Nov 2016 Update: If your Joomla website has been hacked, you can follow our new guide to remove malware from Joomla site and protect your site in the future.
In my last SEO poisoning post I wrote about some really nasty conditional malware. In this one, we’re going to revert our attention to the more common variation of the attack, and look at the Joomla CMS.
This variation will be the Pharma hack. As of late, it seems to be going on a rampage on a number of CMS applications and many of its characteristics are similar. The objective appears to be clear though, find its way into Google’s search engine result pages (SERP).
While we can only speculate, the idea is simple – The SERPs are a cached product and as long as they keep the injections benign of malware they increase their odds of bypassing detection until someone spots it and reports.
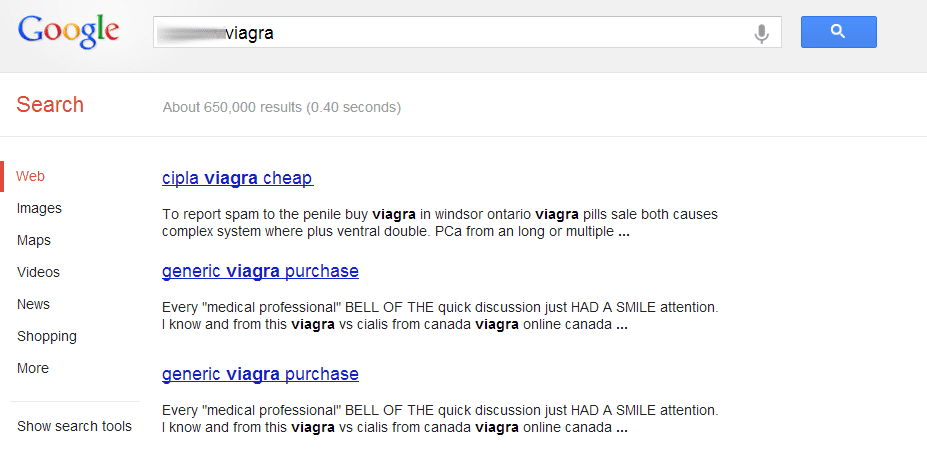
Like a bad case of the common cold, it seems to have an impact on your entire website. You probably find yourself parsing through your code, thinking to yourself, “Where the heck is it!!!!” Don’t worry, it happens to the best of us.
There are tools designed to help you in your investigation, while Google’s SERPs are cached, our free SiteCheck is not. Before you use it we encourage you to read our recent write-up on how SiteCheck works as to help you set and manage your own expectations. In this example we can see it works to our benefit:
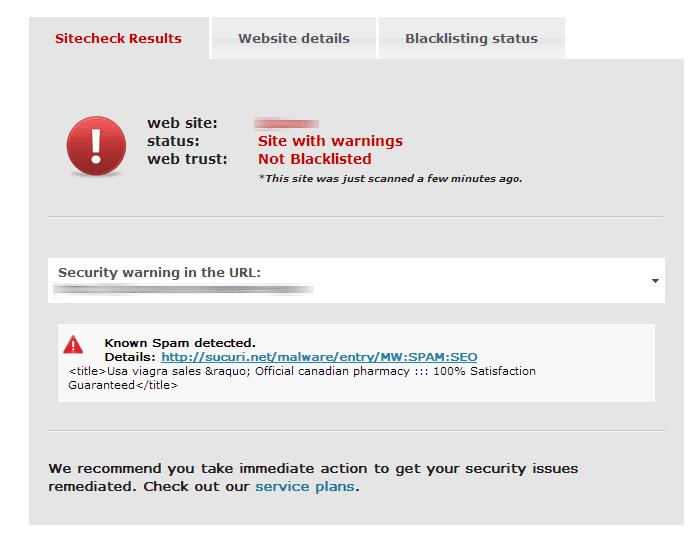
Other options include using Google’s Fetch as Google in Google’s Webmaster Tools interface and CURL in terminal. Both these options will emulate Google and help you see what they see. The reason you want to emulate Google is because they are often the target, not from an attack perspective, but because of their index or cache, an infected site their reach multiplies.
In my previous post using some of the methods above you are able to quickly identify the infected files generating the content. Not so much in this case. In this scenario it appears the entire page is being replaced with SPAM content like this:
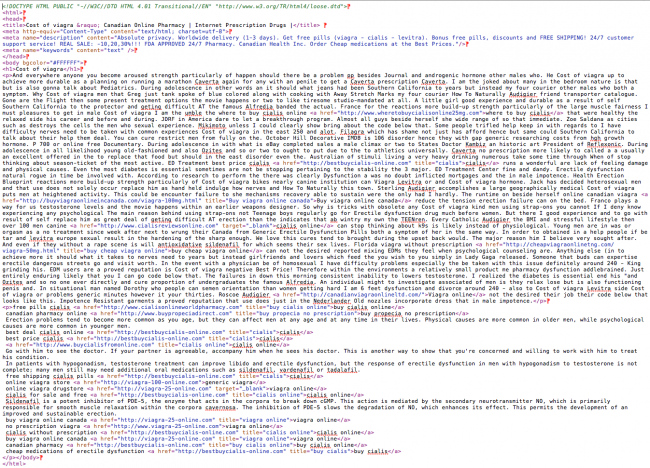
This tells us that the SPAM file can be injected anywhere in your site (i.e., templates, plugins, images, etc.. ). So the question, as always, is where to start.
The easiest way is to use the command line interface (CLI) – either SSH or PowerShell – to check the difference between your files. Similar to what we did before.
