We clean hundreds and thousands of infected websites, a lot of the cleanups can be considered to be somewhat “routine”. If you follow our blog, you often hear us say we’ve seen “this” numerous times, we’ve cleaned “that” numerous times.
In most cases when dealing with infected websites, we know where to look and what to remove, generally with a quick look we can determine what’s going. Despite our experience and passion for cleaning up a hacked website, there are always surprises lurking and waiting for us, almost every day.
Some of the most interesting routine cases we deal with are often websites with SPAM. SPAM is in the database, or the whole block of SPAM code is stored in some obscure file. We also deal with cases where the SPAM is loaded within the theme or template header, footer, index, etc. Sometimes these SPAM infections are conditional (e.g. They only appear once per IP), sometimes not.
More often than not however, these infections is not too difficult to identify and remove. In the case we’re writing about in this post, we were able not only to remove malware, but also take a look at what’s going on behind the curtain.
The General Picture:
We started to find malicious files with name consumer.php. Sites with this malware were flooded with spam. Simple removing of consumer.php caused the PHP error and the site didn’t load properly. Right, it has to be loaded somewhere. Based on the PHP warning and little effort, we found several files where the malicious code was included:
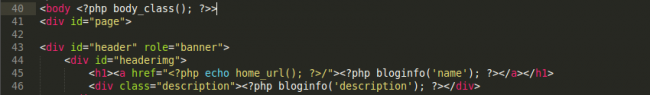
Looks benign, right? Are you having a hard time spotting the offending code?
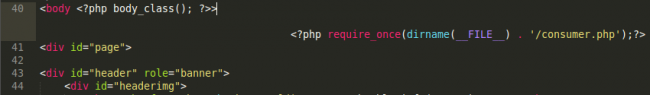
Check it out again with word wrap enabled 🙂
Until now, it looks just like yet another regular old SPAM case. However, we still want to make sure nothing is missed, and that the site is properly cleared.
Behind the curtain:
In this case, we noticed an interesting WordPress plugin called Pingatorpin. As we dug in a bit, we found some interesting facts:
- The plugin was not in the official repository
- All of the plugin headers were fake
- Searching for the plugin on Google returned a pretty large number of sites with this “plugin” installed
- The sites using the plugin all had similar files
- All of the sites using the plugin showed up infected with SPAM when scanned with Sucuri SiteCheck
We scanned quite a few sites that were using the plugin, the results were interesting. Here’s an example:
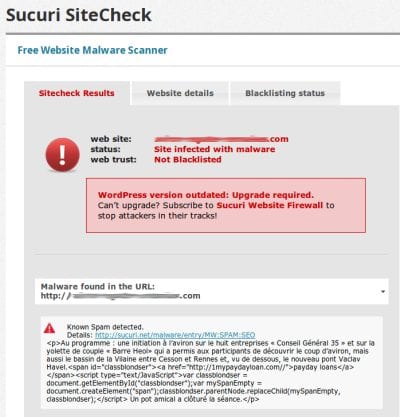
There’s a surprise – A ton of sites with same malicious WordPress plugin, all infected with SPAM. We just found the source of the SPAM.
All of the files in this plugins folder were actually malware.
- config-generator.php – Creates the config file serializing the array.
- executor.php – Responsible for injecting require_once() into the files and logging which file is infected into files.dat.
- remover.php – Malware cleanup script which is pretty interesting.
- consumer.php – The payload which will get the content from the config.db file, process the content, and echo it into the pages it wants to infect.
Yes, that stinks, but it’s pretty straight forward. I know, I know, yet another SPAM infection, this time with a pretty interesting composition using a fake WordPress plugin. Maybe another thing worth mentioning here is you need to make sure you’re checking your site to see what’s loaded and running. Our WordPress plugin included with our Malware Cleanup service would have notified you when this was added.
Beyond that, keep your software updated, use safe passwords and if you don’t know what to do.. Let us, Sucuri, take a look. It’s our passion 🙂










4 comments
Hello, please hide the excerpt of the post in the scanner screenshot, we can google it and finf the website (i did it …) Thank tou for this discover Peter 😉
Just a great post I would say! I love Sucuri !!
Thanks for giving me the useful information. I think I need it. Thank you
Any info on how the wp-content/plugins/pingatorpin directory was uploaded? I’m assuming since you are specifically calling it a plugin that it must have been installed through the wp-admin interface which means their one of their admin user’s password was compromised. Were their signs of a bruteforce attack to wp-login.php or did they get in after their first POST to wp-login.php?
I clean dozens of WP sites a week and thankfully haven’t run into this one yet. Currently still dealing with the wpppm plugin(loads spam ED page instead of a WP 404 page) and its variants along with the massive ED spam redirect injection that hits almost every index.php, wp-config.php, and header.php that it can find.
Comments are closed.