We have recently been notified of phishing emails that target WordPress users. The content informs site owners that their database requires an update and looks like this:
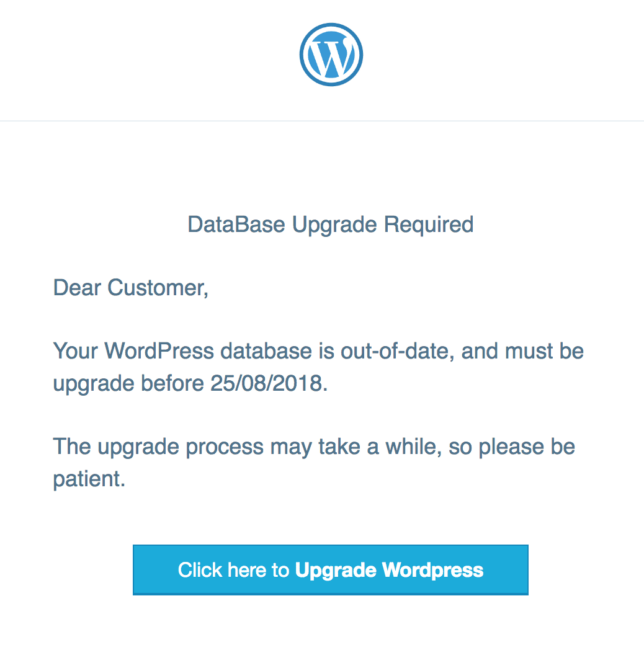
The email’s appearance resembles that of a legitimate WordPress update message, however the content includes typos and uses an older messaging style. Another suspicious item in the content is the deadline. WordPress wouldn’t define deadlines without a valid explanation, and hosting providers wouldn’t either (if you believed the email was from them). The use of timestamps in a European format may be another suspicious sign, especially for those residing in the US.
The footer of the emails mimics the one used by Automattic (the parent company of WordPress.com, Jetpack, WooCommerce), but the link also points to a phishing page on a different hacked website (which is again located in the /so/ subdirectory).
Fake Upgrade
If you click on the “Upgrade” button, a fake WordPress login page opens ready to collect your credentials. That page was created on a hacked but legitimate website. In one sample, it was in the /lop/ subdirectory, and in another case it was in the /so/ subdirectory.
Once you enter your credentials and click the “Log In” button, you’ll see the following screen asking for your site’s address and username. This is suspicious because it doesn’t make sense, a user will have already entered their credentials on the previous step. It’s also not entirely clear if they want you to re-enter your WordPress credentials, or if they’re looking for your database username.
Clicking on the “Upgrade WordPress Database” button completes the final step of the attack and sends your credentials and website address to the attackers.
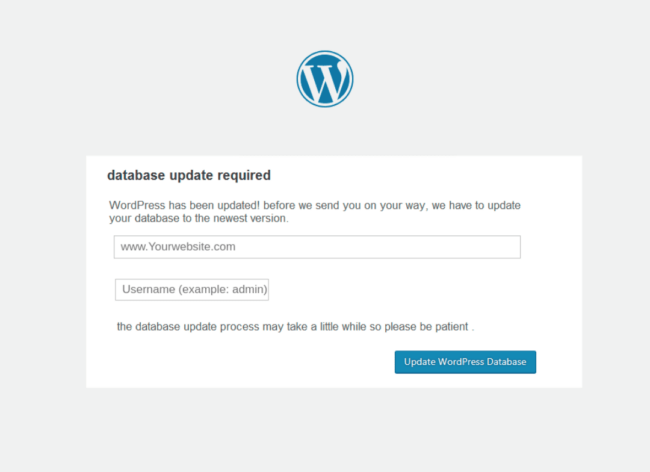
This explains how the bad actors are obtaining the site addresses and associating them with the stolen credentials.
Headers
The headers of the phishing emails showed that they came from a hacked site on the 47.49.12.164 (webserver2.ncswi.com) server. The name of the malicious mailer script is quite generic and can also be found in the headers—you can find some more tips on header analysis here:
X-PHP-Originating-Script: 48:mailer-1.php
We find many different mailer scripts with this name on compromised sites.
Hacking a site to send out email spam from its server is quite common. Hosting providers usually suspend such hacked sites because they don’t want their server IPs to make it into anti-spam blacklists. This highlights the importance of identifying and cleaning up a compromise before your site gets suspended by your host.
Precautions
Even if your site software is up to date and fully patched, hackers may still be able to break into it if you give them your credentials. Phishing attacks against common CMS’ often try to fool webmasters into opening a web page that resembles a standard login page and type their credentials there without verifying the address of the page.
In the case above, attackers used a mailer on a compromised website as a delivery mechanism to send their phishing email campaign and collect the credentials of other WordPress users.
Once an attacker obtains a website’s credentials through this campaign, they are then able to upload backdoors, deface the site content, or use the website to serve malware. This can lead to blacklisting and significantly impact your site’s traffic and reputation.
Phishing emails are easy to detect if you use common sense and follow a few simple rules::
- Never trust an email that asks you to perform an action that you didn’t request—especially if you haven’t received this type of email before
- Verify that the sender matches the content in the email
- Check the content for typos or poor formatting
- Inspect URLs for legitimate domain names
Mitigation for Sites Distributing Spam
Mailers are a category of scripts that bad actors install to distribute spam emails and phishing campaigns. These scripts abuse a server’s resources to send emails in large batches, can vary in levels of sophistication, and are found on roughly 19% of all compromised websites during clean up.
Simple mailing scripts can be identified if you scan files for mail() functions. More complex variations may use alternative functions and obfuscation, so it’s always a good idea to do a full malware scan if you suspect that your site is sending spam emails.
Integrity monitoring will also help find any new or modified files. Scanning for backdoors is also a good idea, as these are commonly installed to allow a bad actor to regain access to your site. You can follow our hacked guide for step-by-step instructions on how to remove unwanted malware and backdoors from your website.
If you believe that your website is distributing unwanted spam or phishing emails and you need a hand cleaning it up, we can help you get rid of malware and harden your website.










