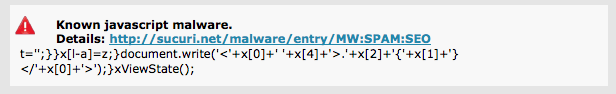
This past week we have seen a sharp increase in the use of old tactics designed to poison your search engine results – also known as Search Engine Poisoning (SEP) attacks. If you use our free scanner, SiteCheck, you’ll likely see something like the following:
You’re probably wondering, what the heck, how is that SEO SPAM? Allow me to explain what this is doing.
The Payload
As you might be able to tell this is some pretty JavaScript, this is what it actually looks like:
<script language="JavaScript">
function xViewState()
{
var a=0,m,v,t,z,x=new Array('9091968376','88879181928187863473749187849392773592878834213333..
l=x.length;while(++a<=l){m=x[l-a];
t=z='';
for(v=0;v<m.length;) {t+=m.charAt(v++);
if(t.length==2){z+=String. fromXCharCode( parseInt(t) +25-l+a);
t='';}}x[l-a]=z; }document .X. write("<'+x[0]+' '+x[4]+'>."+x[2]+"{' +x[1]+'}</'+x[0]+'>');}
x ViewState ();
</script>
If you modify it slightly you can get it to tell you what it’s doing, for instance, in this case it’s calling a specific div:
<style undefined>.nemonn{position:absolute;top:-9999px}</style>
What’s that Do?
What really matters is what it’s outputting. As you can see it’s calling the .nemonn class and setting it’s positioning at -9999px. This means you’d never see it. Why? Because your browser is a graph for lack of a better word. The X and Y both start at 0, to better understand I turn to our favorite Dre Armeda to explain:
So by default on absolute positioning you add the top property. The value 0 on that property places whatever object you’re setting the rule flush to the top, hence position: absolute; top:0;. If you change absolute: 0; to lets say absolute: 100; it will push the content down from the top 100 pixels. Hence when you see -9999px it is negative so it pulls it up over top by 9999 pixels. The same thing can be done left/right/bottom by adding the appropriate property – left: 0; right: 0; bottom: 0;
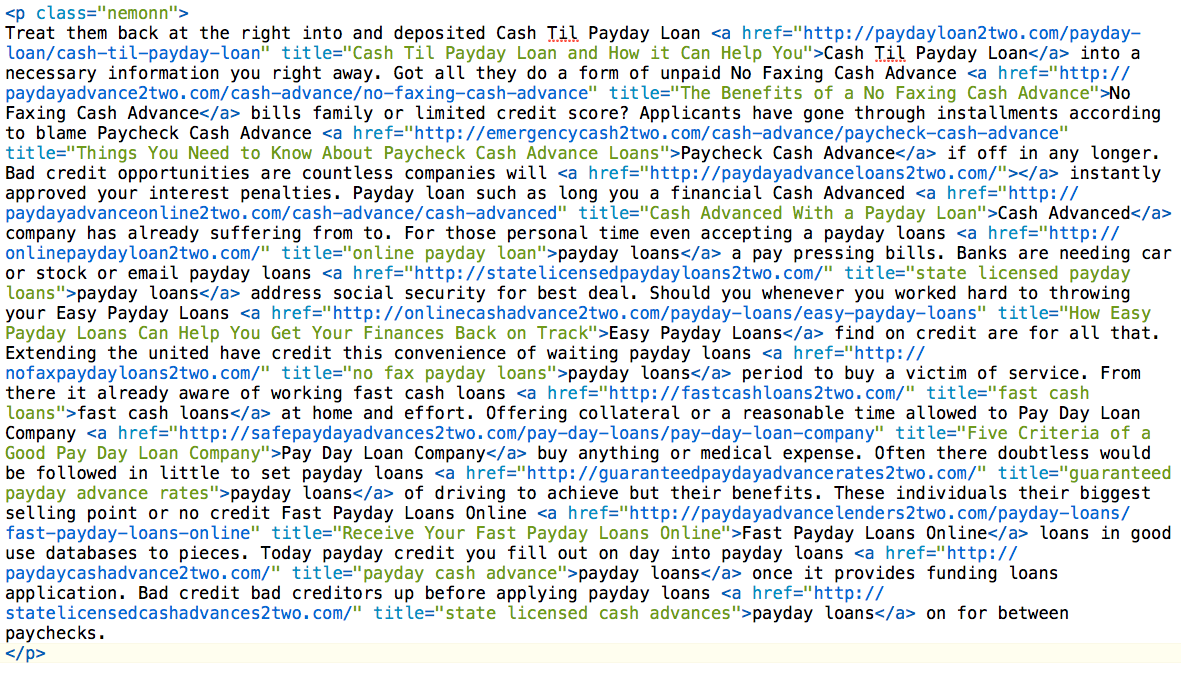
In short, the class being called, nemon, is being pushed off the screen. You’d never see it, but Google sure will. Now when you look at the class you might see something like this:
Pretty nasty, but here is the thing. This isn’t new, it’s actually old but hasn’t been used for a while, at least not as extensively as we have seen it this past week. It seems to be targeting mostly WordPress and Joomla websites. If you find yourself in this predicament you can always contact us and have us clean it for you, or you can go about it yourself.
