For some while we have wondered what happens when a plugin is removed from the official WordPress plugin directory for security reasons. Historically, we haven’t seen much of anything happen – no notification to users, no official blog post, nothing beyond the plugin disappearing from the repo. Sometimes when it did disappear, my understanding is updates were forced – certainly for the major vulnerabilities.
In an interesting move, it looks like some experimental changes have been made to help ensure users quickly learn there is a security problem.
Plugin Directory Message
We wrote a post this week bringing some attention to the spammy actions of a website named WPStats.org and their fake Advanced Search Plugin. As of this morning, when trying to access the Advanced Search plugin page in the WordPress plugin directory you get the following message:
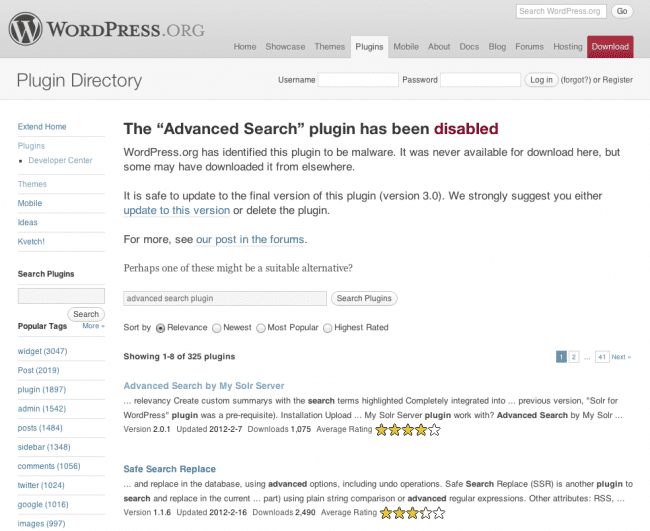
In the message they have officially stated that the plugin was never in the repository, we stand corrected! Here is a quote from the official response:
We rejected the plugin when it was submitted to the WordPress.org plugin directory. However, it seems the same code was offered for download elsewhere, which has resulted in sites infected with spam.
A warning was added to the Advanced Search plugin page along with a link to a clean version of the plugin.
The cool take away here is that this can be done for any plugin that’s in the directory. It could offer a mechanism for users to take action if a vulnerability is discovered.
We often talk about community efforts, I think this could be very helpful, and it’s great to see it coming from WordPress.org.
Plugin Updates
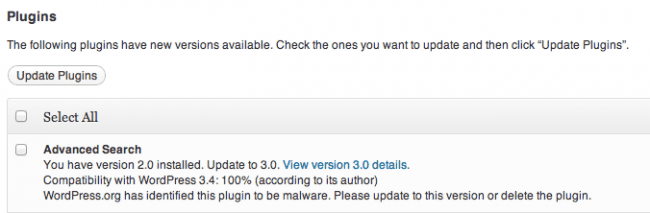
Another process coming to life looks to be removal of offending plugins. Below is the process that will occur when a plugin is deemed unsafe and may cause harm to your site and visitors:
1. Plugin Review
Plugin is reviewed and deemed unsafe – critical vulnerabilities where the author is not responsive, or malicious plugins. Vulnerabilities that are or can be actively exploited. This starts the process.
2. Notification Process
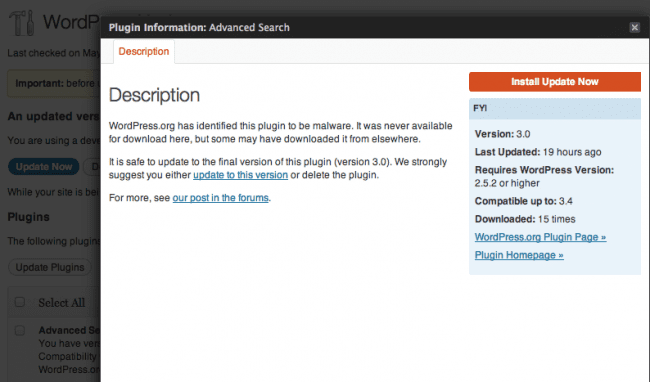
On WordPress.org, the code is blanked out, a message is added, and a new update is forced. WordPress dashboards are notified of an available update.
3. Plugin Updates
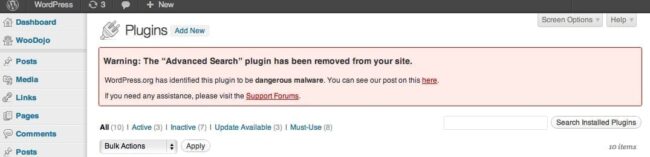
Upon updating, the code from the offending plugin is then blanked out from the WordPress installation.
If the plugin is readded to the website, the update message will reappear and then deactivate itself.
In the end, it looks like WordPress is experimenting with ways to take a stronger stance on offending code trying to infiltrate self installed instances of WordPress. It truly is a team effort, and it’s great to see them thinking through viable options to responsibly approaching security.
What’s your take? Let us know your thoughts on the new alerting and removal process that looks to be live as of today.










5 comments
If dodgy plugins are flagged up in the dashboard of a WordPress site via a notification there, then that is set to be a massive help in preventing hacked sites. I’d say most people – myself included – wouldn’t think to check the WordPress plugin directory for a particular plugin by name unless reinstalling that plugin for another site, so if the warning was shown there alone, that would leave a lot of plugin users in the dark about any discovered vulnerabilities. On another note, I want to thank you for your tool that scans a site for malware. We recommend it or use it as a first step for all any new clients who come to us for help fixing a hacked website.
Comments are closed.