For the last few days, we have had some customers come to us worried thinking that their websites were compromised with some type of pop-up malware. Every time they visited their own site they would get a strange pop up:
“Please stop hotlinking my easing script — use a real CDN instead. Many thanks”
What is going on?
We did some Google searches and found hundreds of threads with people worried about the same thing. Out of no where, that pop-up was showing up on their web sites. Were they all hacked?
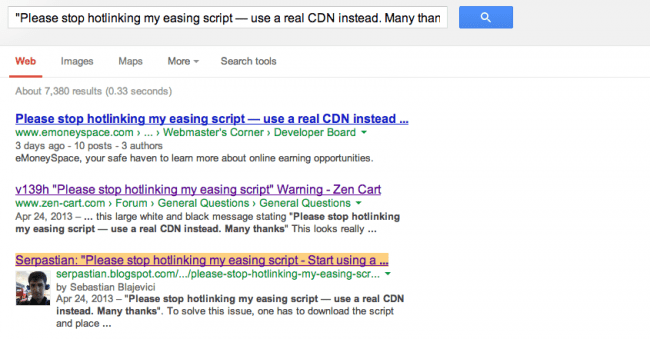
Through further research we found that all of the sites in the results had a JavaScript include from: http://gsgd.co.uk/sandbox/jquery/easing/jquery.easing.1.3.js. This file is part of the popular jQuery Easing Plugin. It seems the author of that plugin got upset that many people were linking directly from his site, and modified the content of that file to give that warning instead. He posted an explanation on his site about it:
Popup? If you’re coming here because of a popup on your site I’m sorry, but the increased hotlinking has caused me issues with my hosting company so I’m taking steps to try and sort it out. Please upload the script to your own server and update any urls pointing to gsgd.co.uk to use that version of the file or you could try using the above url for CDN (though this currently only has the 1.3 easing script, look at http://cdnjs.com/ for more info and maybe try and add any missing files/versions still in use).
Please also note, I have no problem with anyone’s use of the plugin without my knowledge or permission, it’s just the hotlinking that’s causing me a headache.
Who Really owns your site?
Most users had no idea that they were even using that plugin. Most developers that include it probably dodn’t even think about the hotlinking issue. It seems that plugin documentation used to give examples pointing to gsgd.co.uk, so the developers just copied and pasted directly into their sites.
What was more worrying to our client was the power that someone else had over their site.
You are not really the only owner of your site
Every time you add a remote JavaScript (or widget or iFrame) to your site, you are giving the server that houses that code full control of what is displayed to your users. If their servers get compromised, your site will be compromised as well.
Can you imagine if the author of the Easing Plugin was malicious? Instead of just that pop-up, they could have added a URL redirect to send all your users to any site they of their choosing (SPAM, porn, you name it). What if their server was hacked? The attackers could have added malware and it would have loaded to all your users.
This is very common. For example, look at the techcrunch.com website (big news outlet). They load JavaScript from all these domains:
http://o.aolcdn.com/ http://pshared.5min.com/ http://js.adsonar.com/ http://scorecardresearch.com/ http://tctechcrunch2011.wordpress.com/ http://platform.twitter.com/ http://connect.facebook.net/ https://apis.google.com/ http://cdn.optimizely.com/ http://r-login.wordpress.com/ http://cdn.insights.gravity.com/
So their security is not only dependent on their own site, but if any of those 11 sites they include in their site gets hacked, it will affect their users as well.
They are not alone. Our own blog, includes code from:
http://disqus.com http://s.gravatar.com http://stats.wordpress.com http://connect.facebook.net/
So our blog security is also dependent on those 4 sites (Facebook, Disqus, Gravatar and WordPress). Including code from Google CDN,Twitter, Facebook or any major publisher is likely low risk being they have a pretty good level of security. That said, there is still a level of risk you are accepting for you and your visitors. Another thing to consider is the risk increases significantly when you include code from smaller and less known locations.
The Solution?
If you are using this plugin, just remove the include from gsgd.co.uk, download the plugin and store it locally. That’s an easy fix.
