Your website’s search results and rankings are vital to the success of your online business. Better search visibility equates to more traffic — which results in more opportunities to convert leads into customers.
And while it may be tempting to game search engine algorithms to come out on top, there’s a hard line in the sand when it comes to the right and wrong ways to optimize a site for search. Black hat SEO (shady techniques that go against search guidelines) is definitely not something you want to practice if you care about the long-term growth and success of your website.
In this post, we’ll outline what black hat SEO is, the tactics and techniques used in black hat SEO campaigns, how the dark art of black hat SEO can impact your website and rankings, and how to report it to search authorities.
Contents:
- What is black hat SEO?
- Redirects
- Cloaking
- Doorway pages
- Keyword stuffing
- Link schemes and paid links
- Comment spam
- Why should I avoid black hat SEO on my site?
- How to get rid of SEO spam
- How to report black hat SEO
What is black hat SEO?
Black hat SEO (or black hat search engine optimization) is the practice of unethical techniques that go against search engine guidelines to improve a site’s rankings in search results.
Instead of creating helpful content, improving a site with quality information, or providing experiences that solve for the user, shady tactics are employed to get search algorithms to rank a domain’s web pages. These dishonest practices rarely keep the needs of the searcher or website visitor in mind.
While black hat SEO can create a short term improvement in rankings, they often damage a website’s presence in search engines over the long term. They can even lead to a site being blocklisted or completely omitted from search results. This is why it’s imperative that you protect your site from bad actors and avoid use of these techniques on your own domains.
What are black hat SEO techniques?
Often used by bad actors and shady marketers, black hat SEO techniques can include link manipulation, keyword stuffing, comment spam, cloaking, and unwanted redirects.
If your website has recently been hacked, you may find one or more of these techniques added to your domain in an attempt to generate more traffic to the attacker’s domains or help rank third-party websites.
Let’s take a closer look at some of the more common techniques used in black hat SEO.
Redirects
A redirect (also referred to as a URL redirect or URL forwarding) is a technique used to redirect a website visitor to a different URL. Redirects are commonly used in SEO to pass authority from one page to another or consolidate two or more pieces of content.
In black hat SEO, however, redirects are used outside of the usual intended purpose to trick search engines — for example, to redirect a web page with high authority to a completely unrelated page so that its position is boosted in Google’s search results. Or to redirect site visitors to one page and search engine crawlers to a completely different one.
These sneaky redirects should be avoided as they are a clear violation of Google’s search engine guidelines.
If you encounter unexpected redirects on your site, be sure to investigate further. In some cases, site owners don’t know that they’ve been hacked and have black hat redirects on their site until they start receiving complaints about the unexpected behavior from site visitors and customers.
![ois.]is redirect malware variant uses allowedHours to define redirect frequency](https://blog.sucuri.net/wp-content/uploads/2022/11/allowed_Hours_used_to_define_redirect_frequency.png)
Cloaking
Cloaking is a technique used to show one piece of information to site visitors and a completely different one to search engines. Black hat SEO artists and attackers use cloaking to manipulate search engine rankings for terms that are unrelated to the website’s original content.
On hacked websites, cloaking is often used to show spam content to search engine bots while concealing it from regular site visitors. It’s also used to redirect search traffic to other third-party websites.
For example, an attacker may compromise a website and inject malicious scripts that show content with spam keywords for Google, while regular visitors continue to see the unmodified page. Or the script might insert spam and keywords only when a user agent belonging to a search engine is detected.
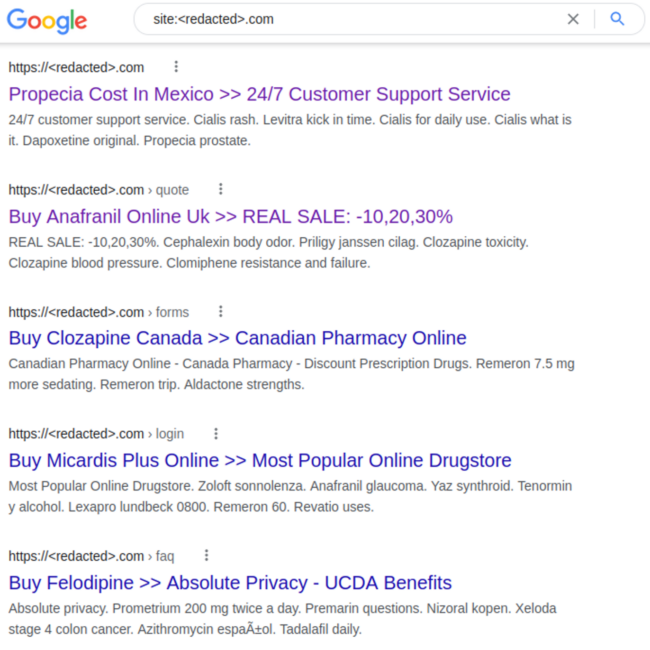
To further highlight this example, here’s a small snippet of cloaked pharma spam. Website visitors won’t notice it on the page, but search engine bots may pick it up and pollute search results with these unwanted pharmaceutical keywords.
