Phishing attacks and campaigns have always been a hot topic in online security. With many posts tagged as “phishing” on our blog — the first one being over nine years old now — we’ve seen our fair share of phishing attempts.
In this post, we’ll cover the signs of a phishing attacks so you can recognize and avoid falling for them.
What is Phishing
A phishing attack happens when a malicious actor pretends to be someone else to gain privileged access or information. This can be in the form of a website, phone number, email, or even in person. If you’re not familiar with the concept of phishing, we have a post covering what is phishing.
Signs of a Phishing Attack
Phishing attacks come in all shapes and forms, and methods attackers use are always evolving. There are many common characteristics which are easy to recognize once you know what to look for.
Genuine-Looking but Odd Requests
Many phishing campaigns will use a recognizable company or branding that the victim is familiar with. This can be a financial institution, coworker, or website you know.
To do this, they will try spoofing their email or phone number, or use one which contains genuine-looking keywords via public emails.
Examples:
- security_bankname@gmail.com
- bankname@outlook.com
Both of these emails use public email registrars, which can create emails with any names for free.
- important@bankk.com
- account@baank.com
- website@securi.info
These emails use a similar domain name to the actual company, such as securi.info instead of sucuri.net. This is why it’s important to always double-check the domain to ensure it’s genuine.
Fast Action Required
To make the victims skip over details they would usually notice, the phishing attempt will add a sense of urgency to the message. Due to the severity or urgency of the request, you are more likely to immediately follow the links or open the attachment the attacker wants you to.
Examples:
- This offers expire in 1 hour!
- [Urgent] Malware on your website
- Your account is compromised
- Suspicious charges on your account
Odd-looking
This one will vary greatly depending on the goal of the attacker and knowledge they have about the victim, but the contact method will likely seem different from your usual communication.
When an attacker pretends to be your boss or coworker, they will most likely use a different writing style than your usual message:
- More or less typos
- More or less formal
- Missing or different signature
These are all signs that you should double-check with your contact to see if they sent the message, preferably with a communication channel you know is safe.
No Signs at All
The most important thing to keep in mind when thinking about phishing is that all attempts are different — and many targeted attacks are very advanced. They can hack or spoof your boss’s email, and then use the correct data to mislead you into thinking they are your target. If they request you visit a link or open an attachment, your best bet is to double-check via a different communication channel to make sure the request is genuine.
Phishing Campaign Examples
Here are some examples of phishing campaigns we have seen lately:
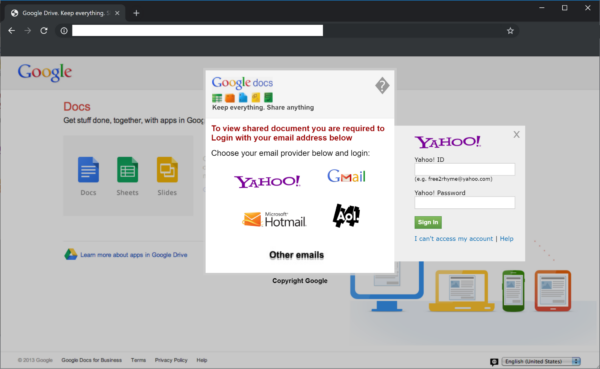
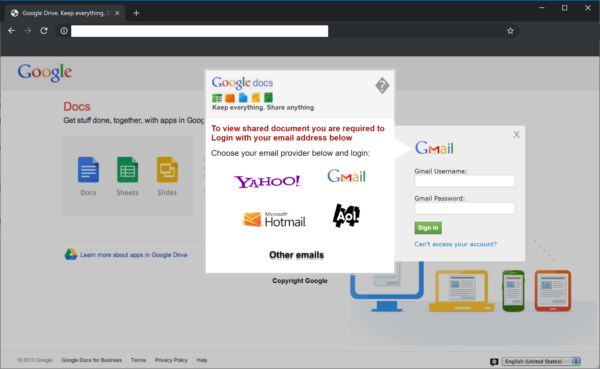
Google Drive Phishing Campaign
Notice how odd it is to be able to use any email provider to login to Google Drive:

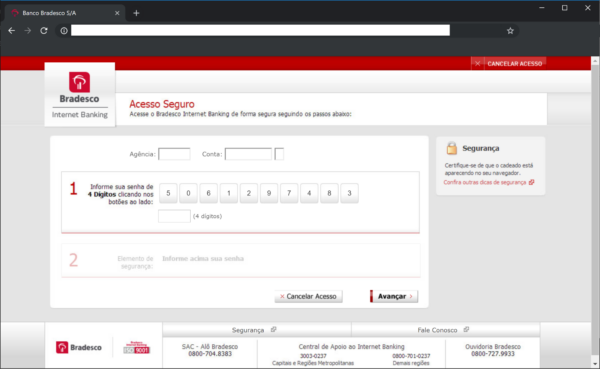
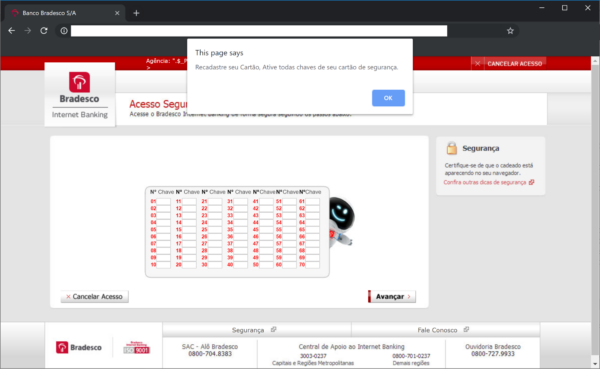
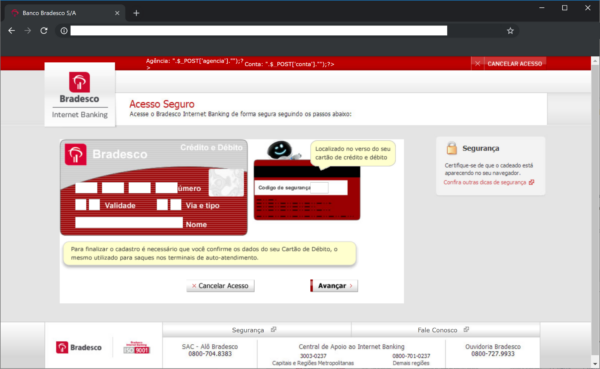
Bank Phishing Campaign in Brazil
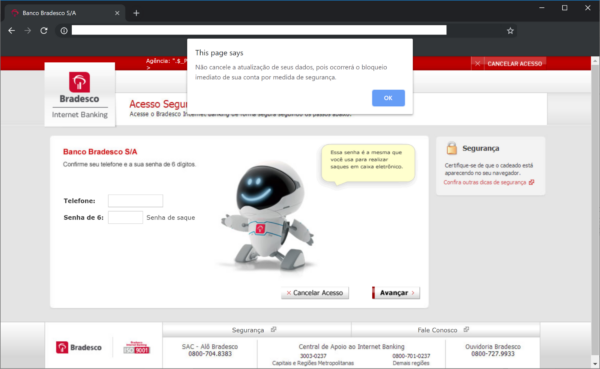
Notice how the phishing campaign asks for credit card information in the last image.
Conclusion
Now that you’re familiar with the concept of phishing campaigns, you can recognize the attacks and avoid falling for them! If you are looking to be up to date on the latest website attacks trends, subscribe to receive email updates.