I also recommend that you look at the source of your site to see what else you have included.
Do a view-source: on your browser and search for <script or <iframe to see what is being loaded. You might be surprised. Our SiteCheck Scanner also prints a list of JavaScript and iframe links we found, so you can use that as well.









11 comments
Thanks for the insight. Never realize about this before. Yeah, we’re not 100% owner of our own website.
Very interesting. Saw this on a site this morning. Now I know!
Maybe a console log message would have been a better solution… A popup is just in your face and wrong.
So is stealing someone else’s bandwidth. Image hotlinkers get a replacement image that points to the origin domain, at least this guy didn’t just move the script or stop the linking.
And how many people look at the console on a regular basis after the site is up and running?
Stealing bandwidth is bad. The question that should be asked is – Was it clear to users that they were stealing?
I am not justifying hot-linking or stealing bandwidth as appropriate, because it’s not. However, you’re assuming users knowingly did this. Even then, is a pop-up appropriate without notifying users before they load the plugin? I would argue no, and some would classify this as malware (Defacement maybe?):
“malware refers to software programs designed to damage or do other unwanted actions on a computer system.”
It’s an unethical approach to a problem that he contributed to by not setting appropriate expectations before usage, and not properly documenting in the demo/tutorials. Further, adding a pop-up on someone else’s website without them knowing is not really a solution to the issue, and although it may reduce bandwidth usage, it won’t stop it.
If you’re going to distribute a tool like this for general public consumption, you need to set expectations and implement controls before a user commits to using it. There are places to host at lows costs or even repositories that can be leveraged to reduce the overhead.
Further, he could have also offered the script for download in a way that limits hot-linking altogether, requiring users to load it in their own environment.
Again, not saying it doesn’t suck. In my opinion, this is a planning and sustainment issue on the side of the author, not a problem caused by the users that justifies pop-ups as the resolution.
I did write a longer reply, but it got eaten up by your website. In short:
I’m the owner of the plugin and I felt that the information in this response and the original article are somewhat misleading so I’d like to clarify a few points.
I never offered the script in such a way that copy and pasting would create a hotlink to my site and the site has always offered a link to the script with the words “download” next to it. Other people created plugins and themes which did however have the hotlink (some of which being paid for plugins).
Users can do their own research but I think the “hundreds of threads” mentioned is a vast overstatement.
The file isn’t part of the plugin, it IS the plugin.
The possibilities for harm outlined above ignore many more dangerous issues, such as your website users privacy and security.
I only did this after the hotlinking, which until that time I was unaware of, reached a point where my hosting company shut down my website. Overall, given the position I was in, I do feel justified in the course of action not just by the overwhelming apologetic response I have had, but by the fact this had reached a point where there was no other practical way of getting in touch with the many thousands of website owners doing this. I’m not sure what “planning and sustainment” I was supposed to do in the situation I found myself in.
I would agree with the main thrust of the article, that if you include content on your site that you do not own you are opening yourself up to attack. I do think the attack possibilities outlined are only scratching the surface of the possible dangers to your site and your users.
Of course, the alternative option was that the plugin authors site was just down, so a 404 delaying page load plus the functionality being broken. Can’t say I blame George here, it’s a hard situation to resolved without breaking a site. Maybe the messaging could have been more fine tuned, but we’re not all Ernest Hemingway.
You have done nothing wrong. Hotlinking is not OK. And any developer who doesn’t check the sources of the scripts he uses is an amateur. Of course scripts should always run from your own server so that you have full control. People should be happy that you are an honest dude. Had you been someone else, this could have resulted in far more serious consequences. Keep it up!
This blog is really nice and informative. We are pleased
to know this blog is really helping people.
Adding hotlink protection using .htaccess would have been more practical, but I like this solution of executing an unexpected script.
He probably did. My guess is that he still uses the script himself, but added hotlink protection with htaccess so it would display a different script, which shows the error, to outsiders.
Comments are closed.