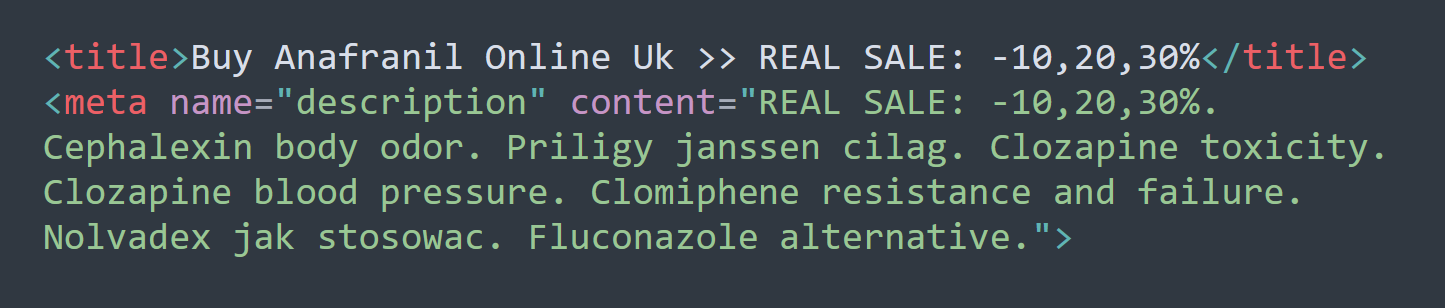
If left unchecked, cloaking can seriously harm a website’s rankings. Search authorities are known to penalize sites that use this shady behavior to try to trick their algorithms.
Doorway pages
Doorway pages are spam pages designed to rank for specific search queries and manipulate searchers by sending them to another different page.
Also referred to as jump pages, gateway pages, or portal pages, spam doorways are often packed full of long-tail keywords and lead site visitors to other intermediary pages that aren’t valuable to searchers in any particular way.
In some cases, doorway pages use malicious redirects, cloaking, or the meta refresh command to send visitors (but not search engine bots) to an unrelated destination. They are known to use bait and switch techniques that make the page rank for certain keywords to compel users to click on the search result — but as soon as they click, searchers are redirected to an entirely unrelated page.
More sophisticated variants like content rich doorways use seemingly useful content with clear calls to action that trick visitors elsewhere.
Pages found to exhibit these techniques can receive a Google penalty (manual action) as they add little to no added value for web searchers and site visitors. And they’re downright malicious if they redirect victims to scam pages, phishing, or malware downloads.
Keyword stuffing
Keyword stuffing is the practice of packing an enormous number of keywords into meta tags and content in an attempt to inflate a page’s search rankings.
According to Google’s Spam Policies for Google Web Search, stuffed keywords often appear out of context, unnaturally repeat words or phrases, and don’t provide added value to searchers.
For instance, take a look at this keyword stuffing example:
Are you looking for discount laptops? If you’re looking for discount laptops, look no further than this site. Our discount laptops website is the best place to order your new discount laptops. Feel free to check out our selection of discount laptops from our discount laptops selection for the cheapest discount laptops.
Painful to read, right? It’s worth noting that search authorities’ algorithms have been working for years to spot this black hat behavior.
So, if your site is found to be leveraging keyword stuffing techniques like the ones in this example, it’s likely that search algorithms will quickly demote your rankings.
Link schemes and paid links
Backlinks are an excellent way to tell search algorithms that you’re a trustworthy source. Relevant, high quality links can help drive more traffic to your website and are an important credibility indicator for search engines.
But authorities strictly ban the practice of buying and sellings links. And that includes giving, taking, or even exchanging links for free products or discounts. If this behavior is detected, Google has clearly stated that they’ll penalize both parties involved.
According to Bing’s Webmaster Guidelines:
Abusive tactics that aim to inflate the number and nature of inbound links, such as links buying participating in link schemes (link farms, link spamming and excessive link manipulation) can lead to your site being penalized and delisted from the Bing index.
In fact, Google is so serious about cracking down on link manipulation that they’ve even set up a service to report paid links. So you’ll want to steer clear of this shady marketing practice at all costs.
Link manipulation happens to be one of the most common types of hacks that our remediation team finds and cleans from infected sites. In many cases, these SEO spam infections are found in the form of hidden links that hackers inject into legitimate website pages that try to help rank unsavory content like pharmaceutical spam, gambling, replica knock-off products, and pornography.
