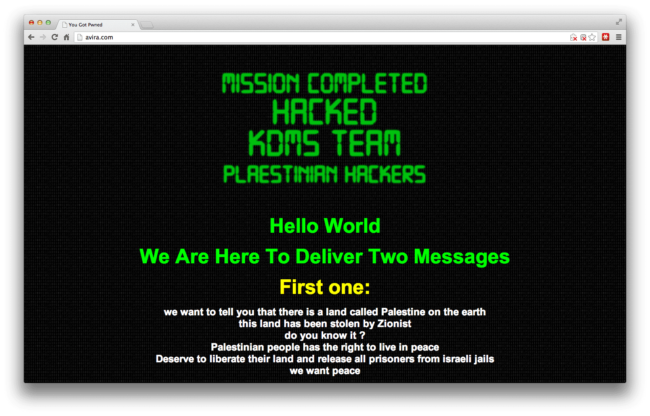
If you visited the web sites for Avira, AVG or WhatsApp this morning, you probably saw that they didn’t look like they should. All of them were defaced and looked like this:
It is a bit horrifying when you see such big sites, including security sites from major Anti Virus products (like AVG and Avira) getting compromised. But what really happened? Did they really get hacked?
DNS redirection
In a broader sense, they did get hacked, but not through a compromise on their servers or network. It looks like the attackers got access to their domains registration panels at Network Solutions and modified their name servers.
For example, these were the new name servers for Avira:
$ host -t NS avira.com
avira.com name server ns1.radioum.com.br.
avira.com name server n1.ezmail.com.br.
avira.com name server n2.ezmail.com.br.
avira.com name server ns2.radioum.com.br.
And these new names servers were pointing Avira’s IP address to 173.193.136.42, instead of the real IP address. That’s why visitors to the site were greeted with a defacement page.
What causes a bit of suspicion is that all these domains are hosted at Network Solutions, so we have to wait a bit more to see if it was caused by a breach on their end or something else.
Update: Avira posted the following on their tech blog: “It appears that our account used to manage the DNS records registered at Network Solutions has received a fake password-reset request which was honoured by the provider. Using the new credentials the cybercriminals have been able to change the entries to point to their DNS servers.” So it doesn’t looks like Netsol was directly hacked, but the attackers found a way to reset the passwords for certain accounts.









5 comments
Thanks for sharing what happened. The hackers as usual targeted the weakest chain in the link in these sites. Glad to know that it wasn’t the servers that got hacked. That would have made things worse for these companies.
This is another case of DNS hijacking similar to that of Australian IT services company Melbourne IT which, back in August, resulted in The New York Times and Twitter websites being hijacked. In both cases, although by the sound of it via different means, valid user login credentials
were obtained and used to change the nameserver records – yet another case of password authentication by itself not being good enough. We have supported two factor authentication for a while and each breach like this just strengthens the call for this to be implemented much more widely
Wow, that’s the unique tactic and very concerning they managed to reset the passwords as portraying themselves REAL ! They need to find out something like 2-factor authentication as @havenswifthosting:disqus suggested.
Thanks for sharing , I also faced the same problem with my sites which were hosted at myhosting.com , they didn’t hijacked my domain name servers but somehow they managed to change the index file of my site.
so the attacker send fake email to reset password for domain panel ?
then the email open new tab which fake login of domain panel ?
so i can say that these big site got hacked by fake login only ?
there is many big site got hacked by this technique.. but i really appreciated with this blog
Comments are closed.