Phishing is a serious threat to any industry. We have seen this topic appear in the news more each day. You might have already received a fraudulent email from what seemed to be your bank or even seen the hacking that took place during the 2016 US presidential election. But what do you know about phishing?
What is Phishing?
Phishing is the fraudulent attempt to obtain sensitive information like login information or other personal identification information (PII), which is any data that could potentially identify a specific individual, such as:
- usernames,
- passwords,
- credit card details,
- SSN (Social Security Number),
- bank account information,
- email,
- phone number,
- secret question answers
Even partial information can increase the chances of success to subsequent social engineering attacks.
In a phishing attack, something lures the victim pretending to be a trustworthy entity, such as:
- banks
- electronic communicators
- internet providers
- retail companies
- shops and others
In recent years, attackers have expanded beyond email into messaging apps like WhatsApp, Slack, Microsoft Teams, and even video conferencing invites, where phishing links are embedded directly into chat or calendar events.
Types of Phishing
Phishing attempts happen in many ways.
Deceptive Email Campaigns
Email phishing is a term used in technology to refer to the fraudulent practice of sending emails apparently from a known or trusted sender with the objective of inducing victims to reveal confidential information.
Phishing can be a targeted act or not. We can assume that pretty much everybody has already received a phishing scam via email. Nowadays, it is easier for us not to notice these emails since the anti-spam technology has evolved. Most of these messages are blocked from ever reaching our inboxes.
In September, we showed a phishing campaign which informed WordPress site owners that their database required an update.
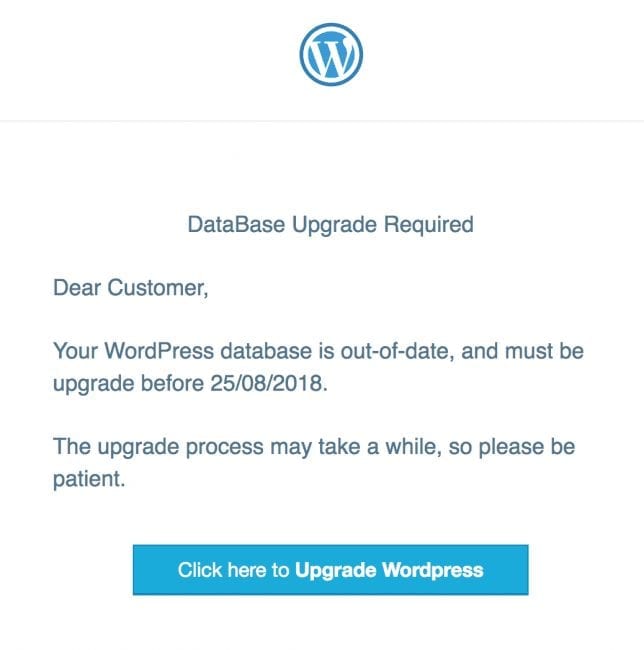
The phishing page was created on a hacked legitimate WordPress website. When clicking on the “Upgrade” button, a fake WordPress login page opens to collect the user credentials.
As part of email phishing, fake website pages are designed to look and sound authentic. Phish emails usually say that you need to provide/verify/view something urgently and they provide you with a link. This link then leads you to the fake web pages.
Without these emails, there would not be many visitors for the phishing pages with the exception of phishing messages in social networks and SMS.
Carefully crafted phishing login pages convince users they are logging into a valid service. When users fail to notice the login page is fake, attackers receive their login details or credit card information. The stolen credentials and personal information are then used to perform identity theft and fraudulent activities.
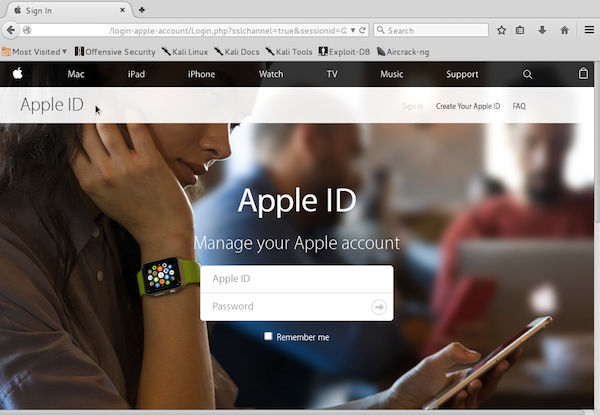
Here is an example of a fake page we found on a compromised website during an incident response. We identified a phishing directory called “login-apple-account” on a customers website. When accessing the path via HTTP, users were led to a very convincing spoof of the Apple ID website:
Phishing in Google Docs
Phishing campaigns in Google Docs are a part of phishing email campaigns when hackers add malicious links to online documents.
