A lot of attention is being applied to passwords lately, and rightfully so.
Most everyone is trying to understand how easy or hard reverse engineering passwords is, and how to better grasp the role it plays in today’s compromises. What is being realized is that it plays an instrumental role, and ranks easily among the top 5 reasons why web applications are compromised.
The Dilemma
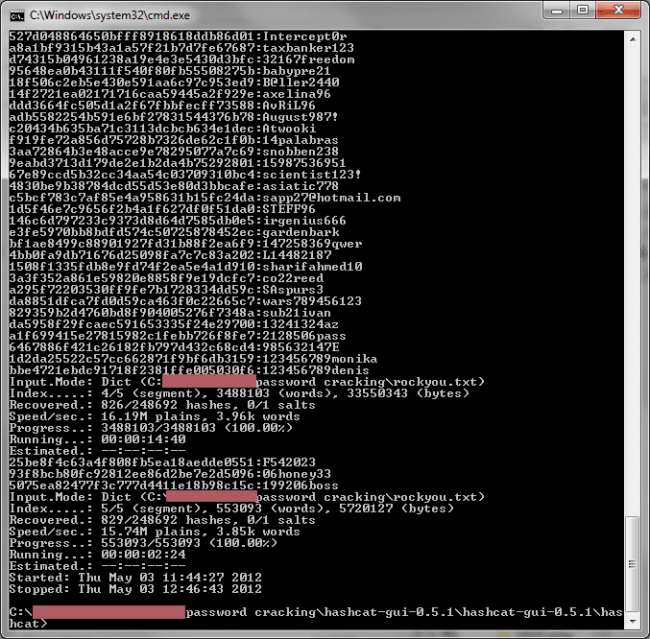
If you’re looking to better understand the process of cracking and reverse engineering of passwords, ArsTechnica put together a phenomenal post clearly describing and illustrating the process, entitled Why passwords have never been weaker – and crackers have never been stronger.
In it they describe the various methods used to both perform brute force attempts and dictionary attacks. What they highlight is the role that technology is playing. It’s what is making crackers so strong and they highlight that the weakness with passwords comes from us – human generated passwords.
Here is an image they shared of a few cracked hashes:
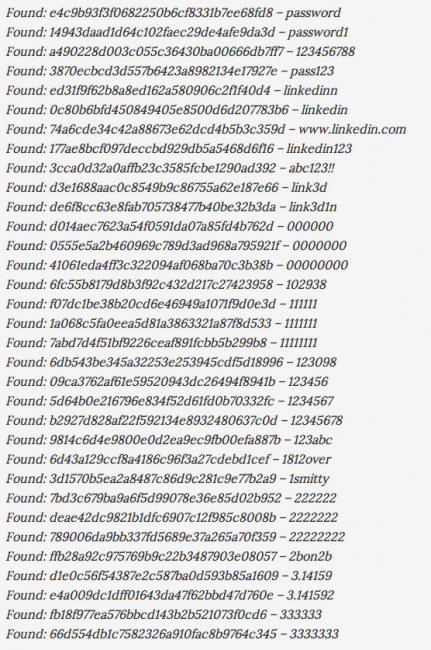
Here is a list we shared back when we confirmed the LinkedIn compromise:
What most don’t realize is that after each compromise, whether LinkedIn, Last.FM, eHarmony, Gawker, etc… the word lists floating through the underbelly of the internet increases, and the odds of your password being captured increases.
Contrary to popular belief, crackers are highly intelligent and like most users, realize that most users will substitute “a” for “@“, or “E” with “3” and so on. These are futile attempts at hardening and introducing a complex password. In fact, the other biggest challenge folks have is the uniqueness of the passwords.
Our founder, Daniel Cid, put out a good post back in 2011 about what a good password consists of.
Forgive the lack of styling, he doesn’t exactly believe in anything that is not in plain text format on the web.
In it, he places emphasis on the uniqueness of passwords, and how it’s not something that is discussed much.The more a password is used – regardless of whether it is 40 characters, randomly generated, or leverages special characters – the less secure it becomes. ArsTechnica’s article talks to the point directly here:
The average Web user maintains 25 separate accounts but uses just 6.5 passwords to protect them, according to a landmark study (PDF) from 2007. As the Gawker breach demonstrated, such password reuse, combined with the frequent use of e-mail addresses as user names, means that once hackers have plucked login credentials from one site, they often have the means to compromise dozens of other accounts, too.
More important is what they describe here, which talks to how those supposedly secure and irreversible hashes are cracked:
In theory, once a string has been converted into a hash value, it’s impossible to revert it to plaintext using cryptographic means. Password cracking, then, is the practice of running plaintext guesses through the same cryptographic function used to generate a compromised hash. When the two hash values match, the password has been identified.
In the various white and black hat communities this is nothing new, but they’re right that in the past 5 years the evolution of cracking has exploded. Not just because of these processes, but because of the technology that allows these processes to be implemented.
This builds on my point earlier. Every time a compromise occurs be worried, be very worried. Those lists start making their rounds faster than a brush fire kicks off here in Southern California. This is because these real-world lists are priceless; they cut the cracking time into a fraction of the time otherwise required. They are so valuable because the odds of the human-generated password being used by other humans who fancy themselves unique is very high.
We are creatures of habit.
Not only does it decrease the time to crack hashed passwords, but it also increases the odds of brute-forcing their way into your website, financial institution, email, social network, etc… and causing irreversible damage to your online presence.
