Nowadays, the term DDoS — or Distributed Denial of Service — raises the heart rate of most webmasters. Though many don’t know exactly what DDoSing is, they might be familiar with the effects of getting DDoSed: an extremely sluggish, dysfunctional, or entirely shut down website.
In this article, we’ll define DDoSing, discuss the most common symptoms, and detail how to tell if you’ve been DDoSed. We’ll also cover tips to spot denial-of-service and what you can do to protect your website from future DDoS attacks.
Contents:
- What is DDoSing?
- What services does DDoS target?
- Is DDoSing illegal?
- How to tell if you are being DDoSed
- Is it legitimate traffic or DDoSing?
- How does DDoSing work? (Live example)
- How to stop a DDoS attack
- What’s the impact of getting DDoSed?
- How do I protect my website from DDoS?
What is DDoSing?
DDoSing, or “Distributed Denial of Service,” is an aggressive form of cyber-attack where a network of ‘hijacked’ computers is used to flood a website’s server with traffic.
At a basic level, DDoS attacks are something like gridlock at a busy intersection — if enough traffic arrives all at once, then the heavy congestion turns into a jam and nobody can get through to the other side.
Here’s another analogy: Imagine you have a small store that can only fit 10 people at a time. Now imagine 100 people trying to get in all at once — it would be chaotic, right? But eventually, your store might even have to close down for a bit because there’s not enough resources for everyone. And that’s what DDoSing does to a website
What services does DDoS target?
DDoS attacks can target a wide range of services, including:
- websites
- game servers
- internet service providers (ISPs)
- the Nasdaq Stock Market
- a NASA probe
Practically anything connected to the internet is a potential target for DDoS.
The same goes for the source of DDoS attacks: Common culprits include hacked web servers and “internet of things” devices like smart appliances, routers, and even CCTV cameras.
Causes can be accidental or intentional. But a large criminal industry has grown around offering DDoS attacks as a service. There’s a market for attacks on sites, including competitors looking to tarnish others’ reputations and those denying online presence for political reasons.
Is DDoSing illegal?
Yes, DDoSing is illegal and many countries including the U.S. have strict laws against it. After all, it’s a form of online vandalism that can do serious harm to a website or online service. Not only does the act wreaks havoc on targeted sites, but it can also affect innocent computers that are ‘hijacked’ to support the attack.
How to tell if you’re being DDoSed
But how can you tell if your website is suddenly very popular or if it’s being DDoSed? Well, it can be tricky. Symptoms of a DDoS attack can mimic issues you might find on your computer — slow access to website files, inability to access websites, or even problems with internet connection.
However, there are a few main indicators that you might be facing a denial of service attack and leveraging website monitoring tools can help you spot them.
If you’re experiencing one or more of these ten symptoms, it’s a sign you might be getting DDoSed:
- A sudden influx of requests to a specific endpoint or page.
- A flood of traffic that originates from a single IP or range of IP addresses.
- A sudden spike of traffic that occurs at regular intervals or at unusual time frames.
- Problems accessing your website.
- Files load slowly or not at all.
- Slow or unresponsive servers, including “too many connections” error notices.
- A flood of traffic coming from a single device type, geolocation, or web browser version.
- 500 internal server errors status codes.
- 503 errors on your website.
- You receive a ransom or extortion demand from some attackers.
More specific DDoS symptoms will vary depending on the type of attack. But any large-scale or unexpected website latency issues mean it’s time to investigate.
Is it legitimate traffic or a DDoS attack?
Since a DDoS attack generates lots of traffic toward your site, it creates a tricky predicament. How can you tell if your site is just suddenly doing really well (traffic-wise) or if you are currently experiencing a DDoS attack?
If a site goes down due to a spike in legitimate traffic, then the time frame would generally only be for a short while until you’re back up and running again. Sustained spikes in traffic are rarely random, and you’d likely be able to identify reasons for it in legitimate cases. Say, a major advertising campaign or a piece of viral content. Checking the referer of the requests might confirm a legitimate reason for a spike in traffic (an influencer just tweeted some praise about your product?)