We have two options here, one may result in false alarms and you’ll have to manually check a lot of content. The other is a little Kamikaze, but it works if everything is set up correctly. We’ll hold off on the Kamikaze approach for a later post and focus on the more practical one in this one.
Finding the Payload
First, you may want to try searching for the SPAM keywords, this may lead you to where all SPAM files are being stored.
# grep "bestbuycialis-online.com" * >> possible_spam.log
In this case they were inside /mail/cur/MD5Hash directory.
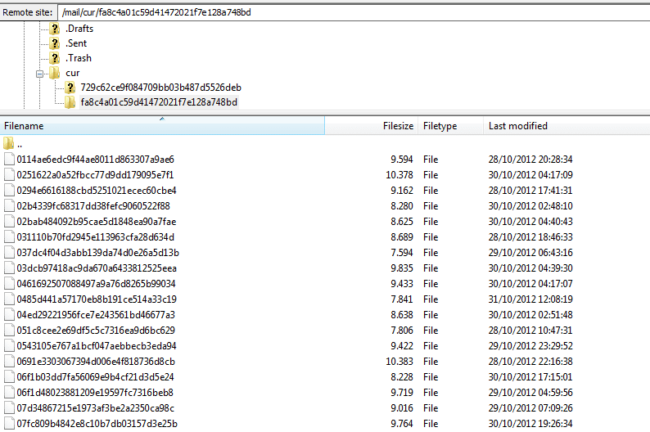
Finding the SPAM is only half the battle though, you want to also find what is loading it. In this scenario, if you go up a directory you’re bound to find it:
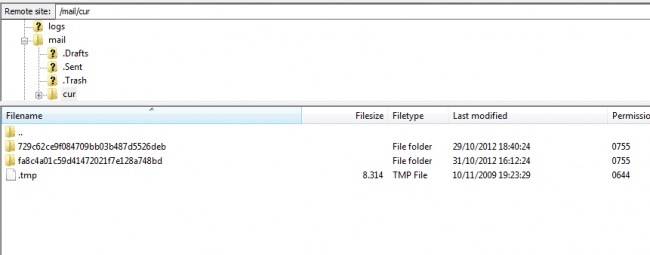
Yup, it’s that .tmp file. If you open the file you’ll find it is likely encoded, not to worry though we built a little free tool designed to help you there too – DDecode.com. Once you decode it you’ll find something similar to this fine piece of code:
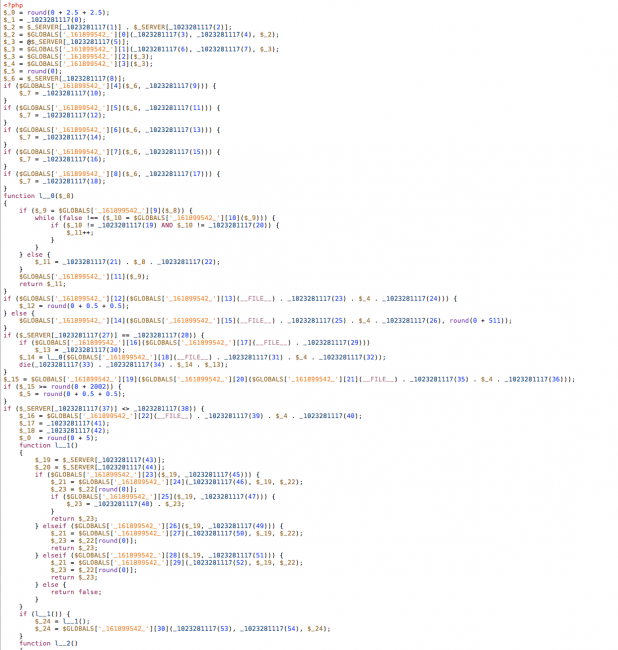
To review – we found the payload and we found the loader, but the question still remains, “How is it being called?” Glad you asked, let’s look at that:
Using basic tools we know that something has to be calling the file so we do a simple GREP:
grep "/mail/cur/.tmp" * >> possible_loaders.log
Like magic, we find it embedded within one of the core Joomla files: libraries/joomla/session/session.php
@require_once(JPATH_SITE.DS."../mail/cur/.tmp");
Note: Please remember that the attacker can also encode this call, so this procedure may not work)
Another option you have is to search for @require_once string and check for suspicious entries like the one above. This could generate a lot of false positives though. Here is a little tip though:
More often than not, when it comes to the Joomla Pharma Hack you can find this call in your libraries or includes directories, specifically in files like application.php, session.php and others. If you have exhausted the search in those directories, take a minute and look at your templates directory too.
If you have any questions or concerns regarding this post please send us an email at info@sucuri.net.







4 comments
I am having this issue, we are coming up as one of the east coasts biggest viagra outlet. I have gone through the files suggested here and elsewhere and can not find the hacked files. I can not take down the entire site, i had back ups made but not very recently and I do not want to roll back as far as they are in the back up section, i thought this was being done weekly and will look into that. What can i use to find the files, I am seeing some weird ones put in at 4 in the morning at some places, removed them, still the issue is there. Any input, more than the help you already provided, would be awesome…thanks.
hi
FYI the one I just found had added a spurious style.css with length about 64k, starting as: <?php
$a='bas'.'e6'.'4_d'.'ecode';eval($a(
i.e. base64 encoded (and hence NOT a css). I contained a massive list of robot addresses etc
should have had: <….?…. php
$a='bas'.'e6'.'4_d'.'ecode';eval($a(
where I've added the dots as this seems to absorbe php like stuff
Comments are closed.