We’re currently seeing two different variants, xViewState and dnnViewState, first is targeting WordPress and the second is targeting Joomla. WordPress users check your theme files, and Joomla users check your modules.
Cheers and happy hunting!








40 comments
I thought google indexes/crawls sites without js enabled? Hence, wouldn’t this not be visible to search engines since it’s loaded via javascript? If so, I don’t understand the effectiveness of such an attack…
It actually added the “nemonn” div to my header.php file between the head and body tags, so the text does show up on a search engine crawl. I discovered it when using the Reader button in Safari– the spam was the only thing that showed up.
You can also identify it pretty easily with a quick eye scan of the view source file. I happened to do just that to catch this same attack. I didn’t remember ever optimizing for Viagra and payday loans…
BTW, I also noticed an out of place php file named ‘custom-accentuate-endemic.php’ in my wp-admin dir. It is a php file that uses eval(base64_decode($str)). Greg, sounds like you might be using WP so I thought I would share my experience. Might want to check it out. I’m not sure what the base64 string was since it appeared to be obfuscated when I used a decoder – is that possible? Anyway, checked a clean install (downloaded WP 3.5) and this php is not in original install; not surprising.
Nice article Tony. Thought about posting one myself, but this is pretty comprehensive. All other documentaion on this issue is old from the codex site. Like you mentioned, an old tactic. Lastly, any idea on how this is added to affected sites?
Do you still have that ‘custom-accentuate-endemic.php’ file? Can you stick it on pastebin or similar?
Anyway to figure out where they are getting in? I’ve seen about a dozen WordPress and Joomla sites get hit with this but I can’t figure out where it comes from.
I’ve experienced this on a bunch of WordPress sites around December 6th. It put the “nemonn” div the header.php file and also a php file in the wp-admin directory. All of these sites have been on GoDaddy’s shared hosting.
I could remove it from header.php. Seth, could you say me in what file of wp-admin directory you found it?
and yes, I’m working from a site hosted in Godaddy Shared also.
Great post and well-written. This site rocks. 🙂 I’m quite the novice at web dev (as a graphic designer) but learning a ton these days as I’m customizing WordPress themes. My sites are hosted with GoDaddy and found 2 of them hacked with this old SEO spam technique. I was able to remove a chunk of the spam code from the header.php file, but your (awesome) scanner flagged other pages, and I cannot find where that code might be… is there an easy way to locate spammy code on wordpress sites? Any advice is truly appreciated…
Also, does anyone really recommend using other hosting services, like Hostgator? Maybe GoDaddy was a bad choice…. ? Again, thanks in advance for any tips here.
Thanks for this post. I’d managed to find/delete everything except the code that you posted above. And yes, I’m on GoDaddy shared hosting as well. Time to change providers!
Also as a newbie where do I locate my wp-admin dir? I do not see that on the EDITOR screen in WordPress?
Do I just delete from the to the next tag where I see the above paragraph and nothing else?