But more subtle attacks aren’t as simple to discern. Let’s say an online retailer with blackhat-hacking skills wants to keep people away from a competitor’s website without them being aware of it. The hacker can DDoS the competitor’s website a few times a day – potentially at random periods throughout the day just to make the competitor’s customers upset with how slow the website is. If the hacker’s server threw 500 hits per day (nothing out of the ordinary), the site wouldn’t be down for more than a few seconds, in intervals. Even mild DDoS attacks like this one hurt the victim’s business and reputation.
In some cases, you can examine potential DDoS attacks through a website monitoring tool. Try leveraging netstat to check entries and see if a specific traffic source continues to query a certain set of data long after the Time To Live (TTL) for the site has elapsed. (This is the time frame that you set for your site to discard held data and free up resources.) If that’s the case, you’re likely looking at a DDoS attack, since legitimate traffic won’t behave in this way.
How does DDoS work?
A DDoS attack simply works like this: An attacker uses a number of machines across the internet (or what’s called a “botnet”). Those machines send a high volume of fake traffic as requests to the target site, all in an attempt to overload server resources and bring the site down.
You can think of it like this: an attacker is like a puppet master, and the computers in the botnet are his marionettes. He pulls the strings, and they follow his commands, sending streams of meaningless traffic toward the target website.
There are many types and sizes of DDoS attacks and they can be devastating regardless of their size. Even an attack from a single system (DoS) can paralyze a site, so consider the ruthless efficiency of a multi-system attack through DDoS. A powerful DDoS can be as tiny as one request per second, and it can still have devastating effects on a website.
Some services are specifically targeted. Interestingly though, the process is largely automated, and most sites affected are randomly selected. Of course, this doesn’t matter if you’re a target. Regardless of the reason, the results can be detrimental, especially for an ecommerce website.
Live example of a site getting DDoSed
To give you an idea of what getting DDoSed looks like we documents a live example of a website getting DDoSed. You can watch how the server resources are depleted and how this disrupts the website’s performance in a matter of minutes.
After watching the video, you’ll be able to better recognize the signs of an attack on your own website.
If you want to know more about the types of distributed denial of service attacks, read our guide on what a DDoS attack is.
How to stop a DDoS attack
Here are five steps you can take to stop a DDoS attack on your site.
1. Identify the attack and monitor your website.
First, you need to be sure that what you’re dealing with is actually a DDoS attack. Unusually slow network performance, unavailability of a website, or a dramatic increase in the number of spam emails may be indicators. Keep an eye out for red flags, it’s usually better to be safe than sorry.
You can track your network activity carefully so you can recognize when anything is amiss. Regularly compare your baseline traffic to current volumes to help you identify traffic spikes and figure out if an attack is taking place.
Catching a DDoS attack early makes all the difference in reducing impact and downtime for your website. If you are running your own web servers, ensure you have services that can help you monitor when you are coming under DDoS attack.
2. Use a web application firewall.
Web application firewalls can help filter incoming traffic and drop traffic that appears to be part of a DDoS attack. It can also rate-limit traffic so that only a certain number of requests can come from a specific IP address during a specific time period.