Comment spam
Comment spam haunts forum administrators and website owners alike. These unwanted post comments are often not related to the original site in any way — and often contain inappropriate material or unsavory keywords for pharma spam, dating sites, payday loans, or even adult content.
As a website owner, you’ll want to be extra careful with how comments are displayed on your site. In many cases, black hat advertisers and bots generate random text content littered with advertisements, spam content, and SEO links. And spammers can use automated scripts and tools to post millions of spam comments across as many blogs or sites as their tools can find.
Nobody likes looking at spam. And nobody wants to read irrelevant spam content on blog posts and web pages — it creates an unpleasant experience that adds zero value to the content.
Ultimately, you are responsible for any content that ends up on your domain. So be sure to take measures to prevent spam on your website if you do end up allowing comments or user generated content.
Why should I avoid black hat SEO on my site?
If you’re trying to maintain good rankings and grow a reputable, legitimate website it’s best to steer clear of black hat SEO techniques.
Black hat tactics can quickly get your website an algorithmic or manual penalty by Google, Norton, SpamHaus and other search authorities. And if there’s other evidence that your site has been hacked, it can even lead to blocklisting.
That means avoiding shady tactics in your own marketing and protecting your site from hackers who may try to piggyback off your hard-earned rankings or redirect your website’s traffic for their own purposes.
How to get rid of black hat SEO spam
Nobody wants to be in the penalty box, especially when it comes to their website rankings. If you’re recently discovered some shady or unexpected SEO tactics being used on your domain and you or someone you know didn’t implement them, this could be an indicator of compromise.
Here are some steps you can take to pinpoint a hack and recover from penalties.
1 – Restore your website from a backup.
Every website owner should have a solid backup plan. This way, you can easily revert back to your last known good configuration in the event of a problem. Users with SSH access can even use WP-CLI to backup a WordPress website for free.
If you don’t have a backup to revert to, follow along for further instructions.
2 – Inspect URLs in Search Console.
Check your pages as Google sees them with Search Console. Login and navigate to the URL inspection tool, then click Test Live URL to see the tested page results.
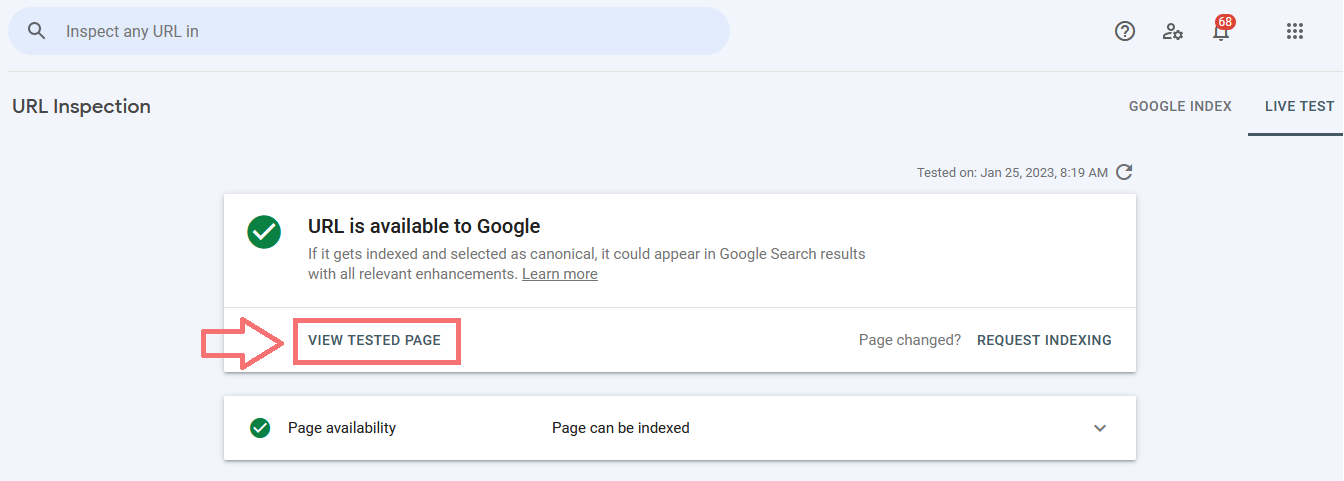
Alternatively, you can emulate the Googlebot user-agent in your browser to check your pages.
3 – Review Security Issues.
Search Console has a handy Security Issues tool to help you check for hacked pages on your website. Note which pages have flagged as containing SEO spam or other problems.
4 – Check your website logs.
Review your website logs to check for suspicious or unusual activity. Pay close attention to new user creation, post modifications, and any unexpected changes to plugins or themes.