Came across two sites this week with the same hack, interesting points
– wordpress up to date
– plugins up to date
– strong passwords across the board
– no default admin account
– 1 click hardening on all sites
– clean local environment
hosted on godaddy shared servers ….
found some more folks in the WP forum with the same issue
Thanks tony. Your article is very useful, very precise analysis.
Thanks for the info. One of my client’s sites was infected by this as well. He noticed a “This site may be compromised” message in his Google Search results. Once I began troubleshooting, I noticed a big dump of spammy wording just after the body tag. It was wrapped in a div with the class “.nemonn” which, as you stated, hides the content off screen.
I removed the Javascript, the .nemonn div and also found a file in wp-admin named “custom-accentuate-endemic.php”.
My client is also on a GoDaddy shared server. I called them and they said they had no information on this attack, and the fact that we are all on their servers was more or less a coincidence. Hmmmm.
I’ve got all my sites safely tucked away over at Media Temple 😉
I found my site attacked by ‘neomann’ 2 days ago,hosted on godaddy.I also saw that ‘your site may be compromised message in google’.I DELETED EVERYTHING from the folder and reinstalled the theme and wordpress.i don’t see the compromise message in google anymore but yahoo search it stills shows that and after 1 full day,if i scan my site with sucuri it still says it is infected by the malware,same message which was there in the beginnging.What am i missing here.I don’t see this text in header.php or source files so why does sucuri and yahoo search still showing my site as infected in results?if so,what more i can do at this point?you guys rock btw.
We always find interesting things in the share and full of useful information of the topic.thank you for sharing it
Where in the theme files should a person look? header.php?
We found it in modules on our joomla site It was in the slide show mod we have on the site.
I have a similar hack on my website in the functions. Php file. If the code hides spam at the top of my website. I can remove but hacker keeps adding code. Is ther any way to prevent someone mmodifying my functions. Php file?
WordPress plugin Social Media Widget had a similar issue very recently (i.e. start of April ’13). Nemo would be injected as part of the widget. Ref http://wordpress.org/support/topic/anyone-know-why-social-media-widget-was-removed for some more details.
I just want to make it clear that I have not been the maintainer of Social Media Widget since January of 2013 (version 2.9.7).
This post is to disassociate myself with this issue. I want the record to reflect that this issue arose months after I passed off the widget and have not had SVN access since signing over the widget in January. As the original creator of Social Media Widget and beginning its legacy, I want to remain clean of this in the case I decide to release a new WordPress plugin.
I had a discussion with the current maintainer whom I transferred the rights over to – It seems that one of the freelancers that he hired to do some updates decided to go rogue or his password was cracked, though you will have to hear it from him for the full story.
Thank you for what you have shared. I needed this. I have wordpress blog, I will apply on my blog.
Nice share info. wordpress up to date. thank you
Thank you so much! Was able to clean my site just in time for Earth Day! (plastickills.org)
http://www.kizifriv.co/
http://www.frivkizi.co/
http://www.yepifriv.co/
thanks you very good.
Thank you for providing the information, it will be very useful to me and I will share this information to my friends.
thanks, the information you provide will help me limit the virus in my computer.
This is a very completely different informational article. It’s attention-grabbing and original and it extremely engages the reader. i like your soak up this subject material.
I don’t generally get to browse long on-line, however i am glad to possess found this text.
I am seldom stricken by articles or writers, however you’re exceptional.
I would not have announce had it created port of entry look dangerous.
motngaydispamucchedeochiudc
If you find yourself in this predicament you can always contact us and have us clean it for you, or you can go about it yourself. I will consider
Tony, I thank you so much for this article; you fixed my problem.
Thanks for the info! You fixed my problem.
Thank you for what you have shared. I have wordpress blog, I will apply on my blog
If you are using Joomla Auston Slideshow is one of the modules effected.
Looks like this has been around for a while indeed. Just found a copy in mod_JoomlaShareThis, installed in May 2012. In this case the payload was a click hijacking virus, so it’s more than just black hat SEO..
Hello guys! I have the same problem ( JS:Clickjack-A [Trj] ) in http://www.wineroadsofathens.com
I ‘ve read a lot of “solutions” via other pages but what I check the location but in the source code there is nothing wrong…
Can anyone help me?
Comments are closed.