It’s quite common to share Google Docs documents, so many people assume it is normal for an organization to share them via Google Drive. When people click on Google Drive phishing links, they see something like this:
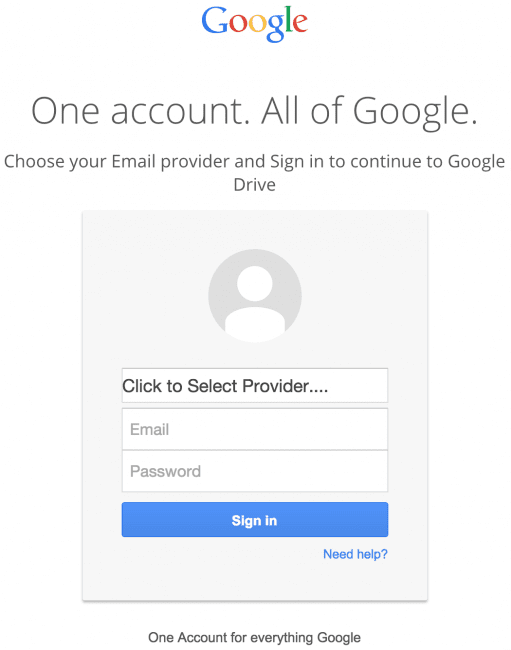
In this example, the address bar contains a fraudulent URL. However, not everybody pays attention to it and subsequently fall victim to such scams.
Attackers have increasingly leveraged collaboration tools such as Google Workspace, Microsoft 365, and Dropbox for phishing. Attackers exploit “Share” notifications that look official, tricking users into clicking malicious documents. Cloud service impersonation remains one of the fastest growing phishing vectors.
Spear Phishing
In most types of phishing attacks, the targets are a wide group of people, for example, Google Docs users. However, in spear phishing attacks, the targets are specific individuals.
Highly targeted attacks are much less common than the other types of mass phishing attacks that we have already discussed, but they do occur.
Malicious actors can look up their victims on websites or even social media platforms, such as Facebook or Instagram, in order to craft a customized scam that can look legitimate.
Spear phishing attempts can be found via email or e-banking targeting a specific victim to read the communication (espionage) or are to steal a significant amount of money.
These attacks can target intermediary victims. Someone who has some sort of access to the real intended victim (e.g. secretary, accountant, etc.) to use their account against more important people within the organization or to infect their computer with malware to access the organization’s internal network.
More recently, artificial intelligence has amplified spear phishing. AI-powered tools can generate personalized, grammatically perfect phishing emails in seconds, making them much harder to spot. Attackers can even mimic a victim’s writing style using AI, increasing trust and success rates.
Preventive Measures
Phishing attacks are widespread and with the holidays so close these malicious practices become even more common.
You should always pay attention to details when entering credentials anywhere on the web. Here are some red flags:
- Suspicious URLs,
- Lack of HTTPS,
- Weird wording,
- Typos,
- Unknown email senders
Use 2FA whenever possible. If criminals steal your credentials, they will still not be able to use them without the second authentication means (SMS, Authentication app, hardware token, etc.).
Phishing is usually hard to detect because the malicious pages are created deep inside the directory structure. People don’t normally check those directories and unless you know the exact URL of the phishing page, you would never know your site is hacked.
As a webmaster, it is advisable to have an account in Google Search Console to notify you about security problems, including phishing.
Best practices include:
- Adopting passkeys and passwordless authentication to reduce reliance on traditional credentials.
- Training employees regularly with phishing simulations to increase awareness.
- Using advanced email security gateways that apply AI/ML to detect suspicious content and sender behavior.
- Deploying zero-trust principles across corporate systems, assuming no communication is inherently safe.
- Monitoring dark web activity to identify if your credentials have been leaked after a breach.
Website owners can also use specialized sites like PhishTank.com and VirusTotal.com to figure out if their site hosts phishing pages. Sucuri also monitors databases of 10 security providers and will notify our customers if any of them detect problems with their websites. Most phishing pages are actually placed on hacked sites. If you are not sure your website has been hacked, we can help you.