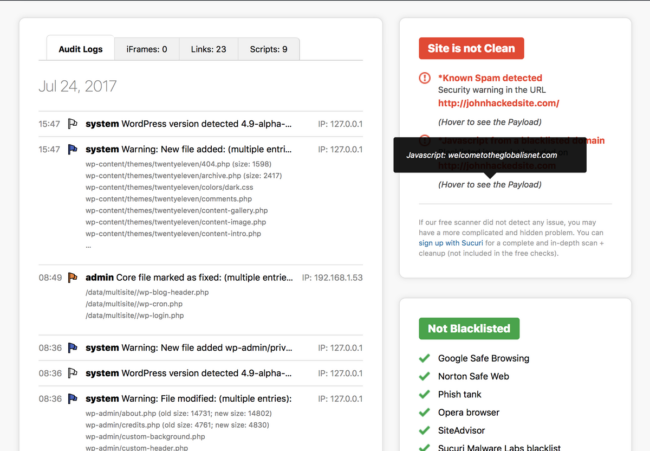
5 – Scan for spam.
Use the free SiteCheck website scanner to remotely detect suspicious code and SEO spam on your website.
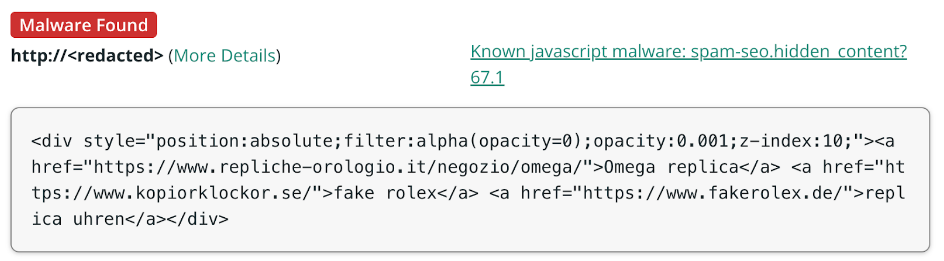
However, in many cases the database will be infected, so you’ll need to dig deeper than a cursory remote scan of outward facing website files.
6 – Remove unwanted spam posts, tags, and comments.
If you are comfortable modifying your database, you can use PHPMyAdmin or Adminer to search for spam.
At the end of the day, you’ll still need to patch the hole that allowed your database or website to get infected in the first place. If you need help, our team of security analysts can assist you with malware cleanup and removal.
7 – Clean up search engine result pages.
Once you’ve eradicated the SEO spam and cleaned up the infection, you’ll need to resubmit your site back to Google.
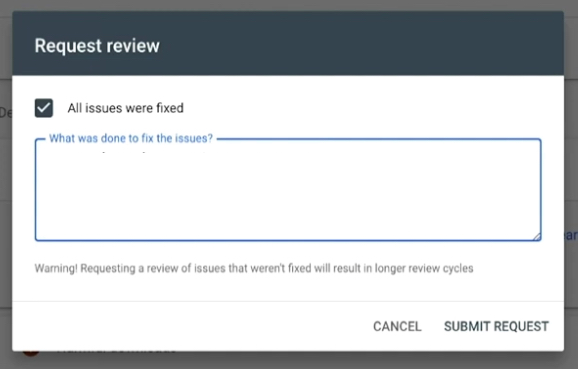
To request a review:
- Navigate back to Google Search Console.
- Click on Security Issues.
- Select Request a Review.
- Describe the steps you took to fix the problem.
- Click Submit Request.
You’ll want to provide a thorough description of the steps you took to remove the issue.
For example:
“I located and removed the malicious JavaScript injection that was injecting SEO spam and redirecting users to phishing sites. I then updated my plugins and website software and changed my passwords.”
And be sure that the issue is completely resolved before you submit your site for review. If it’s not, resubmitting again could result in a longer wait.
It can take days — or even weeks — for your entire site to be recrawled. You’ll need to exercise a bit of patience here.
How to report black hat SEO
There are two primary reasons why you might want to report black hat SEO.
Hacked site:
If your website has been hacked and littered with SEO spam, you’ll need to clean up the malware infection first. Once the issue has been addressed, resubmit your website to Google and request a review to have your site unflagged.
Spam links:
Any victim who’s been the target of a black hat spammy link campaign will need to tackle the issue head on.
If your site has received a manual action or penalty for shady backlinks, you’ll want to ask the other site to remove those links to your domain. But if you can’t get them removed for some reason or another, you can use Google’s Disavow Links to your Site feature. Exercise caution with this tool, as it can potentially harm your site’s rankings.
Just looking to report spammy web results or spam content that you’ve recently encountered somewhere? No problem! You can also file a webspam report with Google to report the issue.
But keep in mind that falsely reporting a competitor for spam is yet another technique that falls under black hat SEO.