnerable?
Hey Cat! This is Mike L from Umass Lowell.. I was just reviewing this article for one of my clients and to my surprise found your comment!
Dude! Hey! That’s wicked funny.
You should catch me online sometime. @rentageekmom on twitter if you want to grab my email address. 🙂
I also want to know if wordpress blogs using Disqus are affected. Also, would it help if all comments are moderated? Thanks.
As they said this is a method you as the admin can be the one attacked once you go to administer the comments so comment moderation is not a really good solution.
Thanks. Actually, I moderate Disqus comments via email or via the Disqus dashboard. With Disqus, I don’t have to administer comments inside wordpress via the admin dashboard. However, comments approved in Disqus will be synced to wordpress so that’s an area of concern. Any ideas?
Actually the Klikky Oy site says “the injected JavaScript apparently can’t be triggered in the administrative Dashboard so these exploits seem to require getting around comment moderation e.g. by posting one harmless comment first.”
So making sure all comments go to moderation, then only approving genuine comments will protect you.
WordPress has an option to allow ‘must have a previously approved comment moderations’, which won’t work, as a hacker could post a genuine comment, then come back to post the hack which bypasses moderation.
Does WordPress know about this? From the blog article you referenced, it doesn’t sound like WP is responding to them. I can disable comments for a day, but I can’t do it much longer than that. Can we count on a patch coming through?
WordPress is aware of the issue and is working on a patch. If you have Akismet installed, these comments will already be automatically flagged as spam.
Okay. I do have Akismet. I’ve routinely delete those spam comments to the trash. Should I just leave them for the time being?
So I simply shouldn’t check my spam queue then? Will it affect WordPress sites on 4.2 with Disqus installed?
The vulnerability should not affect the comment queue in the administrative panel. The only risk is when the comment is approved and the administrator subsequently views the comment on the post’s page. You can empty your spam as usual.
Thank you! In the meantime, I’ve disabled comments.
So can we safely view the spam comments in the spam panel, as long as we don’t approve the infected ones? I routinely get legit comments sent to spam so I check my spam queue regularly. Comments downthread are suggesting that even viewing them could be dangerous?
You can indeed safely view the spam comments in the spam panel (according to the researcher’s website) as long as you do not approve the malicious ones.
Thanks very much, Cedric!
I’m assuming the hacker would need to have an approved comment first otherwise this code would not appear without being approved by the Admin. Correct?
It entirely depends on how the site is configured. If you have the “Comment author must have a previously approved comment” option enabled, then yes :).
Updated, thanks.
I’m a huge fan of WordPress, and I don’t know how much work is involved to patch this, but it’s very disappointing to read they haven’t responded to attempts to notify them about this vulnerability. Particularly as WP have been so proactive recently in pushing updates, and working with Yoast, Sucuri and other plugin authors to patch vulnerable plugins over the last few weeks.
I’m sure virtually all website owners would prioritise security over functional improvements shipped with versions 4.1 and 4.2. Let’s hope this was some kind of communication breakdown.
Looks like WP just pushed out 4.2.1 – i guess / hope thats the reaction to this? anyone?
I run Varnish in front of our webserver, and can filter requests before they hit Apache. I’ve done this to block Shellshock as well as common hacking attempts.
I am wondering what the request might be – and then I could build a regex to deliver a 403 Error to any requests trying to exploit this. It’s not immediately obvious how these POST requests might look in the wild. I also suppose that Varnish can’t inspect POST requests – so it makes it a little difficult to block.
Any thoughts?
Maybe not the payload content, but perhaps you could put a rule in that limits request size (being that this is an overflow attack) for POST requests to the PHP comment post endpoint.
(BTW, care to share your VCL for shellshock etc?)
Does this affect the wordpress jetpack comments?
If you have Akismet running there is a good chance that the comments will get flagged as spam so do not check your spam queue.
Do you think the following .htaccess or apache config can mitigate the issue? thank you.
LimitRequestBody 65000
Thank you for this information, we will check our blogs for this problem.
cool
alert(“I am an alert box!”);
hello word
XSS
With Gain Credit Personal Loans, you can get instant loan/money for a
wide range of your personal needs like renovation of your home, marriage
in the family, a family holiday, your child’s education, buying a
house, medical expenses or any other emergencies. With minimum
documentation, you can now avail a personal loan at attractive 3%
interest rates. This is trust and honest loans which you will not
regret, Contact us via Email: gaincreditloan01@gmail.com
Hello Everybody,
I am Kristen Oh Lim I live in Baskent and i am a happy woman today? and i told my self that any lender that rescue my family from our poor situation, i will refer any person that is looking for loan to him, he gave me happiness to me and my family, i was in need of a loan of $45,000 to start my life all over as i am a single mother with 3 kids I met this honest amuslim man loan lender that help me with a loan of $45,000. he is a muslim man, if you are in need of loan and you will pay back the loan please
contact him tell him that Kristen Oh Lim that refer you to him. Contact Mr.Jubrin nelson via email: (globalteamlendingfirm@gmail.com)
Hello, I am Malissa Delh, currently living in New jersey city, USA. I am a widow at the moment with three kids and i was stuck in a financial situation in February last 2016 and i needed to refinance and pay my bills. I tried seeking loans from various loan firms both private and corporate but never with success, and most banks declined my credit. But as God would have it, I was introduced to a Man of God a private loan lender who gave me a loan of $85,000USD and today am a business owner and my kids are doing well at the moment, if you must contact any firm with reference to securing a loan without collateral , no credit check, no co signer with just 3% interest rate and better repayment plans and schedule, please contact Mr Jubrin Nelson. He doesn’t know that am doing this but am so happy now and i decided to let people know more about him and also i want God to bless him more.You can contact him through his email: globalteamlendingfirm@gmail.com
alert(“XSS”)
WordPress fix this
Comments are closed.