Security Risk: High
Exploitation Level: Remote
DREAD Score: 7/10
Vulnerability: Privilege Escalation
Patched Version: 1.9.51
If you’re a user of the UpdraftPlus plugin for WordPress, now is the time to update. During a routine audit of our Website Firewall (WAF), we detected a “nonce” leak vulnerability affecting the UpdraftPlus WordPress plugin. The vulnerability allows a malicious actor to perform various operations that he normally wouldn’t be allowed to, such as uploading files on the target server, downloading the site’s backups and retrieving WordPress secret keys.
What are The Risks?
If you’re hosting a WordPress site that uses the free version of UpdraftPlus and allows users to create accounts (ie. subscribers), you’re at risk. A logged-in attacker could use this bug to leak a specific token (which WordPress calls a “nonce”) that can be reused to trigger other mechanisms within the plugin, for example uploading arbitrary files on the server (if they pass WordPress extension filters) and downloading the site’s file and database backups, which could result in a site compromise.
Technical Details
The plugin’s admin_action_upgrade_pluginortheme() method was hooked to WordPress ‘admin_action_’ action, which can potentially be executed when a logged-in user visits a page in /wp-admin/ that includes the /wp-admin/admin.php file and has the ‘action‘ GET parameter set to a specific value.
![]()
As you can see from the above snippet, the target method is hooked to both ‘admin_action_upgrade-plugin‘ and ‘admin_action_upgrade-theme‘ hooks. These can be directly called by adding “?action=upgrade-plugin” or “?action=upgrade-theme” to the user dashboard’s URL.
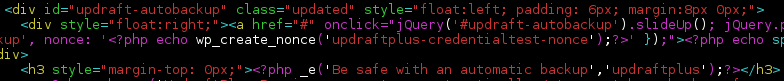
Doing this would result in the plugin leaking the ‘updraftplus-credentialtest-nonce’ nonce, which was also used at several other places in the code, namely in the plugin’s AJAX handler:
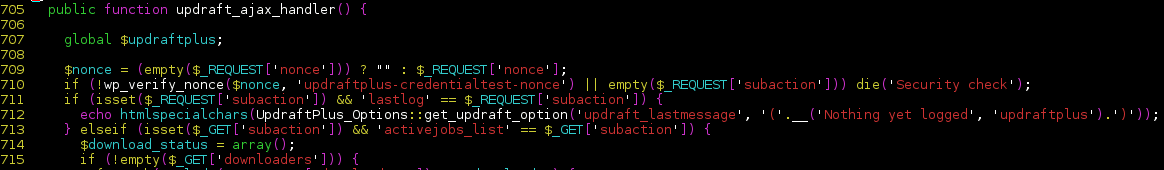
From there, an attacker could do a lot of things like displaying a phpinfo() page including all of the website’s defined constants (which includes WordPress secret keys, database credentials and prefix), executing every hook present in the current context and downloading the site’s backup files.
Brief comment on UpdraftPlus’s way of handling the issue
We’d like to take a few lines to mention that the plugin’s developer was exceptionally effective at understanding what the issue was, patching it and notifying his users of the issue. This is a great example of what people means when they say no software can be 100% secure. UpdraftPlus was (and still is) a very secure piece of software, overall. We can say for sure that this bug was a result of a misunderstanding of how ‘admin_action_‘ hooks could be used, definitely not from a lack of WordPress security best practices.
If you are a developer, you can read his blog post for an example on how to deal with vulnerability disclosures (only 12 hrs after we notified them).
Update as soon as possible
Again, even if you’re not necessarily affected by this particular vulnerability, we suggests you to upgrade to the latest version. If for any reasons you cannot do this, we highly recommend you to have a look at our Website Firewall (WAF) to get rid of the risk this vulnerability (and many others) represents to your site.










3 comments
For what duration of time/version numbers was this problem out there?
Does it affect the Pro version as well?
In my membersite, historically, I have no users except customers. However, recently more WP users have been registering and not sure where they are gaining access… assumed it was probably an open “comment” reply area. These “new users” appears only in the last month whereas previously zero on a site up for 7 years.
UD has been a life-save product for me and glad to hear other perspectives that the response was appropriate for remedying the problem.
just read the UD site which answered most of the question here…
the Premium versions were not affected.
Pretty amazing they got the fix out in 12 hours.
and MUCH APPRECIATION to Sucuri for discovering this!
I guess that explains how someone was able to install malware on my site last week. Thanks for catching that… I’m now updated, and a little wiser too.
Comments are closed.