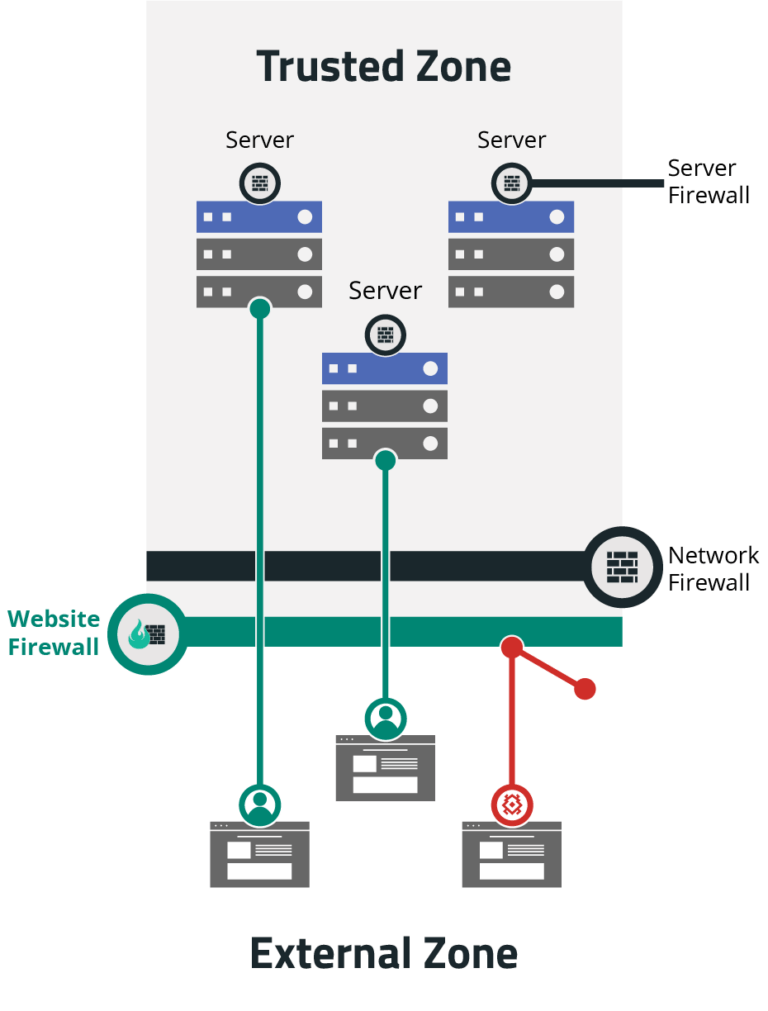
As an example, the DDoS mitigation feature of the Sucuri website firewall automatically blocks fake traffic and requests from malicious bots, without interfering with your legitimate traffic. Our cloud-based network can mitigate large network attacks (Layer 3 & 4), and we specialize in handling Layer 7 attacks against web applications.
Block off all unused ports and services; a webserver likely only needs port 80 and 443 open to the public. Furthermore, consider leveraging UFW for a very easy way to control access to ports on a Linux webserver.
3. Implement caching for your website.
Caching can help reduce the amount of traffic that needs to be handled by your web server. This allows you to store frequently accessed content in a temporary location like the web browser or dedicated servers, preventing your website from being overwhelmed by a large number of requests.
4. Leverage a CDN.
A content delivery network (CDN) can help distribute traffic across different servers to deliver content to your website visitors. This reduces the load on your own website’s server and prevents it from being overwhelmed, while ensuring it stays accessible to legitimate users.
5. Lean on a website security provider.
If you don’t want to deal with the challenge internally, you can partner with a DDoS protection service to help block and prevent denial of service attacks.
What happens as a result of a DDoS attack?
Since attacks can cause server outages, DDoS attacks can place significant stress on dev or IT resources trying to bring the website back online. Even worse, they can severely disrupt your website traffic, user experience, and ultimately the purchase process. That can mean lost revenue for a website due to downtime and technical issues.
For example, an attack on an e-commerce business during the busy holiday shopping season can impact the entire company’s profitability for the year.
In the end, the cost of protecting yourself against a DDoS attack is usually much smaller than the financial impact of a DDoS against your site (or any other hacking attempt).
How do I protect my site after getting DDoSed?
While distributed denial of service attacks may be common, it doesn’t mean you need to accept it as a part of your site’s online presence.
Limiting the number of requests your web server accepts over time is one way of mitigating DDoS attacks. Unfortunately, rate limiting is often not sufficient at effectively handling complex attacks.
Using a web application firewall, however, can significantly help mitigate a layer 7 DDoS attack. Since the firewall filters traffic between the internet and the origin server, it can act as a reverse proxy and protect the website from malicious traffic.
The Sucuri Web Application Firewall leverages an Anycast distributed network, which scatters traffic across a number of distributed servers. Since this approach is effective at diffusing disruptions and helps large volumes of traffic become more manageable, websites can take advantage of this service to further reduce the impact of an attack.
When it comes to attacks against your website or livelihood, it’s always better to take a proactive approach than reactive one.