The Advice
Here is the normal stuff you’ll likely be told and things that should be a staple in every password discussion at a minimum:
- Include uppercase and lowercase
- Include special characters
- Use numbers
- Longer than 10 characters
- Passphrases are your friend
- Don’t reuse passwords
And of course the common mistakes:
- No dates
- No names
- No places
- No pets
- No reusing passwords
But that is all basic. You really need to become more proactive and take a better stance with your passwords.
In fact, human-generated passwords should cease to exist all together and the emphasis should be on the following:
- Use a password manager
- Group your passwords
- Use a generator
- Write down your master passwords
- Don’t reuse
Password Manager
Stop coming up with excuses and being lazy, it’s time to start using a password manager. I personally use and recommend two: Lastpass and 1Password. I have even written posts on my personal blogs talking to password management and the security methods used by LastPass that might prove of value to some.
Do understand that LastPass has had security issues in the past, case in point is when they forced all their users to reset their master passwords in May of 2011. But then again, so has KeePass, as early as a few months ago. This should not be a deterrent to using a password manager, it’s nothing more than a reality that we must live with.
On a side note, I can attest that this can be a painful process. I have been undergoing it for the past 4 months. It’s amazing the number of accounts you forget you have, and just this weekend I had to check my bank account but found myself too lazy to log into my password manager. But being that I was in a public location, is that really a bad thing?
Group Your Passwords
Here is a really good idea, group them so that they are a bit more manageable. You can group by anything, see below:
- Important – e.g., financial institution, infrastructure access, email, master accounts
- Medium – e.g., social networks, websites, forums
- Low – e.g., fake accounts, alias accounts, gaming accounts
This then allows you to categorize and create your own rules, something like this:
- Important – no less than 12 characters, use special characters, random generator
- Medium – no less than 8 characters, case, random generator
- Low – no less than 8 characters, human-generated passes are fine, quick access need
Be sure to give your groups serious thought. Something you think is low, might in fact be high.
For example, think of your Amazon account. Some might think it’s low, but is it? I’d say it’s a medium at minimum. If you log in, you’re likely to quickly gain access to the user’s profile information. That can be used to ascertain all kinds of personal information – things like your billing address, phone number, credit card info. So, is it really low? Those snippets of information can become very dangerous.
These things would be of concern to me and would cause me to run on the side of caution.
Use a Generator
In addition to using a password manager, use a password generator. There are a few you can use online, as well commands you can run locally if needed, but I find it most convenient to leverage the generators provided by my password managers.
When possible just be sure to follow these guidelines:
- Be sure not to use the same randomly generated password on multiple sites
- When possible try to include special characters, but note that not all logins allow this
- They should be no less than 8 characters, but I aim for no less than 10 – 15 characters
Write it Down
Lastly, write it down. Some may contest this idea, but I feel it’s effective.
Most password generators you’re looking at one, possibly two, master passwords. Write them down, put them on a piece of paper and store it in a safe place. Get it off your digital media.
With enough time anything can be cracked.
You do need to be smart about this though. If you write it down and paste it to your cubicle wall or put it up in your office where everyone can see it, it’s useless. There are still threats with your colleagues that you have to consider.
You don’t need to be scared of technology, but you do need to respect it.
Common Mistakes:
- Paste it to your keyboard
- Paste it under your computer
- Put a post-it on your monitor
- Tape it under your phone or in the drawer with all your pens
Again, be smart about what you do with that piece of paper.
Don’t Reuse
Now, I’d be lying if I said I didn’t fall susceptible to this from time to time: “Let me add a real quick pass to get in and out and I’ll change it later.” So what do you do? You reuse your favorite P@ssw0rd.
It happens, but do your best to go back and update, or better yet, try to avoid it all together. Uniqueness is the key. The less you use it, the better it serves you.
To The Pundits
The obvious argument that most will make with this advice is well, there is always the odds of getting the same pair.
Sure, it’s feasible so let’s look at that.
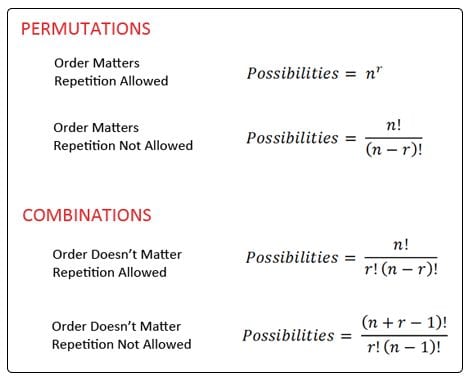
I was intent on finding this awesome article appropriately titled Permutations and Combinations. This allows us to objectively look at the number of possible variations based on number of characters, which can calculate the odds:
To the rest of us, here is a better way to read this:
- 6 letters – 308,915,776 options
- 8 letters – 208,827,064,576 options
- 8 letters with uppercase – 53,459,728,531,456 options
- 8 letters with characters too – 6,095,689,385,410,816 options
In short, I like my odds.. 🙂
If you have any questions please let us know by leaving a comment or sending us a note here info@sucuri.net.







7 comments
Well done, Tony.
I appreciate the part where you get into sharing how long it might take a hacker to crack the password given the complexity.
http://www.dynamicnet.net/2012/03/weak-passwords-open-doors/ is our take tied with using a password keeper.
Thank you.
we are asked to find the key. im finding it hard guessing it. the only clue given is that the key is complex and should not be used as password. can you help me find out what it is?
Comments are closed.